In today’s digital age, the need for robust security measures is more pressing than ever. As we navigate through a labyrinth of online exchanges, the terminologies surrounding data protection can often become conflated and confusing. Two such terms that frequently arise in discussions around data security are ‘encryption key’ and ‘password.’ Although often used interchangeably in casual conversations, they serve distinct functions within the realm of cybersecurity. Understanding the differences between these two concepts is crucial for anyone aiming to safeguard sensitive information.
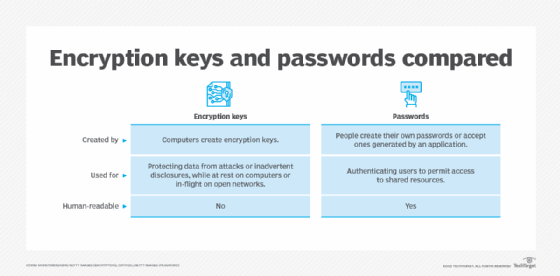
At its core, a password is a string of characters, typically created by the user, that serves as a means of authentication. It allows access to personal accounts, systems, or data. The integrity of a password lies in the user’s ability to keep it confidential. In a world teeming with cyber threats, the importance of strong, unique passwords cannot be overstated. Authentication mechanisms that rely solely on passwords can be vulnerable to various attacks—including brute-force attacks, phishing scams, and social engineering tactics.
On the other hand, an encryption key is fundamentally different in nature and purpose. It is a piece of information, usually a long string of characters, used in conjunction with an algorithm to transform plaintext into ciphertext, rendering it unreadable without the appropriate decryption key. The essence of encryption is to safeguard information; therefore, the encryption key is intrinsic to the process of encoding and decoding that information. While the strength of a password can often hinge on a user’s creativity and memory, encryption keys typically rely on computational complexity, making them far less predictable.
One of the most glaring distinctions between encryption keys and passwords lies in their application. A password is utilized for user authentication, establishing a user’s identity to grant access to specific resources. Conversely, encryption keys are employed in the encryption and decryption processes of data. In simpler terms, passwords serve as gateways, while encryption keys serve as locks and unlock mechanisms inherent to data protection protocols.
The lifespan of these two forms of security is also markedly different. Passwords usually have a defined lifespan where they are routinely updated to enhance security. Users are often encouraged to change their passwords periodically to mitigate the risk of unauthorized access. In contrast, encryption keys can often remain static for extended periods—unless the underlying encryption algorithm or security policy necessitates a key rotation. This factor can lead to a false sense of security, as many may mistakenly believe that once their data is encrypted, it is impervious to all threats.
Another point of consideration is the complexity involved in managing passwords and encryption keys. The average user may find it relatively straightforward to create and store passwords using various password management tools. However, encryption keys necessitate a higher level of technical acumen. They often require explicit management protocols and secure environments for their generation, storage, and distribution, especially in organizational contexts where data security is paramount. Mismanagement of encryption keys can result in data breaches—a failure with far-reaching consequences.
Despite their differences, it’s essential to recognize the intersection between encryption keys and passwords. Many modern applications employ a combination of both to enhance security. For example, password-based key derivation functions (PBKDFs) utilize a user-created password to generate an encryption key. This dual-layered approach enhances security by ensuring that even if a password is compromised, without access to the original password, the encryption key—and therefore the encrypted data—remains secure.
Moreover, in the realm of advanced cryptography, new methodologies have emerged, such as keyless encryption, which eliminates the reliance on traditional passwords altogether. These innovations are designed to mitigate vulnerabilities associated with human-generated passwords. Discussions about the future of digital security often revolve around these advancements, promising novel mechanisms that harness the capabilities of encryption while reducing the risk paradigm that comes with password usage.
As we interrogate the relationship between encryption keys and passwords, it becomes apparent that both are integral components of a comprehensive cybersecurity strategy. While they serve distinct functions, the convergence of these elements can provide a formidable defense against the ever-increasing tide of cyber threats. Grasping the nuances of how these security measures complement one another will not only bolster individual data security but also enable organizations to develop more resilient systems.
In conclusion, understanding that an encryption key is not synonymous with a password illuminates the broader discourse about cybersecurity. The promise of advancement in cryptographic techniques suggests a shift in perspective—a move towards a digital ecosystem where protection transcends simple authentication measures. As technology continues to evolve, so too must our understanding and implementation of security mechanisms. Curiosity about these elements can lead to improved practices, safeguarding our digital lives in an increasingly complex environment.







Leave a Comment