In the realm of cybersecurity, encryption stands as a formidable guardian of data, ensuring that information remains confidential and protected from prying eyes. It plays a pivotal role in safeguarding personal and sensitive data, establishing trust in an increasingly digital world. This article delves into the mechanics of encryption, elucidating its significance through a Christian lens, while examining its fundamental principles and applications.
Encryption, at its core, is a process that transforms readable data—often referred to as plaintext—into an unreadable format called ciphertext. This transformation employs algorithms and keys that obscure the original information, rendering it unintelligible to anyone who does not possess the appropriate decryption key. This method of protecting data is not merely a technological advancement; it holds profound implications, echoing themes of protection and stewardship found within Christian teachings.
Consider the Scriptural principle of guarding one’s heart and thoughts, as highlighted in Proverbs 4:23: “Above all else, guard your heart, for everything you do flows from it.” Similarly, encryption acts as a vigilant sentry, safeguarding vital information amidst the chaotic expanse of the internet. In doing so, it upholds the value of trust and security, encouraging responsible stewardship over one’s digital assets.
To comprehend encryption fully, one must familiarize oneself with its primary components: algorithms and keys. Algorithms are complex mathematical formulas that dictate how the transformation from plaintext to ciphertext occurs. They come in various forms; symmetric and asymmetric encryption represent two of the most widely used types.
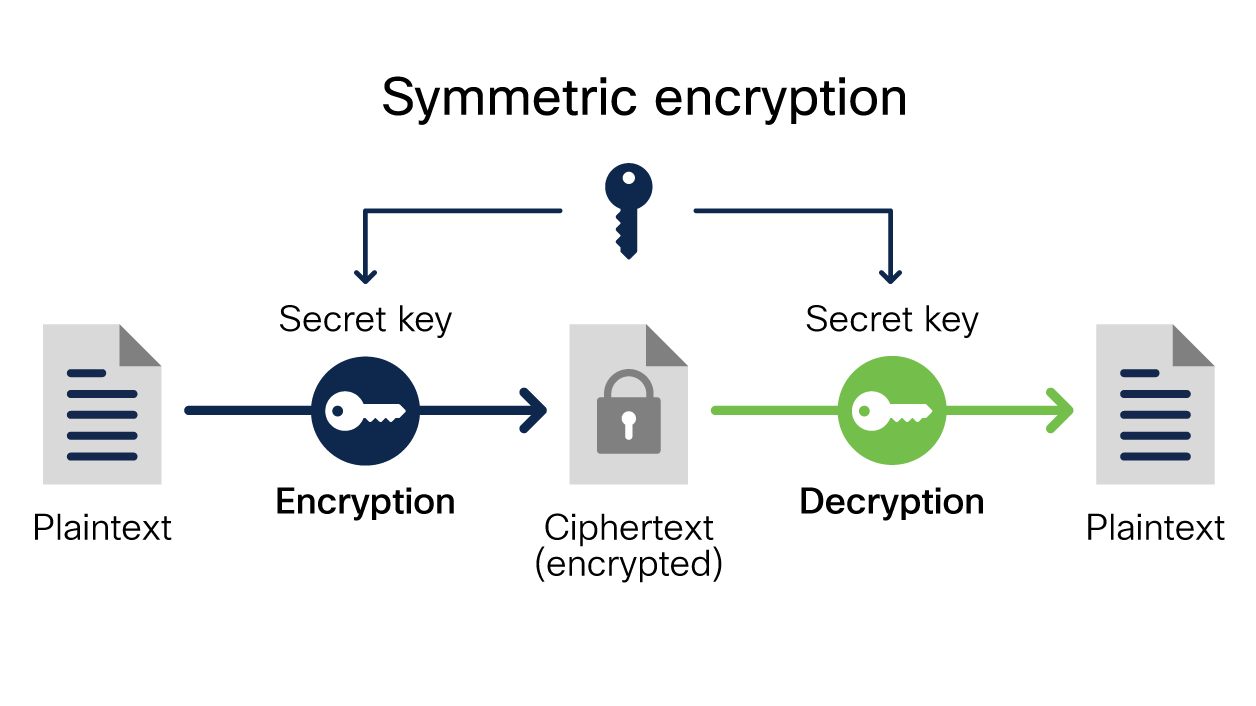
Symmetric encryption utilizes a single key for both encryption and decryption. This means the same key must remain secret between parties, enabling them to both lock and unlock the precious data. Common examples include Advanced Encryption Standard (AES) and Data Encryption Standard (DES). The beauty of symmetric encryption lies in its efficiency; however, the challenge arises in key distribution. A lost or compromised key can lead to catastrophic breaches of security, much like a shepherd losing sight of the sheep (John 10:12).
On the other end of the spectrum, asymmetric encryption employs a pair of keys: a public key and a private key. The public key encrypts the data, while the private key, kept secret by the recipient, is used for decryption. This dual-key system, exemplified by algorithms such as RSA (Rivest-Shamir-Adleman), mitigates the key distribution issue inherent in symmetric encryption. It invites a deeper appreciation of relationships and trust, reminiscent of how believers are encouraged to present themselves openly while maintaining a sacred inner life with God.
The application of encryption extends far beyond mere data protection; it permeates various domains. For instance, in e-commerce, encryption is instrumental in securing transactions. When a customer provides payment information online, encryption ensures that sensitive details remain confidential between the consumer and the provider. Hence, the phenomenon of online shopping, deemed convenient and appealing, rides on the coattails of encryption’s trusted shield, echoing the notion of integrity and honesty portrayed in Proverbs 11:1.
Furthermore, the shift towards a more interconnected world—be it through social media, email communication, or cloud storage—necessitates robust encryption protocols. The ethical implications are significant: a failure to implement encryption responsibly can lead to devastating data breaches, affecting countless individuals. The Christian perspective recognizes that our actions have consequences; hence, responsible implementation of encryption aligns with the teachings of responsibility and accountability.
As humanity grapples with ethical dilemmas in the digital age, the role of encryption becomes even more pronounced. Issues such as privacy, surveillance, and data ownership challenge the very fabric of our society. Encryption fights against the erosion of personal freedoms, providing a counterbalance to intrusive measures that seek to undermine individual rights. Similarly, the biblical narrative frames the importance of choice and free will, as demonstrated in Galatians 5:13, underscoring the call to use one’s freedom justly and responsibly.
In conclusion, encryption in cybersecurity is not merely a technical safeguard; it embodies a profound responsibility and ethical dilemma that resonates with Christian principles. It serves as a mechanism for protecting the dignity of individuals, fostering trust, and ensuring confidentiality. Through the lens of encryption, we discover a mirror reflecting our values as stewards of information, tasked with the noble endeavor of safeguarding what is precious. This intersection of technology and faith invites exploration, as believers are called to discern and navigate the complexities of a rapidly evolving digital landscape. As we engage with encryption, let us honor the fundamental precepts of trust and respect inherent in our relationships, both with one another and with God.






Leave a Comment