In the ever-evolving landscape of digital communication, the concepts of encryption and encoding frequently emerge, often leading to confusion among individuals and organizations alike. While both techniques serve the purpose of data transformation, their functionalities, applications, and implications are distinctly different. Understanding these differences is not merely an academic exercise—it’s essential for ensuring the integrity, confidentiality, and authenticity of data in an increasingly technology-driven world.
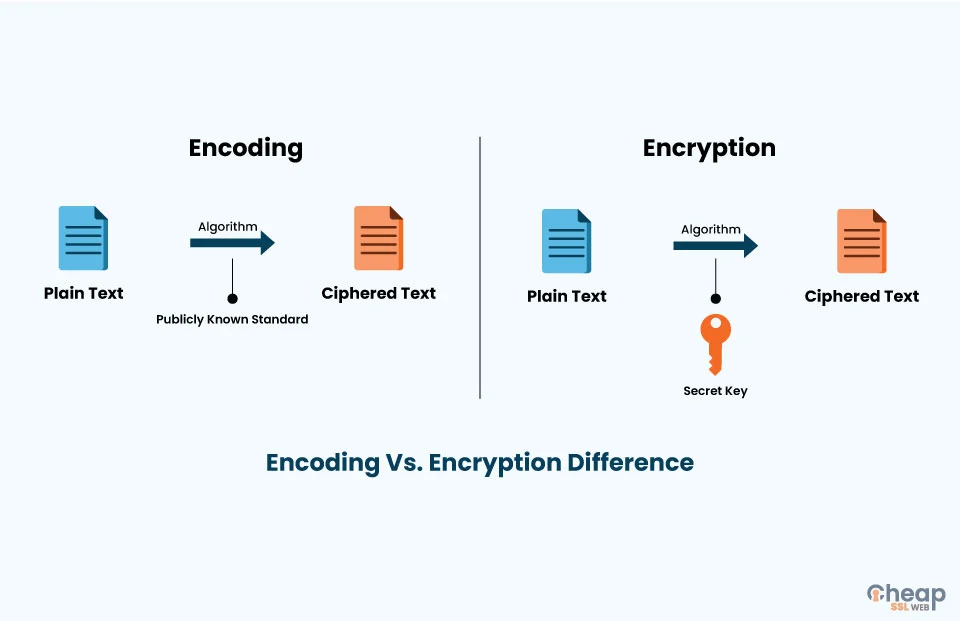
First, let us delineate the foundational principles of encoding. Encoding is primarily a process of transforming data into a specific format using a publicly available scheme. The intention behind encoding is to ensure that data can be properly consumed and understood by different systems or applications. For example, when a text file is encoded in Base64, the raw binary data is converted into a series of ASCII characters, thereby enhancing compatibility across various platforms. This type of data transformation does not provide security; anyone with the decoding scheme can revert the encoded data back to its original form.
Conversely, encryption is inherently a security mechanism designed to protect data from unauthorized access. Encryption algorithms utilize cryptographic keys that change the data into a seemingly unintelligible form. Only individuals or systems possessing the appropriate decryption key can revert the encrypted data to its original state. This disparity is not merely semantic; it encapsulates the fundamental difference in objectives—encoding is about data representation, while encryption is about safeguarding information. Thus, encryption is critical in scenarios where confidentiality and privacy are paramount.
Numerous types of encoding exist, with various applications in data storage, transmission, and processing. Common encoding schemes include ASCII, UTF-8, and Base64. ASCII, for instance, allows a range of characters—whether letters, digits, or symbols—to be represented numerically, making it one of the earliest and simplest encoding schemes. UTF-8 expands upon this by accommodating a more extensive array of characters, thus becoming the predominant encoding method for global digital communications.
In contrast, encryption has spurred a myriad of algorithms that can be categorized into symmetric and asymmetric encryption. Symmetric encryption employs a single key for both encryption and decryption, necessitating the secure exchange of this key between parties. Algorithms such as Advanced Encryption Standard (AES) exemplify this method. Asymmetric encryption, on the other hand, employs two keys—a public key for encryption and a private key for decryption. Public Key Infrastructure (PKI) is often utilized via algorithms like RSA, wherein anyone can encrypt data with the public key, but only the key’s owner can decrypt it with their private key. This multifunctionality plays a critical role in secure communications over the internet, including the operation of SSL/TLS protocols.
The implications of misusing encoding and encryption are significant and warrant careful consideration. Encoding data merely to obfuscate it does not confer security. For instance, using Base64 encoding for sensitive information such as passwords or Personal Identifiable Information (PII) can lead to exploitable vulnerabilities. Anyone with access to the encoded data can decode it easily; this is a notable fallacy that compromises data security.
In stark contrast, the robust nature of encryption provides a defense against unauthorized access, ensuring that sensitive data remains confidential even if intercepted. Businesses employing encryption to secure client data, both in transit and at rest, adhere to regulatory compliance standards such as GDPR or HIPAA, which mandate robust data protection measures. Failure to encrypt such data could result in deleterious consequences, including financial loss and reputational damage.
Moreover, the digital landscape encompasses various use cases for both encoding and encryption that audiences can anticipate investing their attention in. Content creators may delve into technical explorations of how different encoding schemes can affect data transmission efficiency. They may also engage in thoughtful discussions surrounding the ethical implications of encryption, specifically in relation to law enforcement’s demands for decryption assistance. Concerns about maintaining individual privacy versus the state’s obligation to uphold safety will resonate with many readers.
Moreover, in the context of data breaches and cyber threats, the discussion around the importance of robust encryption becomes increasingly pertinent. Readers can expect to find elucidations on how encryption serves as a bulwark against data exfiltration and adversarial manipulation. From case studies highlighting breaches that resulted from inadequate encryption practices to analyses of high-profile incidents where encryption thwarted unauthorized access, the discourse presents both cautionary tales and motivational narratives for implementing stringent encryption protocols.
Summarily, the distinctions between encoding and encryption are profound and consequential. Encoding serves as a method of data representation, primarily concerned with compatibility and utility, while encryption embodies the essence of data security, emphasizing confidentiality and protection from unauthorized access. As individuals navigate this complex digital ecosystem, understanding these differences is paramount. From ensuring compliance with data protection regulations to safeguarding sensitive information, the implications of encoding versus encryption extend far beyond mere technicalities, resonating deeply within the fabric of security and privacy in the digital age.





Leave a Comment