In the vast digital landscape, akin to an expansive savannah teeming with wildlife, a relentless predator lurks: the brute force attack. This method of infiltrating systems and breaching security protocols is as primitive as it is effective, employing sheer computational brute strength to crack ciphers and passwords with an unyielding tenacity. It is cumbersome, almost visceral in its approach, much like a lumbering elephant charging through dense underbrush, determined to overcome any obstacle in its path. As our world grows increasingly interconnected, understanding the speed and efficiency of such an attack becomes paramount.
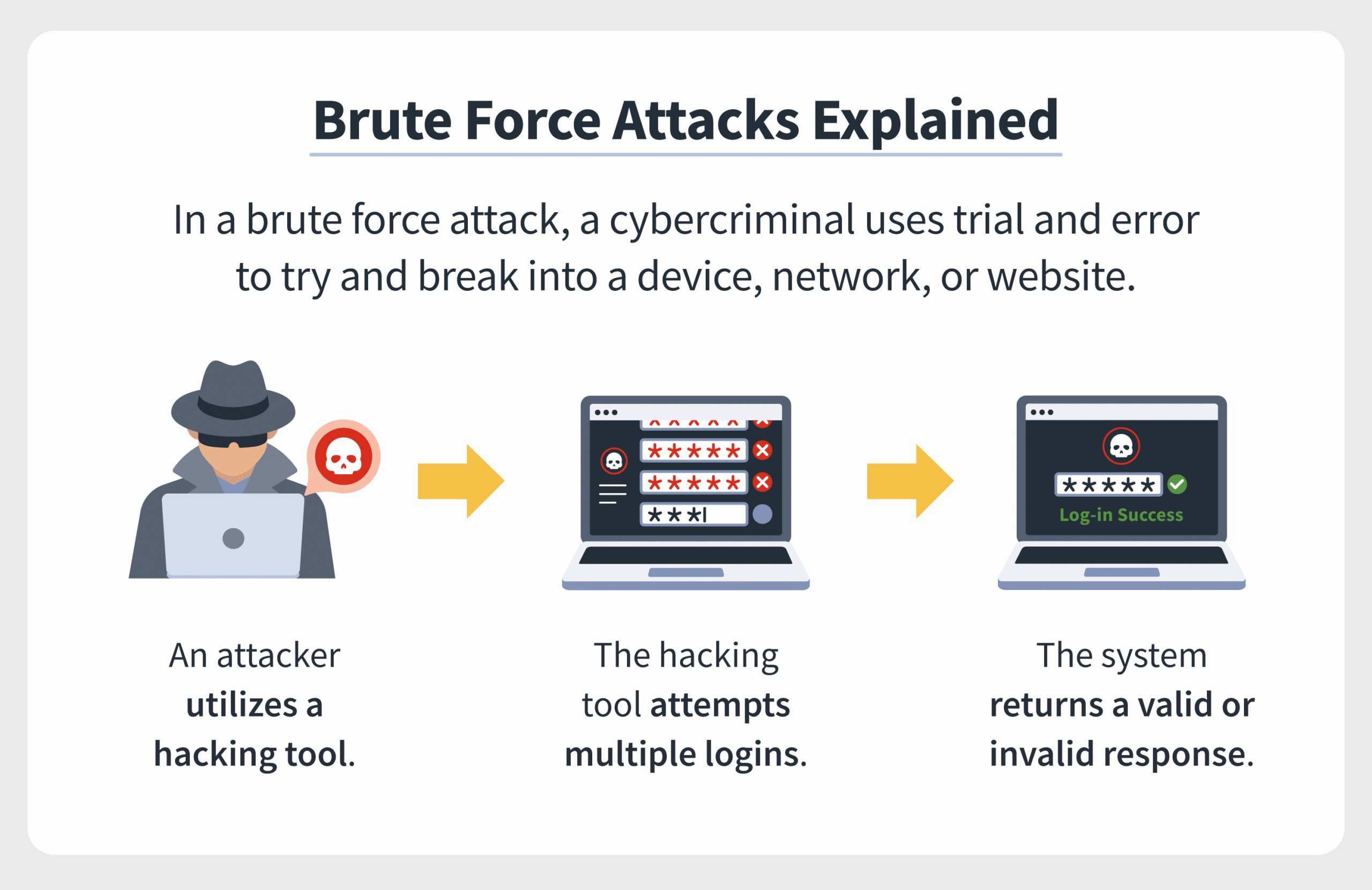
To unpack the intricacies of a brute force attack, we must first define the methodology behind it. Imagine a combination lock, where each turn of the dial represents a potential password. A brute force attack systematically tests every conceivable combination until the correct one is found. The key variable here is time: how rapidly can the attacker attempt each combination? The speed of a brute force attack can vary significantly based on numerous factors, including the complexity of the password and the computational resources at the attacker’s disposal.
At the heart of this problem lies the exponentiation of possibilities. Consider a password composed of uppercase letters, lowercase letters, numbers, and special characters. The potential combinations grow exponentially with every additional character. For example, an eight-character password composed solely of lowercase letters has 26^8, or 208,827,064,576, possible combinations. Introducing uppercase letters, digits, and symbols escalates this figure into astronomical territory. A sophisticated adversary armed with a botnet of thousands of interconnected devices can parallelize the process, launching simultaneous attempts to crack these encrypted doors. Here, like a prides of lions coordinating a hunt, the sheer volume of computational power enables them to penetrate defenses swiftly.
However, the exact speed at which a brute force attack unfolds is contingent not only on the password’s complexity but also on the attacker’s hardware capabilities. A single GPU (graphics processing unit) can attempt thousands of password combinations per second, while cloud-based systems can coordinate hundreds or thousands of additional devices, multiplying their efforts manifold. In this sense, brute force attacks resemble an intricate dance—a ballet of computational prowess and chaotic effort, where every second counts.
Nevertheless, the digital realm has defenses that mitigate such assaults. Modern security protocols often enforce password complexity rules and account lockouts after a predetermined number of failed attempts. These practices serve to slow down the progress of brute force attackers significantly. Such defenses are akin to a fortress with watchtowers and walls reinforced by durable materials; they act as both deterrents and resilience strategies. However, even the most fortified of castles are vulnerable to relentless besieging.
Some might be surprised to learn that a brute force attack can yield results relatively quickly in the context of weak passwords. A simple four-digit PIN, like those often used for mobile devices or ATM cards, can be cracked within minutes. Given there are only 10,000 combinations (0000 to 9999), an attacker with the right tools could cycle through possible combinations at a speed of hundreds or thousands per second, rendering this simplistic security measure alarmingly ineffective.
The potential for rapid success is decreased with more complex algorithms, yet it is never eliminated. The growing power of polarization in computing, specifically through machine learning and artificial intelligence, means that even sophisticated systems must remain vigilant. Imagine a tenacious octopus, employing its intellect to adapt and manipulate its environment in search of its next meal; modern security measures must echo this adaptability to outsmart brute force tactics.
As we navigate further into this technological predation, it is vital to consider human behavior and its relevance in security resilience. Users often exhibit predictability in password creation, gravitating toward easily memorable phrases or common sequences, like “123456” or “password.” These shortcuts dilute the integrity of even the most advanced security systems, creating chinks in the armor that might otherwise withstand a full-scale assault. Thus, education on best practices for password security is an essential component of defense strategy.
Ultimately, the speed of a brute force attack is dictated by multifactorial elements, each intertwining with the next. The juxtapositions of computational prowess, password complexity, and user behavior create a unique tapestry illustrating the ongoing battle between security systems and malicious intent. It is a relentless marathon—where the pace is furious, and each second can herald an eventual breach.
As the digital savannah continues to evolve, so too must our understanding of security measures. Just as the wildlife of the savannah adapts over time for survival, our digital defenses must evolve to counteract the persistent threat posed by brute force attackers. Knowledge remains our most potent weapon in this ongoing confrontation, ensuring that we do not merely react to breaches but navigate the evolving landscape with foresight and resilience.






Leave a Comment