In today’s hyper-connected world, securing data has become paramount. With constant debates surrounding privacy and data breaches, understanding how to protect sensitive information is essential. Encryption, a transformative technology, serves as the cornerstone of modern cybersecurity protocols. Below, we delve into various facets of data encryption, outlining its significance, the types of encryption methods available, and practical applications.
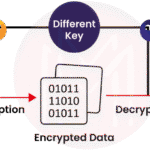
Data encryption serves to obscure information, rendering it unreadable to unauthorized users. Essentially, it converts plain text into a coded format through algorithms, which can only be accessed or reverted to the original text through a decrypting key. This process not only enhances data security but also fortifies the trust among users, stakeholders, and clients.
The process of encryption can be categorized primarily into two types: symmetric encryption and asymmetric encryption. Each serves unique purposes and possesses distinct characteristics.
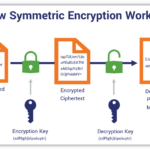
Symmetric Encryption employs a single key for both encryption and decryption processes. The primary advantage of this method lies in its speed and efficiency, making it suitable for processing large volumes of data swiftly. Popular algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES). However, the security of symmetric encryption heavily relies on the secrecy of the key. If the key is compromised, so is the entire encrypted data.
In contrast, Asymmetric Encryption uses a pair of keys – a public key for encryption and a private key for decryption. This bifurcation greatly enhances security since the public key can be shared openly, while the private key remains confidential. RSA (Rivest-Shamir-Adleman) is a widely-recognized example that demonstrates the effectiveness of asymmetric encryption. Nevertheless, the computational intensity and slower speeds of this method often make it less suitable for encrypting large amounts of data.
When discussing encryption, one must consider its applications across different platforms. For instance, data at rest encryption involves securing stored data, while data in transit encryption protects data actively being transferred through networks. By utilizing various encryption strategies tailored to these contexts, organizations can significantly mitigate the risks associated with data breaches.
Implementing encryption does not solely pertain to securing sensitive files. With the advent of cloud storage and online services, encryption creates a fortress around personal information, eliminating unauthorized access. Encrypting data in transit ensures that even if intercepted, the information remains inaccessible, maintaining privacy during communications.
Another critical aspect of modern encryption is the concept of end-to-end encryption (E2EE). This method secures a message from its origin to its destination, meaning only the communicating users can read the data. While E2EE is widely adopted in messaging platforms like WhatsApp and Signal, it transcends simple messaging applications, aiding in protecting banking transactions, personal information, and sensitive business communications.
Moreover, understanding the potential vulnerabilities in encryption systems is equally crucial. Cryptographic attacks, such as brute force attacks, can target weak encryption algorithms or poorly managed keys. Cyber adversaries utilize significant computational power and sophisticated algorithms to bypass security measures. To combat such threats, employing best practices, such as using long and complex keys and regularly updating encryption standards, is imperative.
Additionally, with the evolution of technology, the rise of quantum computing presents an impending challenge to traditional encryption methods. Quantum computers possess abilities that could potentially undermine current cryptographic algorithms, causing widespread concern among security experts. Hence, the exploration of quantum-resistant algorithms is becoming an urgent priority for data security specialists.
Compliance with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) necessitates the encryption of sensitive personal data. Organizations must ensure their encryption practices align with these legal frameworks to avoid hefty penalties and foster trust within their customer base.
Furthermore, educating employees about encryption and overall data security practices is vital. Human errors often lead to data breaches, with poorly managed passwords and lapses in security protocols posing substantial risks. Regular training sessions and workshops can cultivate a culture of security awareness, empowering employees to protect sensitive information proactively.
As technology continues to evolve, so too will the methods employed to secure data. Emerging trends in encryption, such as homomorphic encryption and secure multi-party computation, present innovative solutions for data privacy and security in complex environments. These advanced techniques allow computations to be performed on encrypted data without decrypting it, thereby retaining utmost confidentiality while still facilitating data analysis.
In summary, securing data with encryption involves a multifaceted approach, taking into consideration the specific requirements and risks inherent to each organization. Understanding the strengths and weaknesses of different encryption methods, staying conscientious about the evolving landscape of technology, and adhering to compliance standards are fundamental to fortifying data security. Successful encryption practices not only safeguard sensitive information but also instill confidence in clients, promoting a robust ethical framework around data management.
The essence of encryption transcends mere technicality; it is about implementing a holistic strategy to protect personal and organizational data in an increasingly volatile digital environment.







Leave a Comment