The advent of cryptocurrency has ushered in a new era of digital finance, but it has also raised pressing concerns about security. Understanding the nuances of private key protection is imperative for anyone involved with cryptocurrencies. A private key serves as a crucial component of this digital ecosystem, functioning like a password that grants access to crypto assets. Losing or compromising this key can lead to devastating financial losses. How, then, should one protect this critical piece of information? Herein lies a comprehensive discussion of best practices to secure your private key.
To commence, it is essential to comprehend what a private key entails. It is a cryptographic key that is used to sign transactions and prove ownership of a blockchain asset. The private key must remain confidential, akin to a bank account’s PIN number. Breaches of this information can result in unauthorized access to your digital coins. Consequently, safeguarding your private key should be a top priority in cryptocurrency management.
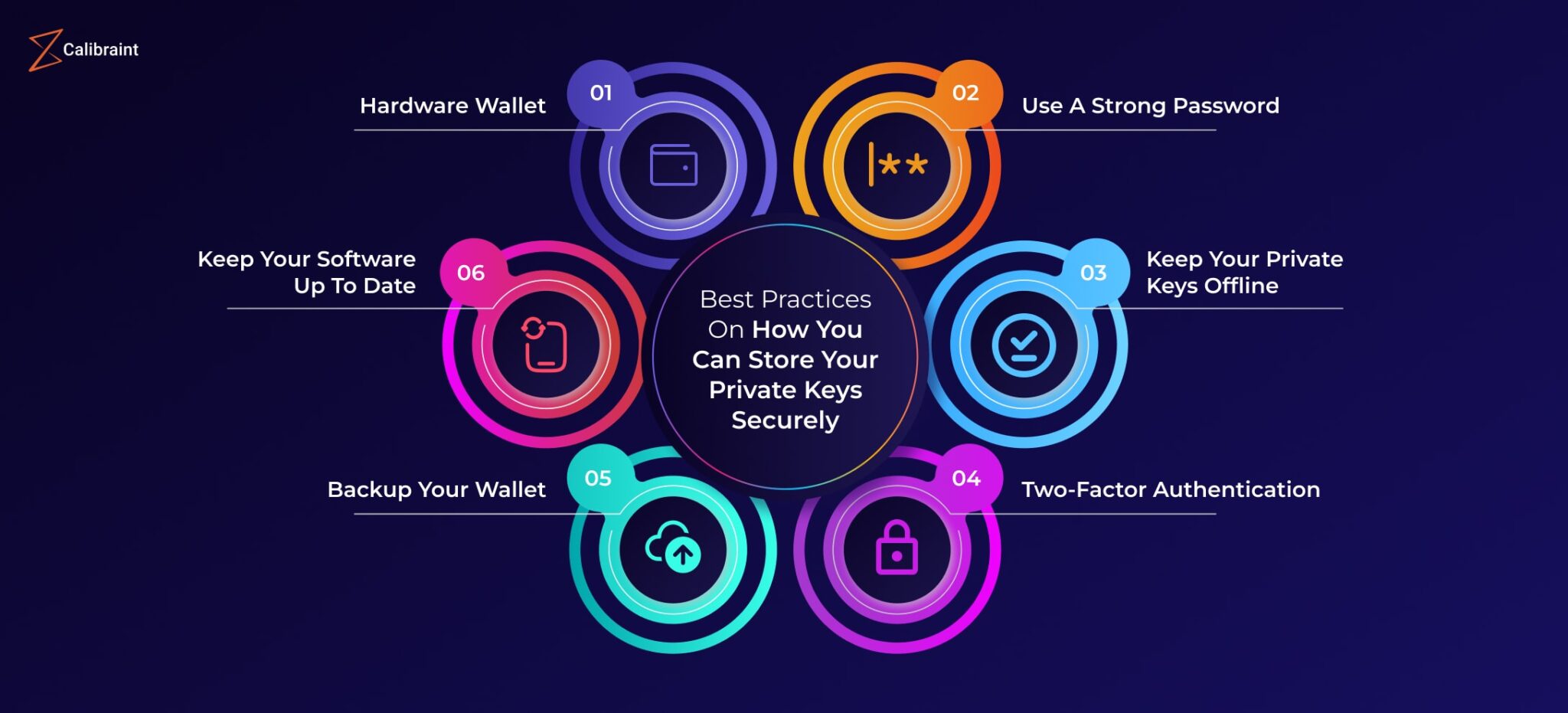
One of the first recommendations is to utilize hardware wallets for storing private keys. Hardware wallets are physical devices specifically designed to store cryptocurrencies securely. They maintain the private key offline, making it considerably more difficult for hackers to gain access through online vulnerabilities. This method mitigates exposure to malicious attacks such as phishing or malware, offering a tangible layer of protection. Moreover, hardware wallets often come with robust security features like PIN codes and recovery phrases, which can further enhance their safety.
In addition, it is prudent to develop a robust backup strategy. In the world of cryptocurrency, redundancy is vital. One should maintain multiple copies of the private key stored securely in different locations. Cloud storage services, while convenient, add unnecessary risk. Instead, opt for physical backups on secure media such as USB drives or external hard drives. Ensure these backup drives are encrypted to prevent unauthorized access. Distribution of these copies among trusted contacts or family members can also serve as an insurance policy against loss or theft.
Another noteworthy practice involves the implementation of two-factor authentication (2FA). By incorporating 2FA, you add an extra layer of security atop your private key. This process necessitates not only possession of the private key but also an additional verification method, such as a text message or authentication app. This multifactor approach is beneficial; it helps in ensuring that even if a key is compromised, the additional verification can thwart unauthorized transactions. It is a simple yet powerful method to diminish the risks associated with digital asset management.
Furthermore, remaining vigilant against social engineering attacks is paramount. Cybercriminals increasingly use manipulation techniques to deceive individuals into divulging sensitive information. Educating oneself about common scams and social engineering tactics can significantly reduce the risk of falling prey. If approached by anyone requesting your private key or sensitive information, employ skepticism. Never disclose private keys, recovery phrases, or personal information without verifying the identity of the requesting party.
The software used to manage your private keys is equally important. One should only engage with reputable wallet providers and avoid lesser-known applications with dubious security protocols. The software should undergo regular updates and maintenance to manage vulnerabilities and threats effectively. Utilize wallets that have undergone a thorough examination by the cryptographic community; peer reviews can serve as a significant indicator of reliability and security.
Moreover, keeping your software environment secure is crucial for private key protection. Utilize up-to-date operating systems and employ antivirus software to protect your devices from malicious attacks. Cyber threats evolve rapidly, and so should your defense mechanisms. Regularly updating your systems mitigates the risk of exploitation from outdated security features.
In addition, consider the implications of using public Wi-Fi networks. Using any unsecured network to access sensitive information concerning your private key is akin to leaving your front door wide open. Public Wi-Fi networks are often breeding grounds for hackers to intercept data. If such a network is unavoidable, utilizing a Virtual Private Network (VPN) can encrypt your connection and complicate unauthorized access attempts.
Physical security should also not be overlooked. Ensuring that your hardware wallet or backup devices are physically secure is vital. Employ safes or secure locations that guard against theft, fire, or natural disasters. In a world of increasing digital threats, the physical aspect of security often gets overshadowed, but safeguarding your hardware from tangible risks is just as crucial.
Engaging in regular security audits can further fortify your defenses. Periodically review your security measures and evaluate if they meet the evolving threats in the digital landscape. This could entail analyzing your software choices, updating hardware wallets, and reassessing the effectiveness of backup strategies. The landscape of cryptocurrency is fluid, and complacency can lead to vulnerabilities.
In conclusion, the protection of private keys necessitates a multifaceted approach. By employing hardware wallets, enhancing security through backup strategies, leveraging two-factor authentication, and remaining vigilant against social engineering attacks, one fortifies their digital assets against a myriad of threats. Cryptocurrency possesses a unique allure due to its decentralized nature and potential for financial independence. However, its security intricacies warrant meticulous attention and proactive measures to ensure safety in handling these digital assets. Ultimately, safeguarding one’s private key is integral not only to protecting financial interests but also to embracing the potential of a decentralized future.







Leave a Comment