In recent years, the proliferation of virtual private networks (VPNs) has sparked a substantial debate regarding their utility and implications in the realm of online security. The rising awareness of vulnerabilities associated with internet usage has led many individuals to embrace VPNs as a tool for safeguarding their data. However, an intriguing question arises: could a VPN itself be perceived as a man-in-the-middle (MitM) tool in disguise? This inquiry invites a closer examination of both the functionalities of VPNs and the principles underlying MitM attacks.
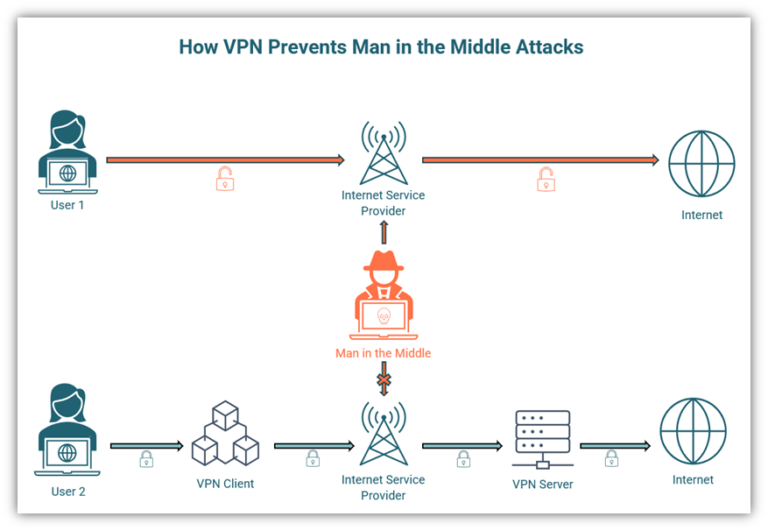
To understand the nuances of this query, it is pivotal to first delineate what a MitM attack entails. In essence, a MitM attack occurs when a malicious actor intercepts and potentially alters the communication between two parties without their knowledge. The attacker can harvest sensitive information, such as passwords and financial data, or inject harmful content into the conversation. This insidious tactic highlights a critical vulnerability in the architecture of internet communications, where trust is often implicitly placed in the pathways through which data travels.
Conversely, VPNs are designed to create a secure channel between a user’s device and a server operated by the VPN provider. By encrypting internet traffic, VPNs purportedly shield users from potential eavesdroppers and data harvesters typically associated with unsecured networks, such as public Wi-Fi hotspots. This encryption ostensibly forms a protective barrier, promoting privacy and safeguarding sensitive information from prying eyes.
However, the juxtaposition of these two concepts raises a pressing question about the nature of trust and the dynamics of data transmission in the digital age. While VPNs aim to enhance user security, they introduce their own complexities that can mirror the characteristics of MitM scenarios.
At the heart of the matter lies the role of the VPN provider. When a user connects to a VPN, their data is routed through the provider’s servers. In this scenario, the provider effectively becomes a middleman in the communication process. While the intention is to secure data through encryption, this arrangement begs the question: to what extent can users trust their VPN provider? Lurking within this uncertainty is the potential for data logging, unauthorized data selling, or even exploitation by nefarious actors who gain access to traffic data.
Furthermore, many VPN providers offer various tiers of service, with some claiming a no-log policy while others may engage in data retention to enhance service performance or comply with local laws. This dichotomy raises critical ethical considerations about user privacy versus operational requirements. Users must navigate a labyrinth of choices, often relying on marketing claims that lack transparency and regulatory oversight. The devil, as they say, is often in the details, and skimming the surface can lead consumers to unwittingly jeopardize their data security.
Another dimension to consider is the efficiency and effectiveness of VPN technologies themselves. The act of encrypting and rerouting network traffic can introduce latency and reduce overall connectivity speeds. While many users are aware of the trade-off associated with enhanced privacy, few recognize the potential pitfalls of relying solely on a VPN for complete anonymity on the internet. With the advent of increasingly sophisticated techniques employed by cybercriminals, merely employing a VPN is not a panacea for security woes.
Moreover, the fundamental architecture of the internet supports a multitude of vulnerabilities independent of VPN usage. Even with robust encryption practices, inherent weaknesses exist within protocols such as Transmission Control Protocol (TCP) and Internet Protocol (IP), allowing for the possibility of MitM exploits. Thus, while a VPN may provide a layer of encryption over additional security mechanisms, it does not unequivocally eliminate all vectors of attack.
Concomitantly, the ambiguity surrounding VPNs creates a fertile ground for misinformation and misconceptions. There exists a pervasive belief that employing a VPN automatically guarantees complete online anonymity. This fallacy can lead users into a false sense of security, potentially neglecting other essential practices such as two-factor authentication, regular software updates, and vigilance regarding phishing attempts. The complexity of cyber threats demands an integrated approach to security that extends beyond the singular adoption of VPN technology.
In summation, the assertion that a VPN could symbolize a man-in-the-middle tool in disguise encapsulates the duality of its function in modern digital communications. While it serves to fortify user privacy through encryption, it simultaneously places trust in the hands of the VPN provider, thus invoking potential vulnerabilities reminiscent of MitM attacks. Users are urged to exercise caution, critically evaluating their chosen VPN provider and remaining cognizant of the multifaceted nature of online security.
The conversation surrounding VPNs is far from black and white. It is incumbent upon individuals to engage in proactive security measures that encompass a comprehensive understanding of both the tools at their disposal and the pervasive threats that populate the digital landscape.







Leave a Comment