At the heart of modern digital communication lies a powerful mechanism known as public key cryptography, often likened to a complex lock and key system. Imagine, if you will, a grand castle, fortified not merely by walls but by an ingenious locking apparatus that ensures only the rightful inhabitants can enter. This metaphor neatly encapsulates the dual nature of public key cryptography; it embodies both accessibility and security, wielding the transformative power of mathematics to safeguard information from prying eyes.
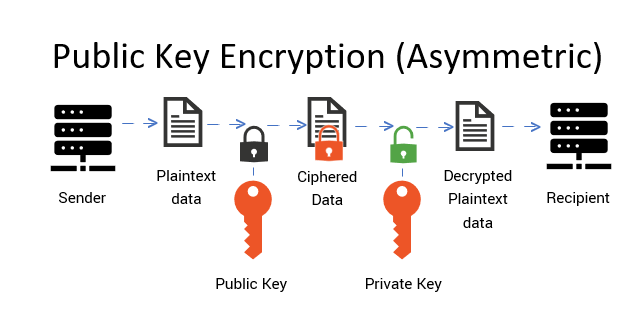
In essence, public key cryptography operates on two distinct yet intertwined keys: the public key and the private key. To visualize these keys, consider a letterbox. The public key is likened to the external door of this letterbox, available for all to access; anyone, even strangers, can place their messages within. However, the real magic lies in the private key, akin to the lock nestled inside the letterbox—secure and unseen—accessible only to the rightful owner. It is this careful interplay between the two keys that creates a fortress of trust in the digital realm.
The inception of public key cryptography can be traced back to the 1970s, birthed from the minds of cryptographic pioneers. They envisioned a system that allowed for secure communication without the cumbersome necessity of sharing a secret key beforehand. This innovation came in the form of asymmetric encryption, where one key encrypts data, and another key decrypts it. This marked a pivotal evolution in encryption, granting users the ability to communicate securely over insecure channels like the internet.
To delve deeper into the mechanics, consider how messages traverse this labyrinthine system. When an individual, let’s refer to them as Alice, wishes to send a confidential message to Bob, she utilizes Bob’s public key to encrypt the message. It becomes a digital cipher, a code so intricate that only the corresponding private key, guarded closely by Bob, can unravel it. In this way, even if malevolent interlopers intercept the encrypted message during its transit, they are left with naught but a jumble of indecipherable figures.
The brilliance of this model lies not only in its encryption capabilities but also in its ability to authenticate the sender. Imagine a wax seal utilized by royalty in the past—a unique emblem that signifies authenticity. In public key cryptography, Alice can also “sign” her message with her private key. This signature serves as verification of her identity, allowing Bob to confirm that the message truly originates from her. If he successfully uses Alice’s public key to verify the signature, a bond of trust is formed, reaffirming the integrity of the communication.
One cannot overlook the concept of trust that underpins this entire architecture. With the proliferation of digital communication, trust acts as the cornerstone of interactions. Public key infrastructure (PKI) emerges as a sophisticated framework ensuring this trust remains intact. Certificates issued by Certificate Authorities (CAs) function as digital passports. They vouch for the identity of key holders, lending credence to the public keys by embedding them within a layer of verifiable legitimacy.
As we dissect this intricate system further, it reveals a web of sophisticated algorithms designed to produce pairs of keys that are robust enough to withstand malicious attempts to derive the private key from the public key. Among the most prominent of these algorithms are RSA, DSA, and ECC, each with unique mathematical foundations and varying degrees of security and efficiency. They employ principles rooted in number theory, such as factoring large integers or the difficulty of solving discrete logarithms.
Despite its numerous advantages, public key cryptography is not without challenges. The very strength that allows it to secure communications—its reliance on complex algorithms—also makes it susceptible to quantum computing threats. Quantum computers, operating on the principles of quantum mechanics, have the potential to execute certain calculations at incomprehensible speeds, thereby rendering classical encryption methods vulnerable. This looming reality has sparked the race for quantum-resistant algorithms, ensuring that security persists even in the face of groundbreaking technological advancements.
The landscape of public key cryptography also introduces a curious paradox—the balance between convenience and security. Users today crave seamless experiences while demanding protections against evolving cyber threats. This call for adaptability has led to a plethora of applications, from secure web browsing with HTTPS to encrypted communications through applications like Signal and WhatsApp. In this dynamic interplay, public key cryptography proves invaluable, merging the essence of security with the demands of user-friendliness.
In conclusion, public key cryptography stands as a monumental pillar of digital security. Through its intricate lock and key analogy, it reveals an elaborate world where data integrity, authentication, and trust converge. As we journey through the digital landscape, this cryptographic marvel not only secures our communications but fosters trust in an era fraught with uncertainties. It encapsulates the fundamental human desire for privacy—a sanctuary where secrets can be shared without fear. As we advance further into the digital age, understanding the mechanisms behind these locking mechanisms will become imperative to navigate the vast expanse of our interconnected lives.








Leave a Comment