In the intricate world of cryptography, secret key cryptography, also known as symmetric cryptography, operates as a cornerstone in securing digital communication. Its operational mechanics, while elusive to the uninitiated, hold profound implications for data confidentiality, integrity, and authenticity. By delving into the enigmatic realm of symmetrically encrypted data, we can unveil the veils of complexity shrouding this indispensable facet of information technology.
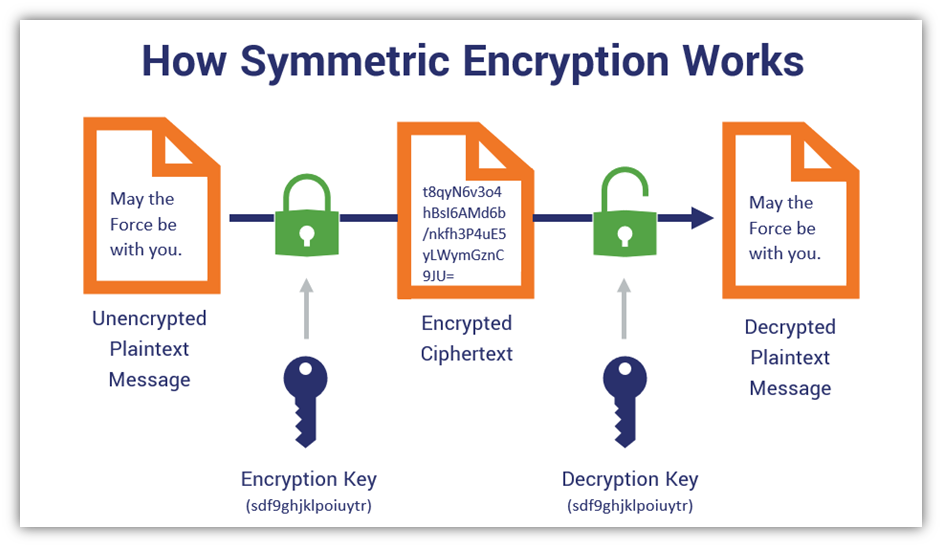
At its core, secret key cryptography revolves around the utilization of a single, shared secret key. This key, a string of bits, serves multiple dualities; it both encrypts data into an unintelligible format and decrypts that data back into its original, comprehensible state. The elegance of this process lies in its fundamental requirement: both parties involved in the communication must possess the exact key. This requirement acts as a double-edged sword, presenting both security benefits and logistical challenges.
The initial step in this cryptographic ballet is a pivotal one—key generation. The effectiveness of the cryptographic scheme relies heavily on the robustness of the generated key. Poorly crafted keys can render an otherwise sophisticated system vulnerable, inviting intrusions from malevolent entities lurking within cyberspace. The security of these keys must be paramount; thus, algorithms such as AES (Advanced Encryption Standard) or DES (Data Encryption Standard) are often employed to yield keys that elude facile discovery.
Once the key is generated, the encryption process commences. Data enters the cryptographic algorithm, combined with the secret key, producing ciphertext. This ciphered output is a mathematically scrambled rendition of the original plaintext, rendering it unintelligible to any unauthorized observers. The transition from plaintext to ciphertext can be envisioned as a lock and key mechanism, wherein the plaintext is the door and the key is crafted specifically to fit a particular lock. Only with the corresponding secret key can the ciphertext be unlocked, reinstating access to the original data.
The allure of secret key cryptography is not merely in its ability to obfuscate data; rather, it also fosters a climate of trust between communicating parties. By concurrently holding the key, both sender and receiver can engage in secure dialogues unconstrained by the prying eyes of adversaries. However, herein lies a significant drawback—the key distribution problem. How do one ensure that the key is exchanged securely without interception? This conundrum is often remedied through asymmetric encryption techniques or secured channels, but the quest for a flawless solution remains a topic of ongoing research.
Moreover, the symbiotic relationship between symmetric and asymmetric cryptography is noteworthy. While symmetric cryptography boasts efficiency in processing speed, asymmetrical methods, despite being computationally intensive, offer a key distribution paradigm that mitigates vulnerabilities inherent in sharing a secret key. This modern coupling demonstrates a trend where hybrid approaches gain traction, showcasing the dynamic evolution of cryptographic practices designed to outrun the sophisticated methodologies employed by cybercriminals.
In an era marked by exponential data proliferation and increasingly sophisticated cyber threats, understanding how secret key cryptography operates invites a shift in perspective. It challenges commonly held beliefs about data security, offering a lens through which to comprehend the mechanisms that underpin our digital existence. As technology advances, so too must our defenses—staying one step ahead of adversaries necessitates a keen awareness of how encryption works and the potential pitfalls that can ensue.
This is where a deeper curiosity about cryptographic resilience is warranted. Engaging with the underlying algorithms and mathematical principles not only unveils the beauty of cryptography but also reveals the vulnerabilities embedded within it. For example, the strength of encryption hinges on the key length; shorter keys exponentially increase the risks of brute-force attacks. Herein lies a paradox: while more extensive keys enhance security, they also increase computational requirements, potentially impeding efficiency—a classic tug-of-war of priorities in the domain of information security.
A critical examination of known attacks wielded against symmetric cryptography is equally enlightening. For instance, techniques such as the birthday attack and linear cryptanalysis exemplify the ongoing arms race between security professionals and ill-intentioned actors. Understanding these methodologies fosters a heightened appreciation for the complexities involved in creating fortifications against digital incursions. This awareness is not simply academic; it stresses the importance of continuously upgrading cryptographic practices to reflect the evolving threat landscape.
As we navigate through the nuances of secret key cryptography, the onus remains on stakeholders to remain agile, adapting their strategies to safeguard data integrity. The adoption of standardized protocols and best practices becomes essential in institutional frameworks, ensuring resilience against potential breaches. This ensures that legitimate communications persist without disruption, countering despondency instigated by security concerns.
In summation, the revelations surrounding how secret key cryptography operates serve not just as a technical exposition but as an invitation to grasp the profound implications of safeguarding information in the digital age. By piquing curiosity and fostering an analytical mindset toward cryptographic practices, a comprehensive appreciation for the art and science of securing our data emerges. Harmonic in its inefficiencies and flaws, secret key cryptography endures as a testament to the ongoing quest for secure communication—a necessary endeavor in an increasingly interconnected world.







Leave a Comment