The concept of a Virtual Private Network, or VPN, is often wrapped in a shroud of mystique and confusion, particularly when juxtaposed against the phenomenon of Man-in-the-Middle (MITM) attacks. The very nomenclature—*Man-in-the-Middle*—evokes images of malevolent entities intercepting communications for nefarious purposes. Meanwhile, a VPN is heralded as a beacon of security in the digital age. Yet, the question remains: Is a VPN a type of MITM attack? This inquiry invites a deeper exploration of the intricate dynamics between these two cybersecurity aspects.
At the core of this discussion lies an inherent contradiction: while both VPNs and MITM attacks manipulate data flow, their intentions and implications vastly differ. A VPN serves as a guardian of privacy, encapsulating user information and shielding it from prying eyes. In contrast, a MITM attack is predicated on deceit, harnessing control over communication channels to eavesdrop or impersonate involved parties. Yet, we must unravel the complexities that bind these concepts to appreciate their divergent roles.
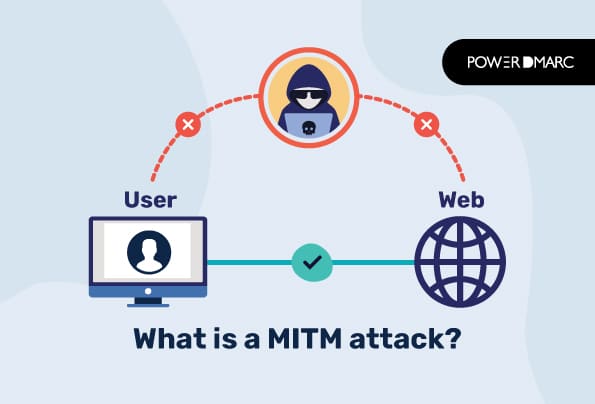
First, it is essential to demystify what constitutes a MITM attack. This form of cyber assault occurs when an adversary clandestinely relays and possibly alters the communication between two parties who believe they are engaging directly with each other. The implications are extensive; sensitive data, including login credentials and financial information, is at stake. Studies indicate a rising prevalence of MITM exploits, particularly in unsecured public Wi-Fi networks, wherein unsuspecting users can unwittingly expose themselves to threats.
Conversely, a VPN operates with the intention of obfuscating a user’s online journey. By routing a user’s internet traffic through a secure server, a VPN encrypts data en route to its destination. An unintended consequence of this is that the VPN provider serves as a *middleman*, hence the initial confusion with MITM terminology. Herein lies the playful inquiry: can a VPN provider, assumed to be a trusted entity, be perceived as a benevolent MITM? The landscape is rife with pitfalls, necessitating a thorough examination of trust and transparency.
One critical aspect to consider is the level of trust associated with VPNs. When employing such services, users must place faith in the provider to uphold data integrity and privacy. The relationship intrinsically involves a transaction of trust—while users sacrifice a semblance of autonomy by routing their traffic through the VPN, they expect the provider to act in their best interest. However, a lack of stringent regulations and oversight in the VPN industry leads to variances in service quality. Some VPNs may log user data, which can paradoxically compromise the very confidentiality they promise to protect.
Moreover, the encryption mechanisms employed by VPNs, while formidable, are not invulnerable. Cyber threats continue to evolve, and the sophistication of attackers can often outpace that of security measures. If a VPN is compromised, it becomes a conduit for potential MITM attacks. Therefore, can it indisputably be categorized as a reliable safeguard against malign influences? Or does it morph into a potential vector for vulnerability? The dichotomy invites scrutiny rather than acceptance.
Consider the implications for corporate networks that deploy VPNs for remote work. Security protocols are essential, yet the level of security may vary among different providers. A benign VPN could inadvertently transform into an adversarial tool, particularly when employees access sensitive information outside secure environments. Instances of compromised VPN services have surfaced, leading to corporate data breaches that wreak havoc on reputation and finances alike.
Returning to our playful inquiry, one must ponder the ethical dimensions entwined with VPN usage. Is it ethical to utilize a tool designed to obfuscate data when such practices can also promote illicit activities? Can the nuances of intention redefine what constitutes a MITM attack? The cybersecurity landscape thrives on ethical ambiguity, pushing users to navigate a labyrinth of moral dilemmas.
As we delve into the weeds, it becomes evident that the interoperability of VPNs and MITM attacks illustrates a fine line between security and compromise. A VPN can facilitate a secure channel for users’ data, yet it also introduces a dynamic where the provider possesses significant power over that information. This tension is magnified in discussions surrounding net neutrality and digital rights, raising questions about the broader implications of entrusting third-party providers with sensitive personal data.
The pressing challenge remains: how do individuals discern reliable VPNs from potential deceivers? Scrutinizing a provider’s privacy policies, user reviews, and independent audits can aid in navigating this murky water. Additionally, awareness of the broader cybersecurity landscape enables users to recognize the multifaceted nature of online threats.
In conclusion, the relationship between VPNs and MITM attacks is anything but straightforward. VPNs are not inherently MITM attacks; rather, they embody the paradox of providing security while simultaneously posing potential risks. As users, the onus rests on us to remain vigilant, educated, and skeptical in our digital realms. Navigating the intricate web of trust that envelops both VPNs and MITM threats ultimately shapes our online experiences, underscoring that in cybersecurity, clarity often resides beneath layers of complexity.








Leave a Comment