The concept of encryption may seem daunting, especially to those unfamiliar with the intricacies of cryptographic algorithms. However, it serves as an essential tool in safeguarding sensitive information in our digitally driven world. Imagine if you possessed a treasure map that you wished to keep hidden from prying eyes—how would you protect it? This playful question leads us to the complicated yet fascinating realm of text encryption. To illustrate this journey, we’ll explore how to encrypt a piece of text using a generalized approach that applies to various algorithms.
Before delving into the intricacies, one must first grasp the fundamental purpose of encryption. At its core, encryption transforms readable data (plaintext) into an unreadable format (ciphertext) using a specific algorithm and key. The key acts as a password; it ensures that encrypted data can only be decrypted by someone possessing the corresponding key. This introduces an interesting challenge: What if two parties need to communicate securely without anyone else accessing their exchanges? This question encapsulates the essence of modern communication and data privacy.
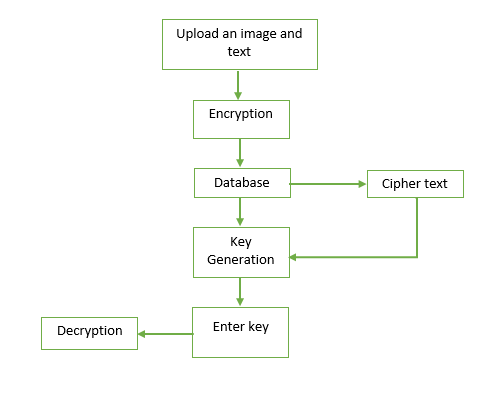
Now, let us embark on our exploration, outlining the essential steps to encrypting text using any algorithm:
1. Choose Your Algorithm
Each encryption algorithm possesses unique methodologies and levels of security. Familiar algorithms such as Advanced Encryption Standard (AES), Rivest Cipher (RC4), and Data Encryption Standard (DES) offer varied approaches to encryption. A decision must be made based on the text’s sensitivity and the required level of security. Would you prefer a symmetric key algorithm like AES, where the same key encrypts and decrypts the data, or opt for an asymmetric algorithm, achieving heightened security through a pair of keys—one public and one private?
2. Decide on a Key
The key, often a sequence of random alphanumeric characters, must be chosen wisely. For example, a 128-bit key for AES may consist of 16 characters, while a more secure 256-bit key requires 32 characters. This raises another challenge: How do you generate a truly random key that resists potential brute-force attacks? Utilizing libraries designed for cryptographic functions can ensure the randomness required for robustness. A thought-provoking question arises: Can you create your key, and how secure would it be?
3. Prepare Your Text
Your text needs preparation for the encryption process. Depending on the algorithm employed, it might require padding, ensuring that the length meets the criteria for block sizes. Consider, for instance, that AES employs 128-bit blocks. You might need to employ a padding scheme like PKCS#7 to adjust the plaintext’s length, facilitating a seamless encryption process. Have you ever pondered how seemingly innocuous characters can change the outcome of an entire encryption scheme?
4. Encrypt the Text
With the algorithm, key, and prepared text in hand, it is time to perform the encryption. Most programming languages offer libraries that streamline the encryption process. For example, in Python, one might use the popular PyCryptodome library. The syntax remains straightforward: initialize the algorithm, load your key, and invoke the encryption method using your plaintext. This act of transformation is a fascinating moment of alchemy—molding ordinary text into an indecipherable cipher. What magic lies in these lines of code?
5. Store the Ciphertext
Upon successful encryption, the resulting ciphertext represents your once-readable text, now shrouded in mystery. Where do you store this ciphertext, and how do you ensure it doesn’t fall into the wrong hands? Best practices dictate isolating sensitive data from public access, perhaps utilizing databases designed for security. Yet, the dilemma remains: if your database is compromised, how will you safeguard your treasure?
6. Managing Keys
The management of keys becomes a pivotal aspect of the encryption lifecycle. A compromised key means compromised data. Distributing the key involves additional complexities. One might consider employing a publicly accessible key to encrypt data, while maintaining a private key for decryption. This establishes a secure communication channel, yet it raises the intriguing question of how securely to exchange keys. Can you outsmart a potential eavesdropper?
7. Decrypting the Text
To reverse the encryption process, upon receiving the ciphertext, one must utilize the original algorithm and the corresponding key. The efficacy of encryption lies not only in its implementation but also in the assurance that only authorized individuals can decrypt the data. Is this not a dual-edged sword, where security must be balanced with accessibility?
8. Continuous Learning and Adaptation
The landscape of encryption is ever-evolving, with new vulnerabilities and techniques emerging systematically. It is paramount for cryptographers and developers alike to remain informed about advancements and best practices. Regularly updating algorithms and keys ensures data remains unabated in the face of emerging threats. Does your encryption strategy stand the test of time, or does it require reassessment?
In conclusion, the encryption process embodies a blend of art and science, encapsulating the need for security in our interconnected world. As we continue to store and share information digitally, understanding how to encrypt text remains paramount. Reflecting on the journey of protecting your metaphorical treasure map allows for a broader understanding of cryptography’s critical role in our daily lives. Will you take the challenge to become proficient in encrypting your own messages? The canvas is set for exploration, and the keys await discovery.








Leave a Comment