In the ever-evolving landscape of information security, the cryptographic safeguarding of sensitive data, particularly passwords, has become an indispensable practice. PowerShell, a versatile scripting language native to the Windows environment, offers functionality to encrypt passwords to fortify them against unauthorized access. However, a pertinent question arises: how safe is this encryption process? This examination delves into the mechanisms underpinning PowerShell’s encryption capabilities, the comparative efficacy of the methods employed, and the fundamental principles of password security.
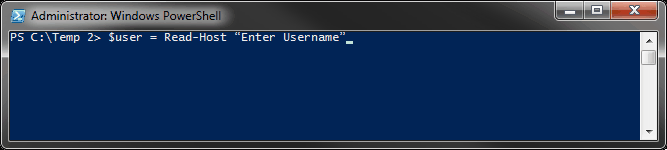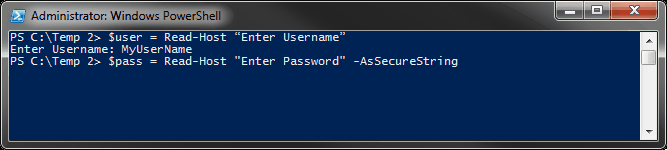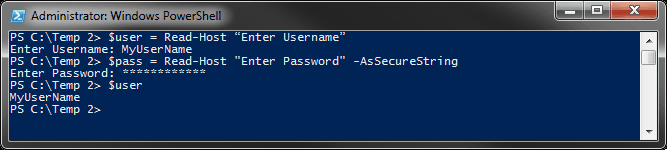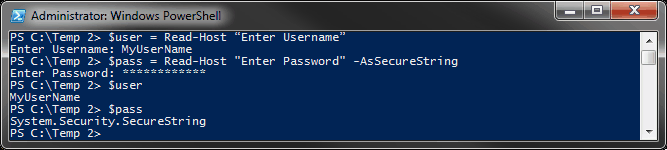
PowerShell utilizes two primary methods for password encryption: SecureString and the ConvertTo-SecureString cmdlet. The former is essential for creating a highly secure string representation of sensitive data, effectively rendering it unreadable in plain text. When this functionality is engaged, PowerShell transforms the password into a SecureString object, which stores data in an encrypted format in memory. This provides a layer of security that is not trivial in the context of threat mitigation.
Utilizing the ConvertTo-SecureString cmdlet allows users to encrypt a string using either a secure key or secure certificates. This method is profoundly beneficial because it employs the Data Protection API (DPAPI) for encryption, which leverages user-specific encryption. Therefore, the encrypted data can only be decrypted by the same user account on the same machine. While this presents an alluring defensive mechanism, it raises questions regarding the efficacy and resilience of such measures against sophisticated attacks.
One of the initial observations when grappling with the security of encrypted passwords is the human tendency to oversimplify perceived threats. Many users assume that once they have encrypted their passwords—even within the PowerShell environment—they are impervious to attacks. This is a precarious overconfidence. Risks such as memory scraping attacks, where malicious software purloins sensitive data directly from memory, can still compromise these encrypted passwords. Therefore, it is crucial to adopt a multi-faceted approach to security, which encompasses not only encryption but also user education and system hygiene.
Moreover, the methodology employed to extract passwords from secure environments—often conducted through social engineering or phishing—highlights an overarching paradox in the domain of cybersecurity. While automated encryption processes are effective in generating secure passwords, human behaviors and vulnerabilities markedly diminish overall security efficacy. The most sophisticated encryption techniques cannot substitute for responsible user behavior. As a result, fostering awareness about social engineering tactics and the importance of employing two-factor authentication can significantly bolster defenses against potential breaches.
In addressing concerns about encryption, it is also vital to consider the nature of the cryptography itself. PowerShell’s encryption techniques, while robust, are not devoid of vulnerabilities. The secure string is only as reliable as the underlying encryption algorithm, and weaknesses in the algorithm can be exploited. Furthermore, the management of encryption keys presents its own set of challenges. Should the key become compromised or mismanaged, the entire security framework disintegrates. Therefore, reevaluating who has access to encryption keys and the contexts in which they are utilized becomes essential.
Incongruities in user behavior particularly surface regarding the storage of encrypted passwords. Many professionals opt to store these secure strings in scripts or configuration files, inevitably introducing risk into the process. Best practices dictate that encrypted credentials should reside in secure vaults or credential stores that are specifically designed to manage sensitive data. Utilizing these tools mitigates the risk of accidental exposure, as they are intrinsically designed to withstand unauthorized access.
A common observation reflects the dichotomy between technological reliance and human ingenuity in cybersecurity. While systems such as PowerShell provide increasingly sophisticated encryption techniques, the human element often undermines their effectiveness. User error, oversight, or a simple lack of understanding can lead to significant vulnerabilities within ostensibly secure systems. Thus, coupling robust encryption practices with comprehensive training programs remains pivotal in fostering a vigilant security culture.
Furthermore, in a world increasingly governed by regulatory compliance, organizations must be cognizant of the stringent requirements surrounding data protection. Adopting PowerShell for encryption can aid compliance with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). These frameworks necessitate not only the encryption of data but also the deployment of effective management practices for keys and access controls. This multifaceted compliance approach ensures a defense-in-depth strategy is embraced, thereby enhancing overall data protection.
While PowerShell presents a formidable toolset for encrypting passwords, it is critical to engage with encryption thoughtfully. Emulating a false sense of security based on encryption alone is a perilous approach. The security of credentials is an intricate balance of employing sophisticated encryption methods, managing user behavior consciously, and adhering to best practices in data governance. Only through a holistic understanding and implementation of these principles can organizations truly fortify their defenses against the ever-looming threat of data breaches.
In conclusion, the act of encrypting passwords in PowerShell yields significant protective advantages; however, the complexity of cybersecurity necessitates a multi-pronged strategy. The interplay between technology and human behavior invites ongoing scrutiny. As threats continue to evolve, so too must our strategies for safeguarding sensitive information, ensuring that encryption serves its rightful purpose in the broader tapestry of information security.








Leave a Comment