The digital landscape resembles a vast, uncharted ocean, teeming with both opportunities and perils. Just as seasoned sailors learn to navigate treacherous waters, cybersecurity professionals must adeptly maneuver through various threats, with one of the most insidious being brute force attacks. In this exploration of cybersecurity, we will delve into the intricacies of these attacks and uncover methods to thwart them, ensuring that your digital vessel remains unsinkable.
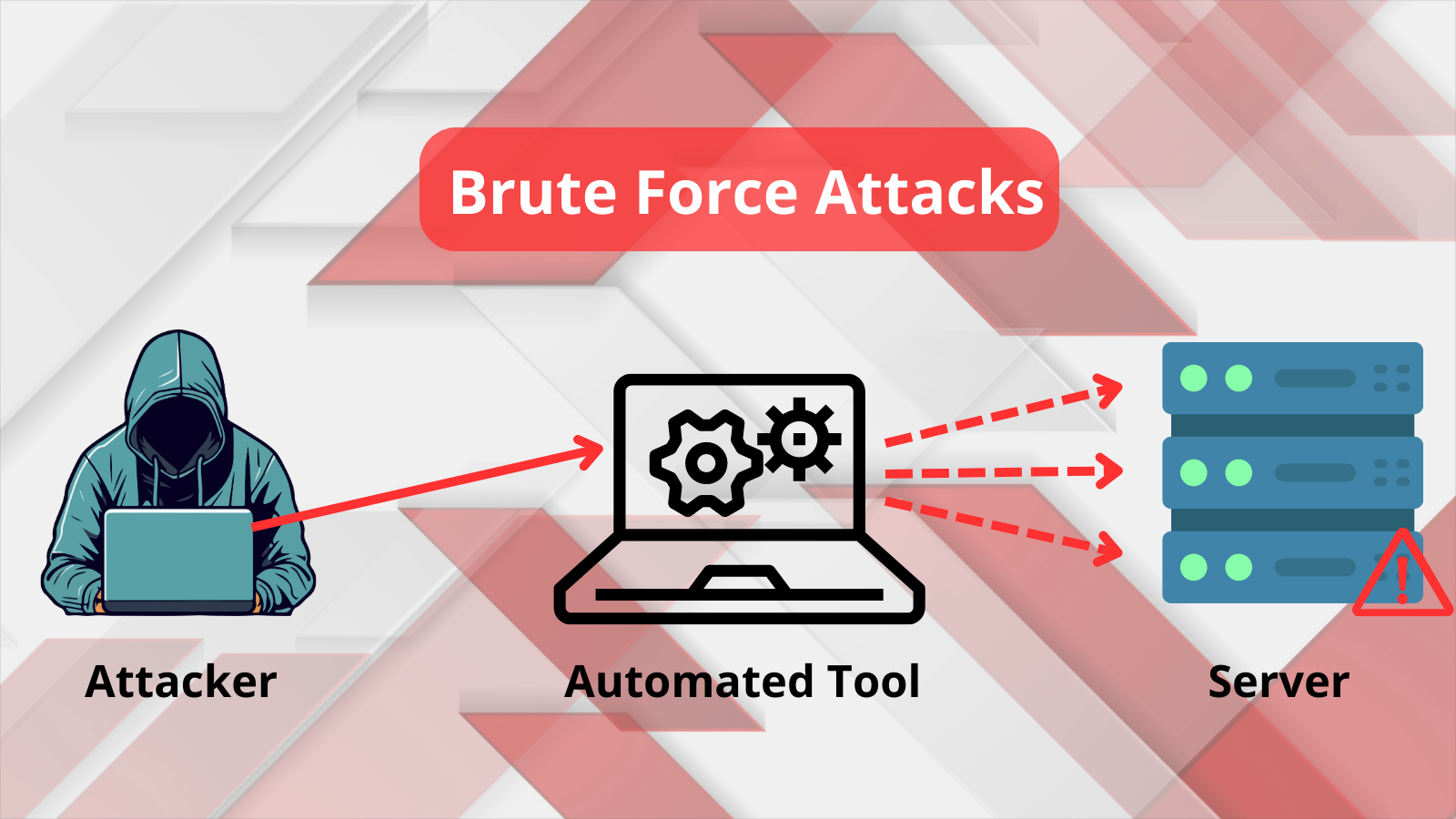
A brute force attack can be likened to a relentless assailant, attempting to breach a fortress by trying every conceivable combination to unlock a gate. This methodology is both simple and barbaric; it relies on sheer computation power rather than cunning. The assailant does not require sophisticated insider knowledge; instead, they persist, governed by persistence and compounded resources. Consequently, no digital infrastructure is immune to such attacks, making it imperative for organizations to adopt robust defensive strategies.
Understanding the anatomy of a brute force attack is crucial in developing ways to avert its consequences. These attacks entail systematically attempting multiple password combinations in rapid succession until access is granted. The consequences of a successful breach can be catastrophic—ranging from unauthorized data access to operational disruptions. Tackling this omnipresent threat necessitates a multi-faceted approach, echoing the sentiment that only rigorous preparation can mitigate potential risks.
One fundamental defensive strategy is the implementation of strong, complex passwords. Imperatively, passwords should not be simplistic; they should resemble cryptographic labyrinths rather than easily decipherable paths. A robust password typically combines uppercase and lowercase letters, numeral digits, and special characters. Ideally, the length of any password should exceed twelve characters—transforming it into a formidable barrier capable of thwarting even the most determined adversary.
However, relying solely on passwords may not suffice. Two-factor authentication (2FA) serves as the digital equivalent of an armed guard standing watch at the castle gate. It requires an additional verification step, such as a code sent to a mobile device or an authentication app. By requiring something the user knows (the password) and something the user possesses (the second factor), the chances of unauthorized access decrease significantly. Adopting 2FA is a straightforward yet highly effective method to fortify security perimeters.
Rate limiting and account lockout mechanisms are additional shields one can deploy in the realm of cybersecurity. Rate limiting involves restricting the number of login attempts from a specific IP address within a designated timeframe. This tactic is akin to a security guard who stops an intruder attempting to access the building repeatedly. When an IP address exceeds the allowed threshold, temporary access restrictions can be enforced, thus thwarting automated scripts designed to crack passwords en masse.
Meanwhile, account lockouts serve as a sanctuary, mandating that accounts become temporarily inaccessible after a specified number of failed login attempts. By incorporating these mechanisms, organizations can dramatically curtail the risk of brute force attacks, forcing attackers to reconsider their approach. It’s fundamental that these measures are complemented by an awareness of the balance between security and functionality. Too stringent limits can frustrate genuine users, thus necessitating a careful calibration of security protocols.
The importance of monitoring and logging cannot be overstated. Proactive surveillance of failed login attempts and suspicious account activity is essential. Regular audits of these logs can unearth patterns and anomalies that signal potential brute force attacks. Consider this the vigilant eye of a watchtower, scanning the horizon for approaching threats. When anomalies are detected, immediate remedial actions can be taken, diminishing the likelihood of a breach being realized.
Furthermore, organizations should garner insights from threat intelligence sharing. Collaborating with peer organizations and engaging in platforms that pool information about recent attack vectors enhances the collective defense. This analogy likens itself to a community of navigators sharing tales of treacherous currents and hidden reefs—offering invaluable guidance to circumvent hazards that may otherwise ensnare unsuspecting vessels.
Moreover, deploying robust encryption protocols adds an additional layer of security. When data is encrypted, it becomes incomprehensible to any unauthorized entity that might access it, even if they successfully breach the initial defenses. Just as navigators utilize star charts and navigation tools, employing encryption decocts a roadmap that ensures sensitive information remains inaccessible to nefarious actors.
If one wishes to take cyber defenses up a notch, intrusion detection systems (IDS) and firewalls should also be considered. IDS monitors network traffic for suspicious behavior, functioning like a barrier reef that detects and deflects unwanted maritime intrusions. Firewalls, on the other hand, act as sentinels, regulating the traffic entering or leaving a network—powerfully controlling the ebb and flow of digital data.
Ultimately, cultivating an organizational culture centered around cybersecurity awareness enhances defensive postures. Training employees to recognize phishing attempts and suspicious activity is paramount. Just as a ship’s crew must be aware of safe navigation practices, so too must organizations educate their employees about the facets of cyber hygiene and the threat posed by brute-force attempts.
In summation, avoiding brute force attacks demands a comprehensive, multi-pronged strategy akin to navigating turbulent waters with precision. From crafting robust passwords to employing cutting-edge security technologies, each defensive measure fortifies the digital realm. The path to safer cyber territories is paved with diligence, education, and vigilance—essentials for safeguarding visceral assets in this expansive digital age.








Leave a Comment