In the realm of digital security, cryptographic services play a pivotal role in safeguarding sensitive data. Imagine navigating a vast forest filled with potential perils, where the only way to ensure safety is by traversing carefully through known paths—this analogy resonates with the challenge of identifying cryptographic security services in any system. Understanding these services requires more than superficial knowledge; it demands a deep dive into the core mechanisms that uphold data integrity and confidentiality.
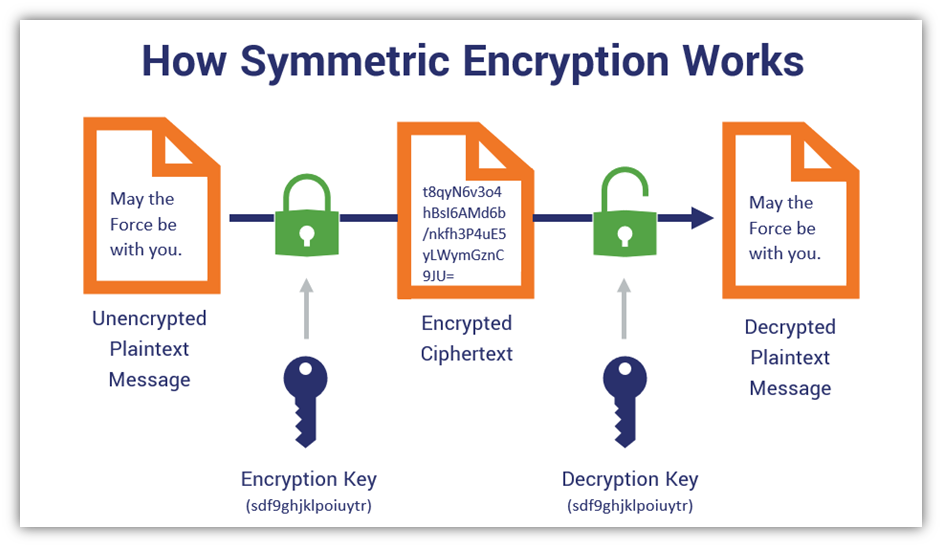
Identifying cryptographic security services involves recognizing the key components that contribute to a system’s security architecture. First, one must examine the various types of cryptographic algorithms employed. These algorithms can be broadly categorized into symmetric and asymmetric encryption. Symmetric encryption utilizes a single key for both encryption and decryption processes, rendering it efficient yet requiring secure key distribution. In contrast, asymmetric encryption employs a pair of keys—a public key for encryption and a private key for decryption. This dual-key system facilitates secure communication without the necessity of sharing sensitive information openly.
Examining the algorithms in use is only the preliminary step. Next, it’s essential to consider the cryptographic protocols that implement these algorithms. Protocols such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL) preside over internet communications, ensuring that data in transit remains confidential and unaltered. They achieve this by establishing secure channels through which data can traverse without fear of interception. Furthermore, recognizing the role of hashing functions, which convert data into fixed-size strings, adds another layer of security. Hash functions, such as SHA-256, ensure data integrity by producing unique outputs that can be verified without compromising the original data.
However, the identification of cryptographic services necessitates scrutiny beyond algorithms and protocols. One must investigate the architecture of the system itself. Is it employing a centralized model where key management resides with a single authority, or is it decentralized, thus dispersing control and enhancing security resilience? The choice between these models influences susceptibility to attacks. A centralized system may simplify key management but represents a single point of failure, while decentralized systems distribute risk but can complicate management strategies. This dichotomy requires careful consideration when assessing security posture.
Moreover, delving into the nature of key management systems (KMS) is an indispensable aspect of identifying cryptographic services. Robust key management is crucial, as compromised keys can render even the most sophisticated encryption ineffective. A well-designed KMS should encompass key generation, storage, distribution, rotation, and revocation processes, each fortified against potential vulnerabilities. The presence of a hardware security module (HSM) is worth noting; it provides physical security for cryptographic keys, thereby thwarting unauthorized access and reducing risk associated with software-based key storage.
Risk assessment is an integral part of drawing conclusions about cryptographic capabilities. Engaging in a thorough risk analysis can determine potential weaknesses within the cryptographic processes of any system. This evaluation should include an examination of threat models—what adversaries exist, what their motivations might be, and how they could potentially exploit vulnerabilities. Consequently, this lays the groundwork for implementing countermeasures that bolster cryptographic security.
One may ponder a playful question: What if a system’s cryptographic services are akin to a classic riddle, quiet yet full of tricks? Revealing the truth behind these services requires careful observation and analytical thinking. A multifaceted approach is essential for discerning the hidden complexities. This elucidation leads to an understanding that identifying cryptographic services is not merely a technical endeavor; it is an investigative pursuit.
Moving forward, it is pivotal to consider the role of compliance and regulatory standards in evaluating cryptographic security. Recognizing frameworks such as the Payment Card Industry Data Security Standard (PCI DSS) and Federal Information Processing Standards (FIPS) can provide benchmarks for encryption practices. Compliance with these standards serves as a solid endorsement of a system’s commitment to cryptographic integrity and security measures. Their guidelines not only elevate confidence but also pave the way for best practices within the industry.
Furthermore, assessing the implementation of cryptographic services should include the examination of authentication mechanisms. Multi-factor authentication (MFA) exemplifies a contemporary practice that combines something a user knows (like a password), something a user has (like a mobile device), and something a user is (like a fingerprint), thus significantly enhancing security through layers. The integration of such multifarious approaches is an evolving field within cryptography that addresses both user requirements and threat landscapes.
Finally, continual vigilance is imperative. The fast-evolving landscape of cyber threats necessitates that organizations maintain an adaptable posture, ready to incorporate emerging cryptographic innovations. As cryptographic practices advance, so too must the processes of identification and assessment. Regular audits and updates based on the latest threat intelligence should be an elemental part of any system’s security protocol.
In conclusion, recognizing and identifying cryptographic security services within a system is a multifaceted endeavor that involves understanding underlying algorithms, protocols, architecture, and risk management strategies. By incorporating comprehensive evaluations, compliance with regulations, robust key management, and strict authentication practices, one can craft an intricate landscape of cryptographic security. The quest to navigate this domain might pose challenges, but with analytical rigor and informed scrutiny, a secure path can be forged through the complexities of digital data protection.







Leave a Comment