The digital landscape is a playground for a myriad of cyber threats, among which the brute force attack stands as one of the most primitive yet effective methods of unauthorized access. But is engaging in such activities—whether for malicious intent or research—considered illegal? This question propels us into a complex gray area that warrants a thorough examination.
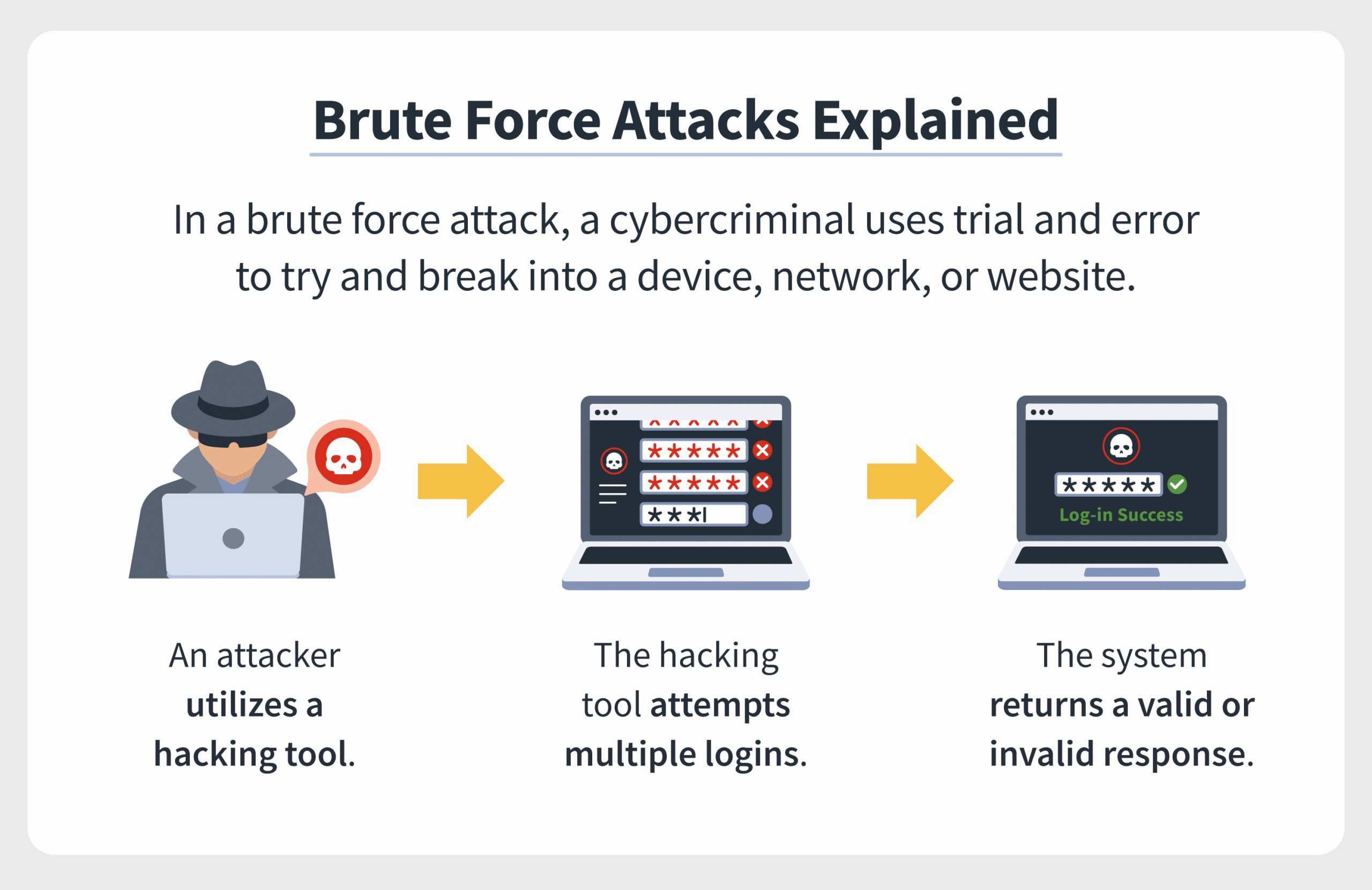
Fundamentally, a brute force attack involves systematically attempting various combinations of credentials to gain unauthorized access to a system. This method leverages the computational power available today, making it feasible for even the most secure systems to eventually succumb if not adequately fortified. However, the legal ramifications of executing a brute force attack hinge on several factors, including intent, scope, and jurisdiction.
Initially, one must explore the implications of intent. If an individual employs brute force tactics to access accounts or systems without explicit authorization, this action clearly crosses into illegal territory. Organizations often have stringent security protocols to combat such intrusions. Unauthorized access can lead to criminal charges under various laws, including the Computer Fraud and Abuse Act (CFAA) in the United States, which outlines specific stipulations surrounding computer-related offenses.
Conversely, the gray area emerges when one considers ethical hacking. Ethical hackers, or “white hats,” utilize brute force methodologies within stipulated boundaries for the purpose of enhancing cybersecurity. Their endeavors, sanctioned by organizations through explicit consent, aim to reveal vulnerabilities. This act, inherently noble in intent, complicates the legality of brute force techniques. Ethical hackers navigate a delicate line; their actions, while beneficial, must always be endorsed by the system owner to stay within legal confines.
The notion of consent introduces additional layers of complexity. In many jurisdictions, pursuing brute force tactics without clear permission can result in punitive measures, regardless of the hacker’s intent. This raises pressing questions: What constitutes valid consent? How explicitly must an organization affirm their approval? The answers vary widely and often rely on context. Thus, ethical implications intertwine with legal considerations, leading to potential ambiguities.
It is also vital to examine the ramifications of scale. A smaller-scale brute force attack might be treated with benign neglect by legal authorities, especially if it does not lead to any identifiable harm or data breach. In contrast, large-scale attacks, particularly those that disrupt services or compromise sensitive information, invariably draw legal scrutiny. Herein lies the paradox: an act perceived as harmless when executed on a micro-level may evolve into a criminal offense based on its scale and impact.
Additionally, the landscape of legality regarding brute force attacks shifts with emerging technology and evolving cyber laws. As organizations increasingly adopt sophisticated countermeasures against such attacks—ranging from locking accounts after a certain number of failed attempts to employing behavioral analysis—what was once permissible may quickly become illegal. Consequently, practitioners in the cybersecurity field must remain vigilant, constantly adapting to both technology and regulations. This accelerates the necessity for ongoing education about the intricacies of cyber law.
Geographic variance also plays a critical role in assessing the legality of brute force attacks. While the CFAA in the United States delineates clear statutes, other countries may embrace disparate laws governing computer-related offenses. In some jurisdictions, the legal definitions of unauthorized access and consent may differ remarkably. As globalization continues to intertwine virtually every aspect of life, individuals and organizations must be cognizant of the laws that govern digital interactions across borders.
The digital domain’s inherent transient nature further complicates the landscape. Data is ephemeral. Perpetrators may find themselves in jurisdictions where laws are nebulous or poorly defined, thwarting accountability. Moreover, the evolution of tactics utilized in brute force attacks—from leveraging distributed networks to employing machine learning algorithms—compounds the difficulty in applying traditional legal frameworks to contemporary cyber threats.
Looking through a wider lens, the dialogue surrounding brute force attacks cannot be divorced from the ongoing discourse about digital rights and cybersecurity ethics. The societal implications of hacking—be it for gain, exposure, or altruism—demand comprehensive consideration. As technological advancements pave new avenues for interaction, individuals often find themselves grappling with moral dilemmas surrounding privacy, consent, and the justification of their actions.
In conclusion, whether a brute force attack is illegal remains an intricate conundrum rife with gray areas. The legality hinges significantly on intent, consent, scale, jurisdiction, and the evolving technological landscape. As the lines between ethical hacking and cybercrime continue to blur, a collective understanding of the implications of one’s actions in the cyber realm becomes indispensable. Engaging in brute force tactics requires careful navigation to avoid the legal pitfalls that lurk in the shadows of this fascinating yet perilous domain. In exploring these complexities, a more nuanced understanding of cybersecurity and the responsibilities inherent in it can be cultivated, leading to a more secure digital future for all.







Leave a Comment