In the realm of cryptography, the quest for a perfectly secure encryption mechanism has long been a subject of fervent inquiry. Among the plethora of cryptographic systems, the Caesar cipher emerges as a rudimentary yet historically significant method. This analysis seeks to dissect the assertion that the Caesar cipher is perfectly secret while elucidating its operational mechanics and vulnerabilities.
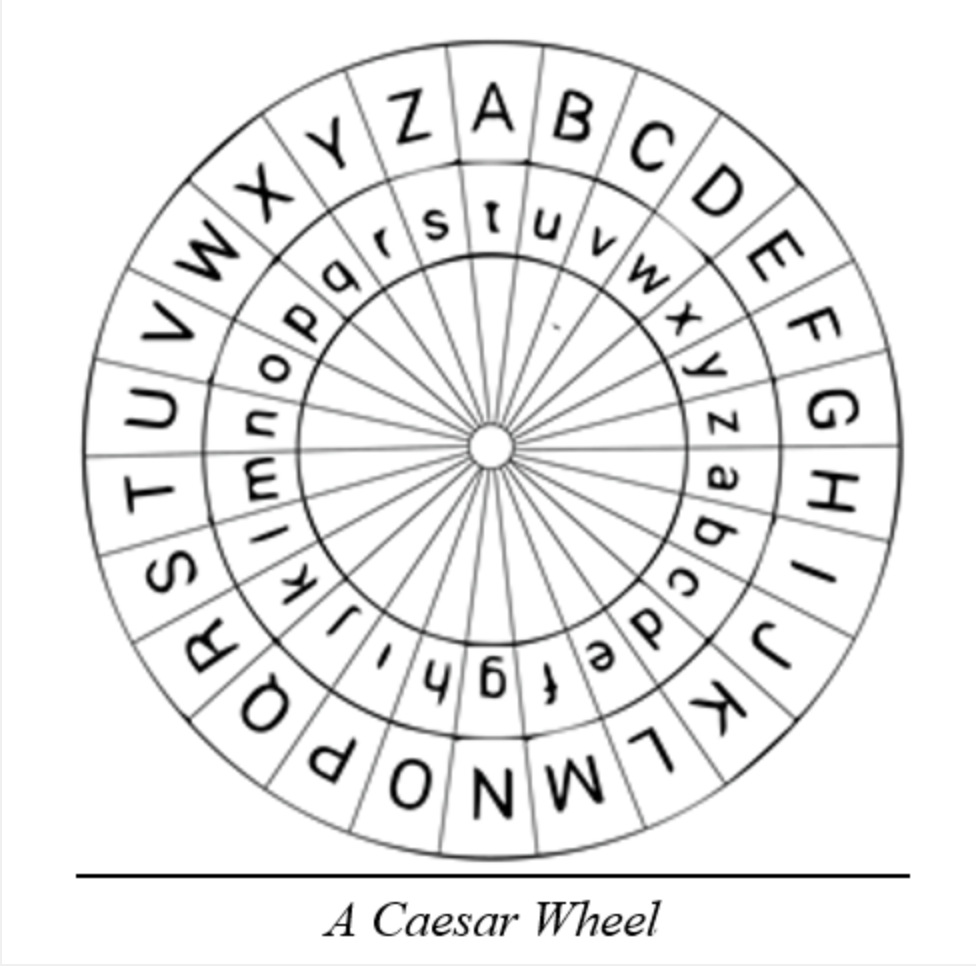
The Caesar cipher, named after Julius Caesar, who reportedly used it to communicate with his generals, is a substitution cipher. It operates by shifting each letter in the plaintext by a fixed number of places down or up the alphabet. For instance, with a shift of three, ‘A’ becomes ‘D’, ‘B’ morphs into ‘E’, and so forth. The simplicity of this technique underlies both its charm and its intrinsic frailty.
Defining perfect secrecy is paramount in this investigation. According to information theory, a cipher achieves perfect secrecy if the ciphertext reveals no information about the plaintext. This is epitomized by the one-time pad, a theoretically unbreakable system that utilizes a random key at least as long as the message itself. Consequently, any assessment of the Caesar cipher’s secrecy must weigh its limitations against this standard.
The cardinal flaw in the Caesar cipher arises from its deterministic nature. With only 25 possible shifts (noting that a shift by 26 returns the original text), an attacker can easily employ a brute force attack, testing every conceivable shift until the plaintext is discerned. This vulnerability becomes increasingly pronounced as the potential plaintexts diminish in length, allowing for frequency analysis to expedite the decryption process.
Frequency analysis is the crux of the Caesar cipher’s demise. Each letter in the English alphabet occurs with varying frequency. For instance, ‘E’ typically appears most frequently, followed by ‘T’, ‘A’, and others. A ciphered message preserves these frequency patterns, allowing a determined cryptanalyst to correlate the frequency of characters in the ciphertext with their standard occurrences in the English language. Thus, even a brief ciphered message can be decrypted without comprehensive knowledge of the key utilized.
Consider a scenario where one encounters the ciphertext “KHOOR”. Analysis could begin by examining recurring letter patterns or frequencies that would suggest which shift has been applied. A pattern of ‘K’, ‘H’, ‘O’, ‘R’ could be matched against known English structures. It is reasonable to surmise that with a modicum of effort, the original message could rend itself from its seemingly cryptic exterior.
Furthermore, the Caesar cipher lacks what cryptographers refer to as diffusion. In modern cryptographic designs, altering even a single character in the plaintext should, ideally, result in extensive and unpredictable changes in the ciphertext. The Caesar cipher, with its linear transformation, fails to meet this criterion. A change in the input leads to a corresponding, easily predictable change in the output, compounding its vulnerability from a cryptographic standpoint.
Moreover, the static nature of the shift creates an additional layer of susceptibility. If an adversary surmises the shift used, they can decipher messages effortlessly. This predictability starkly contrasts with the complexities of contemporary cryptosystems which frequently employ rotating keys and complex algorithms that obfuscate the relationship between plaintext and ciphertext.
Curtailing the argument that the Caesar cipher might exhibit aspects of perfect secrecy requires consideration of context. In environments devoid of cryptographic literacy or threats, the Caesar cipher may provide a semblance of security. For instance, it could serve as a basic tool for encoding messages among children or for introductory educational purposes concerning cryptography. However, its application in serious communication remains exceedingly imprudent within the modern landscape of information security.
In contrast, a discussion on the educational merits of the Caesar cipher cannot be overlooked. It serves as a poignant introduction to fundamental concepts within cryptography, inspiring curiosity about more robust systems. By exploring its weaknesses, students can grasp the importance of advanced cryptographic constructs that utilize keys, complexity, and sophisticated algorithms designed to thwart unauthorized access.
The debate surrounding the Caesar cipher’s status as a perfectly secret system ultimately affirms its significant limitations. While it may innocuously introduce the rudiments of encryption, the absence of true secrecy renders it obsolete for any genuine protective use. In the grand tapestry of cryptography, the Caesar cipher stands as a relic: a historical artifact reflecting humanity’s early endeavors in safeguarding communication, yet failing to align with the sophistication demanded by contemporary digital interactions.
In conclusion, upon rigorous analysis, it becomes abundantly clear that the Caesar cipher does not espouse the qualities of a perfectly secret cipher. Its simplicity, predictable outcomes, and vulnerabilities to elementary attack tactics compromise its integrity. To advance in the age of information, cryptography necessitates innovation that transcends the limitations exemplified by such rudimentary techniques. In the face of ever-evolving threats, the pursuit of true secrecy remains a tantalizing, albeit elusive, ideal.







Leave a Comment