In an increasingly digital world, grasping the concept of digital signatures is essential for both individuals and businesses alike. They serve a pivotal role in ensuring the authenticity and integrity of electronic documents. To comprehend digital signatures without succumbing to the labyrinth of technical jargon, we can break down this notion into several fundamental components.
At its core, a digital signature functions much like a handwritten signature or a stamped seal, but they exist in an electronic format. They provide a means of validating the sender’s identity and ensuring that the message or document has not been altered in transit. Unlike traditional signatures, which can be easily forged, digital signatures utilize intricate cryptographic techniques that make them vastly more secure.
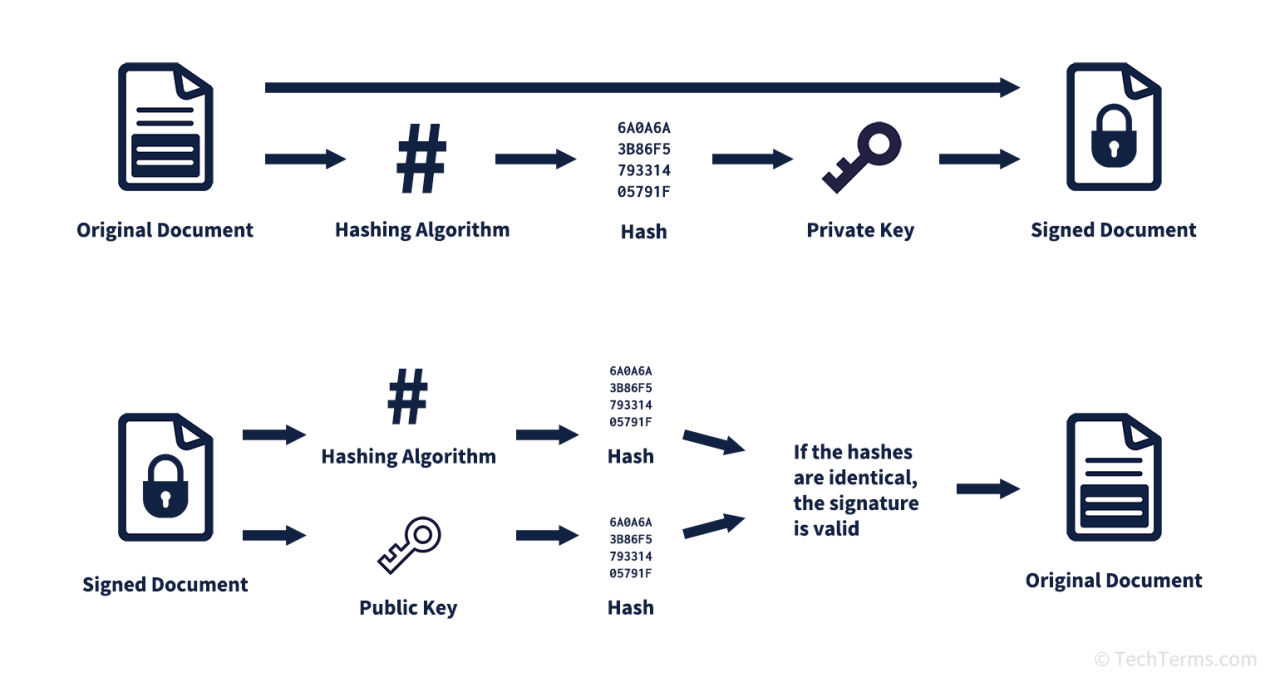
The process begins with the creation of a unique hash value, a short representation of the data within a document. This hash is generated through a mathematical algorithm that transforms the original data into a fixed-length string of characters. Each document will produce a distinct hash, even if the content varies by a mere character or spacing. This property, called uniqueness, guarantees that the hash will change if any part of the document is modified.
Next comes the critical role of asymmetrical encryption. Each user possesses a pair of cryptographic keys: a public key and a private key. The private key is kept confidential by the user, while the public key is shared openly. When a document is signed digitally, the hash value is encrypted using the sender’s private key. This encrypted hash, along with the original document, constitutes the digital signature. The act of signing transforms the simple hash into a secure, verifiable piece of data.
Upon receiving a signed document, the recipient can verify its authenticity using the sender’s public key. By decrypting the digital signature, the recipient obtains the original hash. They then generate a new hash from the received document to ensure the two match. If both hashes correspond, it confirms that the document has not been tampered with and that the signature genuinely belongs to the sender. Thus, the dual aspects of authenticity and integrity are upheld.
There are notably three significant types of digital signatures, each varying in complexity and security:
- Simple Electronic Signatures (SES): These are the most basic form of digital signatures. Essentially, they affirm the consent of an individual to a digital document without the intricate encryption techniques. While convenient, they offer limited protection and can be susceptible to forgery.
- Advanced Electronic Signatures (AES): AES incorporates stronger security measures, binding the signature with the signatory’s identity through a secure system. These signatures use encryption to provide enhanced verification capabilities, ensuring the integrity of the signed document.
- Qualified Electronic Signatures (QES): Representing the highest level of security among digital signatures, QES relies on a qualified certificate issued by a trusted certification authority. It guarantees not only the identity of the signer but also the highest level of integrity and validation under laws like the EU’s eIDAS regulation.
Understanding the legal implications of digital signatures is equally imperative. Different jurisdictions around the globe have established regulations to govern the use of digital signatures in commercial transactions. For instance, the Electronic Signatures in Global and National Commerce Act (ESIGN) in the United States grants electronic signatures the same legal standing as traditional signatures. Similarly, the eIDAS regulation in Europe outlines strict parameters regarding the use of digital signatures to ensure their authenticity and reliability.
Moreover, the importance of digital signatures extends beyond mere legality; they encapsulate a layer of security that traditional signatures lack. In the digital realm, where cyber threats are rampant, utilizing digital signatures significantly mitigates risks associated with document forgery, phishing attacks, and identity theft. By affixing a digital signature, an individual or organization asserts their commitment to the authenticity of the document, providing peace of mind to all parties involved.
The applications of digital signatures are vast and permeate various industries. In finance, they are integral for secure transactions, ensuring that sensitive information is not intercepted or altered. In healthcare, digital signatures facilitate secure sharing of medical records while maintaining patient privacy. Even in government, digital signatures help expedite processes and reduce paperwork, contributing to broader efficiency and transparency.
While the concept of digital signatures can seem daunting at first glance, understanding their fundamental workings, types, and importance can demystify their role in our digital lives. They provide a robust mechanism for ensuring document integrity and authenticity—an essential facet of modern communication.
In conclusion, digital signatures represent a harmonious blend of technology and security, essential for the seamless operation of electronic transactions. By grasping the essentials and their implications, readers can navigate the digital landscape with prudence and confidence, ensuring that their communications remain both secure and credible.







Leave a Comment