The digital age has ushered in an unprecedented era of data generation and storage. Not only are personal details such as names and addresses at stake, but also sensitive information ranging from financial records to health data. Understanding how to manage and safeguard this kind of sensitive data has become paramount in our interconnected world. However, the fine line between vigilance and paranoia is often blurred, leading to an overzealous approach that may inhibit necessary interactions and functionalities. This article elucidates the principles of safely handling sensitive data without succumbing to a state of unyielding fear.
To begin, it is essential to recognize the intrinsic value of sensitive data. Sensitive information, by its nature, is privy, holding potential ramifications if divulged or mishandled. It is not merely a collection of digits and letters; it embodies the personal lives of individuals and the operational frameworks of enterprises. With this understanding, we can contextualize the need for robust security mechanisms that prevent data breaches and unauthorized disclosures.
At the core of mitigating risks associated with sensitive data is the implementation of the principle of least privilege (PoLP). This doctrine posits that individuals and systems should only have access to the data necessary for their functions. By constraining access, organizations reduce the potential attack surface, effectively thwarting malevolent threats. Oftentimes, a benign employee may inadvertently become a vector for harm merely by having unfettered access. Thus, reviewing and auditing permissions regularly is a prudent practice that fosters a culture of caution without fostering paranoia.
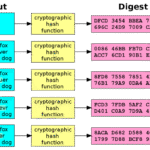
Encryption serves as another cornerstone of data protection. It transforms data into a format that is incomprehensible to unauthorized users. While many individuals may find encryption daunting due to its technicalities, modern solutions have evolved to provide user-friendly options. Employing end-to-end encryption ensures that even if data is intercepted, it remains shielded from exploitation. In essence, this process is akin to locking one’s valuables in a safe; even if a thief gains entry into the place of storage, the treasure remains inaccessible without the key.
Moreover, the significance of education cannot be overstated. Organizations must invest in training their personnel on data security protocols, imparting knowledge about social engineering tactics like phishing. Employees should be apprised of their role in safeguarding sensitive information, creating a security-aware workforce that recognizes potential threats without descending into paranoia. Establishing comprehensive yet digestible guidelines will foster a sense of responsibility and awareness, rather than afflicted anxiety.
In parallel, fostering a culture of open communication about data breaches, cyber threats, and security is vital. Fear often stems from a lack of understanding, and when individuals are educated about risks and their protective measures, anxiety dissipates. Regular discussions and workshops can facilitate this deepening comprehension and promote a proactive mindset, wherein individuals feel empowered rather than anxious about inadvertently exposing sensitive data.
Data management frameworks such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) offer structured methodologies to guide organizations in their data protection endeavors. Compliance with such regulations not only fortifies the organization’s stance on data integrity but also instills confidence among clients and stakeholders. It is essential to note that such adherence should not be perceived as an imposition, but as a catalyst for establishing a security-centric ethos that benefits all parties involved.
Periodic assessments and audits of data security measures are crucial for maintaining integrity over time. Regular testing, including penetration tests, can unearth vulnerabilities that may have gone unnoticed. This analytical approach offers opportunities to bolster defenses preemptively rather than reactively. Emphasizing this progressive attitude towards data security cultivates an environment where concerns about mishandling sensitive data do not manifest into paranoia but rather into pragmatic vigilance.
However, it is equally critical to recognize the balance needed between over-precaution and flexibility. An overly rigid data protection protocol may inhibit operational efficiency. Organizations must navigate the complexities of remaining secure while adaptable. For instance, multi-factor authentication (MFA) is a robust security practice that enhances protection without obstructing user experience. Sensible strategies should be adopted to accommodate both safety and convenience, thereby alleviating unnecessary anxiety about potential data breaches.
Furthermore, the influence of technology on data safeguarding cannot be ignored. Advanced tools and technologies such as artificial intelligence and machine learning are revolutionizing how organizations approach data security. These technologies can detect anomalies and respond to threats in real-time, providing layers of protection that were previously unattainable. However, reliance on such tools does not eradicate the need for human oversight and constant vigilance. A balanced approach, incorporating technology with human intuition, is quintessential for fortifying sensitive data management.
In conclusion, navigating the complex landscape of sensitive data management requires a nuanced understanding of its implications and safeguards. By embracing the principles of least privilege, encryption, education, communication, compliance, regular audits, and a balanced approach to technology, organizations can effectively manage sensitive data without fostering an environment of paranoia. Security is paramount, but fostering a culture of responsible data stewardship can yield benefits that extend far beyond mere compliance. In the end, it is about establishing trust—within organizations and between entities—while ensuring that sensitive information is preserved with integrity.






Leave a Comment