In an age where digital communication permeates every aspect of our lives, the significance of secure encryption cannot be overstated. It serves as the backbone of online security, safeguarding sensitive information from prying eyes and malicious actors. Yet, the intricacies of how secure encryption functions largely remain a mystery to the average individual. This exploration demystifies the world of encryption, seeking to shift perspectives and pique curiosity about the cryptographic mechanisms that operate behind the scenes.
At its core, encryption is the process of encoding information in such a way that only authorized parties can access it. This is achieved through algorithms that transform plaintext—readable information—into ciphertext, which appears as gibberish. The journey from plaintext to ciphertext and back again is underpinned by a blend of mathematical theories, complex algorithms, and cryptographic keys. Understanding these components unveils the marvels of modern cryptography.
The Algorithms: The Heart of Encryption
Encryption algorithms can be categorized into two primary types: symmetric and asymmetric.
Symmetric encryption involves a single key for both encryption and decryption. This implies that both the sender and receiver must possess the same secret key. The challenge lies in securely sharing this key without interception. Advanced Encryption Standard (AES) is a quintessential example of symmetric encryption, widely employed for its efficiency and speed.
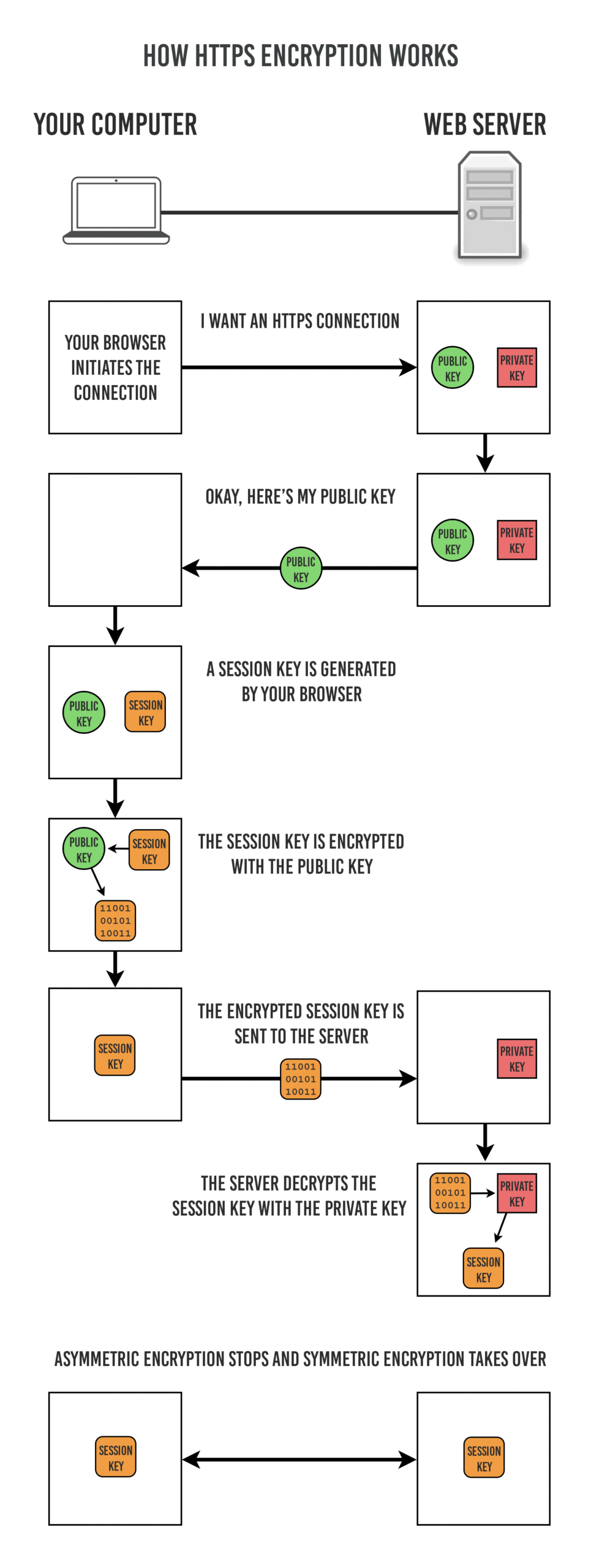
In contrast, asymmetric encryption employs two keys—a public key and a private key. The public key encrypts the data, while the private key decrypts it. This method eliminates the need for the exchange of secret keys, mitigating the risk of compromise. The RSA algorithm epitomizes asymmetric encryption, using the mathematical properties of prime numbers to generate key pairs. The allure of asymmetric encryption lies in its convenience, although it is generally slower than its symmetric counterpart.
The Role of Cryptographic Keys
The cryptographic key is a vital element in the encryption process. It is the seed that enables the algorithm to produce the ciphertext from the plaintext. The strength of encryption relies heavily on key length; longer keys provide greater security as they exponentially increase the number of possible combinations an attacker must navigate to crack the code.
For example, a 128-bit key can produce 2128 combinations—an astronomically high figure—making brute-force attacks impractical. In an era where computing power is continually advancing, migrating to longer keys—such as 256-bit—has become increasingly popular, further bolstering guardianship against unauthorized access.
The Encryption Process: From Plaintext to Ciphertext
The process of encryption, while rooted in complex mathematics, can be broken down into more digestible stages:
- Input Plaintext: The original data that needs encryption.
- Key Selection: The key that will encrypt the plaintext.
- Algorithm Execution: The algorithm processes the plaintext using the selected key, transforming it into ciphertext.
- Output Ciphertext: The final encrypted data that appears nonsensical to anyone who intercepts it without the appropriate key.
This sequence may seem straightforward, but each stage is infused with intricate mathematical transformations, involving substitutions, permutations, and elaborate cryptographic operations that disguise the original information completely.
The Decryption Process: Unlocking the Secrets
Decryption is the obverse of encryption, intricately tied to the encryption method employed. In the case of symmetric encryption, the same key used to encrypt the data is utilized for decryption. Should certainty of the key’s secrecy persist, recovery of plaintext is seamless. Asymmetric encryption presents a different landscape—the data encrypted with the public key can only be decrypted with the corresponding private key, ensuring a one-directional flow that enhances security.
Yet, it is critical to recognize that decryption is not merely a reversal of the encryption process; it involves its own set of algorithmic steps geared towards translating ciphertext back into readable data. This two-pronged process reveals the elegance of encryption: complexity imbued with a purposeful design.
Real-World Applications: Beyond Basics
Secure encryption is ubiquitous in our daily lives, providing the foundation for various applications that require confidentiality. From online banking and e-commerce to private messaging services, encryption is integral to maintaining trust in digital transactions. Behind the scenes, systems like Transport Layer Security (TLS) encrypt data during transmission over the internet, thwarting potential eavesdroppers.
Moreover, encryption plays a critical role in ensuring data integrity. It confirms that the information exchanged has not been altered, thus preserving reliability across various platforms. Various enterprises employ encryption to protect sensitive data from cyber threats, illustrating the necessity of adopting stringent security measures in an increasingly interconnected world.
Challenges and Future Directions
In conclusion, secure encryption operates as a complex yet fascinating mechanism that safeguards information in our digital age. By exploring its algorithms, key usage, and processes, one uncovers the remarkable sophistication that lies beneath the surface. As technology continues to advance, understanding secure encryption becomes increasingly crucial, ensuring that privacy remains an inviolable tenet of our digital interactions.








Leave a Comment