Quantum cryptography epitomizes a convergence of physics and information security. It harnesses the principles of quantum mechanics to create cryptographic systems that are fundamentally secure against eavesdropping and other forms of cyber intrusion. As our digital world continues to expand and evolve, the necessity for resilient encryption methodologies grows increasingly paramount. This exploration delves into the nascent realm of quantum cryptography, elucidating its mechanisms, applications, and implications for future security paradigms.
At the heart of quantum cryptography lies the phenomenon of quantum key distribution (QKD). QKD allows two parties to generate a shared, secret random key that is impervious to any form of interception. The cornerstone of this process is the use of quantum bits, or qubits, which can exist in multiple states simultaneously, a trait known as superposition. Moreover, the act of measuring a qubit, which is part of the communication between the parties, fundamentally alters its state due to a property called ‘observer effect’. This ensures that any attempt at eavesdropping can be detected, as the presence of an unauthorized observer would introduce anomalies into the shared key, alerting the legitimate participants to the breach.
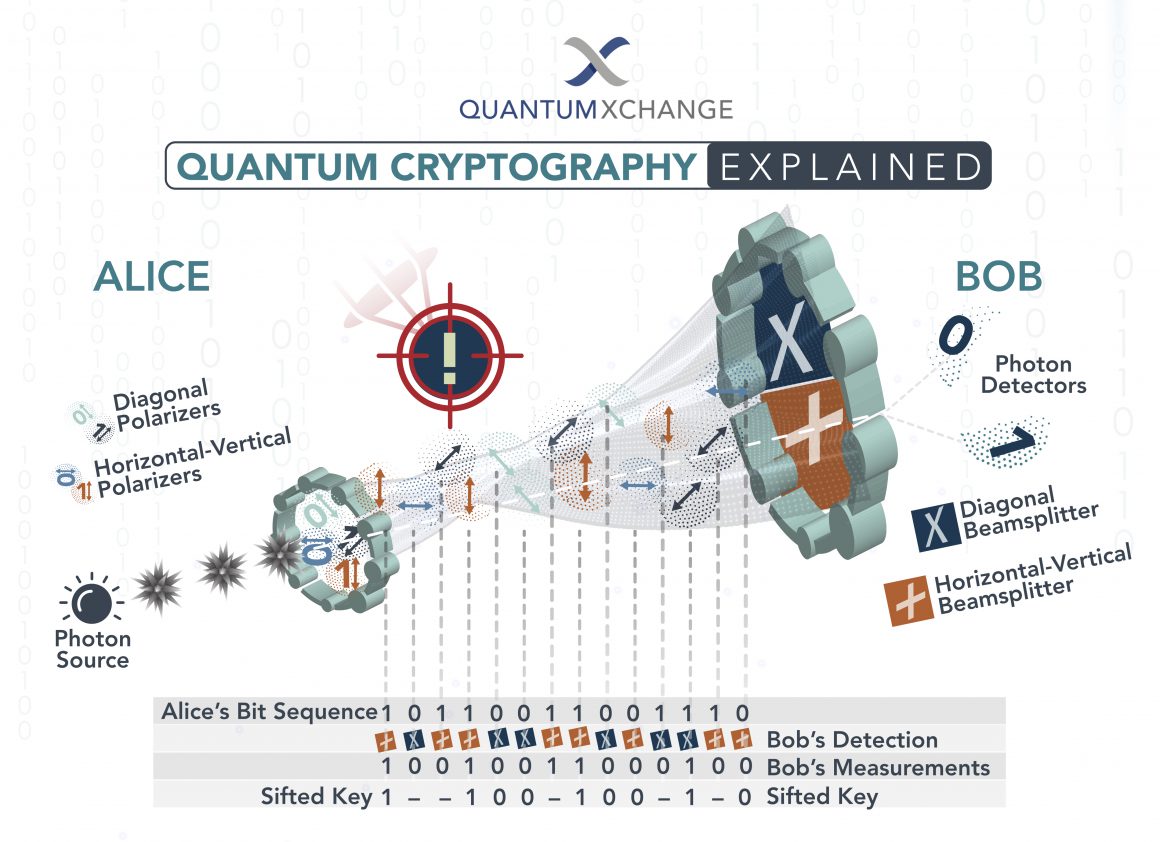
The most widely studied and implemented protocol for QKD is the BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984. In this protocol, the sender (commonly referred to as Alice) encodes the key using two bases of polarization states of photons. The receiver (Bob) measures these photons, thus generating a shared key that can be verified for its integrity. The elegance of the BB84 protocol is augmented by its computational simplicity and the robust security it offers, paving the way for experimental implementations that serve as proof of concept.
Beyond QKD, quantum cryptography extends into the realm of post-quantum cryptography and quantum-secure communications. As advancements in quantum computing threaten the foundational algorithms that protect today’s digital communications—algorithms like RSA and ECC (Elliptic Curve Cryptography)—the need for new cryptographic frameworks becomes even more pressing. Post-quantum cryptography aims to develop encryption systems that remain secure against the capabilities of quantum computers, thereby ensuring that sensitive information remains protected despite technological advancements.
The realization of quantum cryptography is not confined to theoretical frameworks; rather, it is increasingly being operationalized across various sectors. Telecommunications companies are experimenting with QKD to bolster the security of their networks. For example, pilot projects in secure telecommunications have successfully integrated quantum key distribution systems into operational architectures. These implementations showcase how quantum cryptography can provide a superior layer of security in transmission protocols.
Moreover, quantum cryptography has significant implications for national security. Governments and military organizations are investing in quantum technologies to safeguard sensitive intelligence communications. The prospect of employing quantum-secure networks for military applications underscores the geopolitical importance of quantum encryption methods. By utilizing QKD, nations can protect their most confidential data from adversarial entities, rendering conventional interception techniques futile.
Financial institutions are also poised to benefit from quantum cryptography. As the landscape of cyber threats grows ever more sophisticated, banks and financial service providers recognize the urgency of implementing quantum-resistant security measures. The transparency and immutability offered by quantum key distribution can help mitigate the risk of data breaches and financial fraud. This prescriptive shift towards quantum cryptography not only safeguards customer transactions but also fortifies institutional trust in digital environments.
However, the transition to quantum cryptography is not devoid of challenges. The implementation of quantum networks requires a robust infrastructure that can support the delicate nature of quantum communications. The inherent fragility of qubits during transmission raises issues related to distance and signal degradation. Current QKD systems are limited in range, necessitating the deployment of repeaters or satellite systems to extend their reach. Research is ongoing in hybrid systems that integrate classical and quantum networks, offering pathways for gradual adoption.
Another hurdle to the widespread adoption of quantum cryptography lies in regulatory and standardization frameworks. The exciting potential of this technology has outpaced existing legal and procedural stipulations, leaving ethical dilemmas in its wake. Questions regarding compliance, data sovereignty, and interoperability must be addressed to allow for a seamless integration of quantum cryptography into existing systems.
As we cast a gaze towards the future, the influence of quantum cryptography is likely to be profound and far-reaching. The fusion of quantum mechanics with encryption technology offers tantalizing possibilities for revitalizing information security. As threats evolve, so too must our defenses. By harnessing the unique properties of quantum states, organizations can forge ahead into a future marked by unprecedented levels of communication security.
In conclusion, quantum cryptography represents the vanguard of secure communications, offering solutions that conventional encryption cannot match. Its applications span a spectrum of industries, heralding a paradigm shift in how sensitive information is protected. While challenges remain, the trajectory of this technology suggests an imminent embedding into the fabric of our digital communication strategies. The vigilant pursuit of knowledge in quantum cryptography will determine the resilience of future networks against the specter of cyber threats.








Leave a Comment