Encryption serves as a bulwark against unauthorized access and serves to maintain confidentiality. In understanding how much it protects, one must delve into the intricacies of the different types of encryption methods: symmetric, asymmetric, and triple encryption. Each has its unique characteristics, which dictate the number of cryptographic keys employed.
Symmetric Encryption is the most straightforward of the three methods. This approach utilizes a single key for both encryption and decryption processes. The core principle is simple: the same key that scrambles the plaintext into ciphertext also unscrambles it back to its original form. This method is notably efficient, especially for encrypting large amounts of data since the operations involved are less computationally intensive compared to alternatives. However, the simplicity of symmetric encryption bears inherent vulnerabilities. If the key is compromised, an unauthorized party gains access to both the encrypted data and the means to decrypt it. Thus, secure key management becomes imperative in symmetric systems.
For example, algorithms such as Advanced Encryption Standard (AES) and Data Encryption Standard (DES) illustrate the widespread application of symmetric encryption in various sectors, from banking to personal communication.
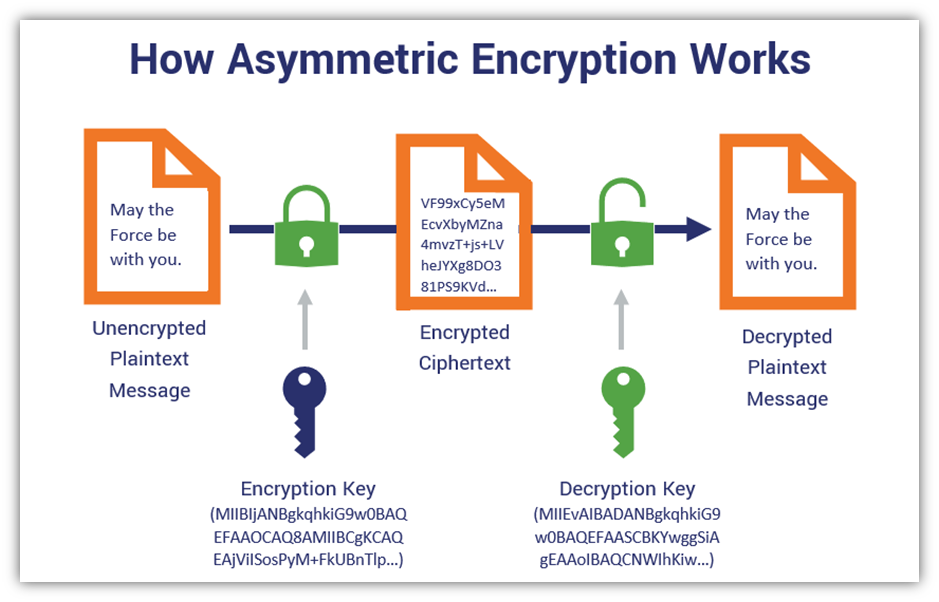
Asymmetric Encryption, on the other hand, introduces a more complex paradigm using a pair of keys: a public key and a private key. The public key is disseminated widely, enabling anyone to encrypt messages intended for the key owner; however, only the corresponding private key can decrypt those messages. This mechanism cultivates an environment where secure communications can occur without the need to exchange a secret key beforehand. As a result, asymmetric encryption significantly reduces the risks associated with key distribution.
This method is foundational for establishing secure connections over the internet, such as with HTTPS and SSL/TLS protocols. As an illustration, RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) exemplify asymmetric encryption methods widely utilized in secure online communications. The dual-key system of asymmetric encryption, while introducing computational overhead, provides deposits of cryptographic security that symmetric counterparts often lack.
The divergence between symmetric and asymmetric encryption underscores a crucial takeaway: the number of keys employed. Symmetric encryption relies on a solitary key, whereas asymmetric employs two distinct keys. This bifurcation creates a framework that allows users to balance security needs against operational efficiency.
Triple Encryption emerges as a more elaborate strategy, typically operating upon the foundation of symmetric encryption. The concept involves applying a symmetric encryption algorithm multiple times to increase the security of the data. An exemplary methodology in this area is known as Triple DES (3DES). Here, the original data is encrypted three times using the DES encryption standard and either a unique key for each encryption or a repeating key.
As a result, the effective key length and the depth of security are significantly enhanced. Triple DES employs three keys if different keys are used for each encryption round, or it can use a single key for all three encryptions, thus having the potential to generate either three or one key accordingly. Nevertheless, the computational expense and latency from processing the data three times can deter its use in real-time applications.
To summarize the key mechanics of these encryption methodologies:
- Symmetric Encryption: Utilizes one key, focusing on speed and efficiency.
- Asymmetric Encryption: Utilizes two keys, enhancing security particularly in key transmission.
- Triple Encryption: Typically employs three keys or instances of encryption using a symmetric algorithm to increase security features.
The relevance of choosing the appropriate encryption method cannot be overstated. In different scenarios, the nature of sensitive information being protected will dictate the chosen technique. Sensitive personal correspondence, for instance, might benefit more from asymmetric encryption given its robustness against interception. In contrast, large databases may leverage symmetric encryption due to its efficiency in handling large volumes. Furthermore, when implementing enhanced security measures, organizations can resort to triple encryption in environments where data sensitivity is paramount.
System architects and security professionals must remain well-versed in the mechanisms underlying these encryption types. By understanding the various keys employed in each, they can make informed decisions that will yield optimal security solutions for their specific requirements. The landscape of cybersecurity is continuously evolving. As threats to data integrity and confidentiality grow more sophisticated, so too must the strategies employed to combat them.
A nuanced grasp of symmetric, asymmetric, and triple encryption empowers stakeholders to safeguard their assets effectively, ensure compliance with privacy regulations, and fortify the foundations of trust in their digital communications. Thus, the discussion surrounding key usage in encryption isn’t just an academic exercise; it is a vital component in the ongoing quest for a secure digital realm.








Leave a Comment