Hashing plays an integral role in the realm of cryptography, forming the bedrock of modern data integrity and security protocols. One of the more intriguing applications of hashing in contemporary settings can be found within the framework of cryptocurrency platforms, exemplified here by Zilliqa. This discussion will delve into the multifaceted utilization of hashing in cryptographic systems, explore its significance, and illuminate the function that it serves, particularly in the context of Zilliqa’s architecture.
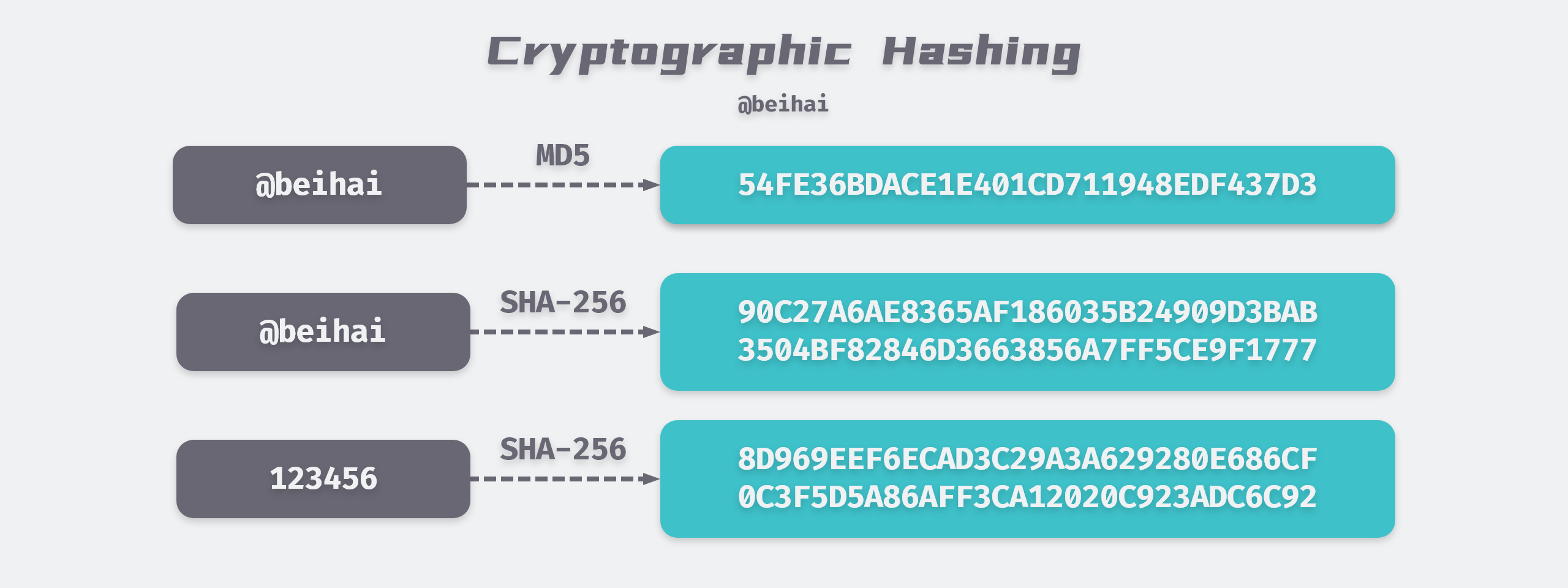
At its core, hashing is a process that takes input data—an arbitrary string of bytes—and transforms it into a fixed-length string of characters, which is commonly referred to as a hash. This transformation is executed through complex mathematical functions and exhibits various distinct properties that render hashes suitable for cryptographic utilization. One of the most prominent characteristics is irreversibility: given a hash output, it is computationally infeasible to reconstruct the original input. With this principle, hashing lays the groundwork for secure verification processes, ensuring that any alterations to the original data will yield a different hash value.
Moreover, the avalanche effect emerges as another critical feature of hashing. A slight modification in the input data engenders a dramatic change in the resultant hash. This property is paramount in ensuring that even minimal alterations in digital information can be easily detected. Consequently, it is widely employed in situations where data integrity is paramount, such as in digital signatures and file verification processes. Data integrity is particularly crucial within blockchain technology, where transparent and tamper-proof records are essential.
The Zilliqa network, a pioneering blockchain platform, employs hashing mechanisms in a rather innovative manner. Utilizing a unique sharding architecture, Zilliqa significantly enhances its throughput and scalability compared to traditional blockchain systems like Bitcoin and Ethereum. Hash functions are employed not only to secure transactions but also to facilitate the sharding process itself. Each shard in the Zilliqa network operates semi-independently, processing its transactions by employing hashing to maintain the integrity of data across the network. But how do these shards maintain coherence in a decentralized environment?
Each transaction submitted to the Zilliqa network is first validated and then cryptographically hashed. These hashes ensure that any fraudulent activity or alteration of transaction details can immediately be identified. Once the transactions are assembled, they are grouped into blocks, and the entire block’s hash represents a unique fingerprint of all transactions within that segment. As new blocks are created and linked chronologically, they form a cryptographic chain that fortifies the security of the entire blockchain. This cohesive structure not only deters tampering but also provides efficient access to transaction histories.
Another significant aspect where hashing becomes pivotal relates to consensus mechanisms. Zilliqa employs a variation of Proof of Work (PoW) for the initial coordination of the network. Miners compete to solve complex mathematical problems—essentially finding a nonce that generates a specific hash characteristic for a block, thus validating the transaction block. This mechanism ensures that malicious entities cannot easily overtake the network and reinforces its overall resilience. However, could the reliance on PoW lead to excessive energy consumption in the long run?
While the advantages of hashing in cryptography are substantial, the potential vulnerabilities must be acknowledged. One notable concern is the susceptibility to collision attacks, where two different inputs yield the same hash output. While contemporary cryptographic hash functions, such as SHA-256, are designed to minimize this risk, advancements in computational power and algorithms pose inherent challenges. Hence, the cryptographic community continuously assesses and updates hashing algorithms to enhance security and counteract emerging threats.
Additionally, as Zilliqa and other blockchain systems evolve, they invariably face the conundrum of maintaining performance without compromising security. The balance between rapid transaction processing and robust encryption practices presents a compelling quandary. Striking this balance is pivotal for the adoption of blockchain technologies in mainstream applications, ranging from financial transactions to supply chain management.
In summation, hashing is a cornerstone of modern cryptographic techniques that facilitate the security and integrity of digital information. Its application in systems like Zilliqa exemplifies how hashing contributes to groundbreaking advancements in blockchain technology. As evidence of increasingly sophisticated threats arises, the evolution of hashing algorithms will remain crucial in fortifying cryptographic systems against emerging vulnerabilities.
As we gaze into the future of cryptography, one might ponder: could the next generation of hashing algorithms substantially alter the way we perceive and implement security protocols? The interplay of technology and cryptography is not a fixed landscape but a continuously shifting arena in which each development beckons new questions and challenges. Thus, the exploration of hashing’s role within this domain remains ever pertinent, urging innovation and vigilance.







Leave a Comment