In the vast landscape of modern communication and data exchange, encryption and decryption serve as the guardians of our information, akin to the vigilant night watchmen in a sprawling metropolis. As the digital realm expands, so too does the necessity to protect sensitive data from prying eyes and malicious entities. The following exposition endeavors to elucidate the intricate mechanisms by which these two interrelated processes operate, employing metaphoric parallels to provide deeper insight.
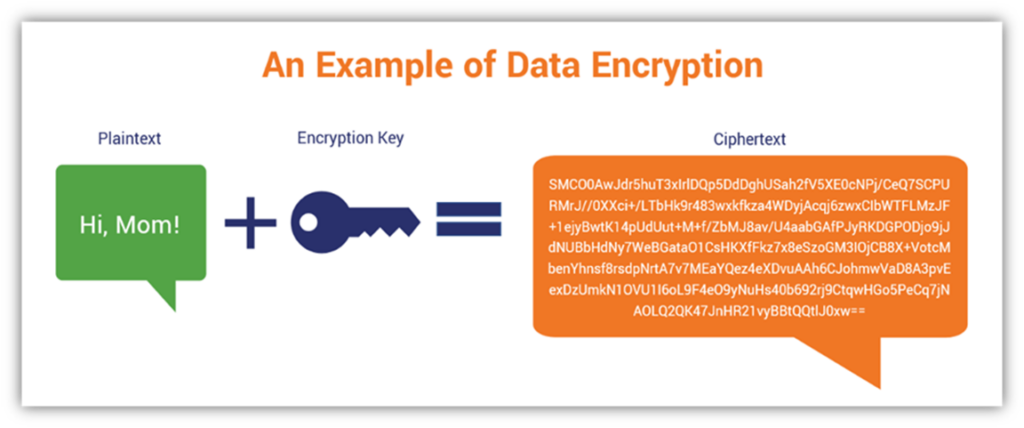
At its core, encryption is akin to transforming a meticulously crafted manuscript into an indecipherable tome filled with cryptic glyphs. When one encrypts information, they effectively rend the fabric of readable content, weaving instead a tapestry of code. This code is unreadable to anyone who does not possess the master key—a unique series of characters capable of unraveling the complexity of the encryption. In this way, encryption operates as a secure vault, safeguarding the treasures of information contained within.
The process of encryption can generally be categorized into two primary methodologies: symmetric and asymmetric encryption. Symmetric encryption relies on a single key for both the encryption and decryption processes. Imagine a locked door that employs the same key to both secure and grant access. Conversely, asymmetric encryption utilizes a pair of keys—a public key, available to all, and a private key, which remains confidential to the owner. This dual-key approach can be likened to a castle with two gates: one is open to the public, while the other, fortified and secret, protects the royal treasures within.
In symmetric encryption, the expeditious nature of the process lends itself well to applications requiring rapid data transfer without the cumbersome weights of complex algorithms. However, the Achilles’ heel of this method lies in the key management; if the key is compromised, the entire fortress of data is rendered vulnerable.
Asymmetric encryption, on the other hand, while slower, offers enhanced security due to its key duality. The public key serves to lock the data away, while the private key acts as the singular means of unlocking it. This ensures that even if the public key falls into the hands of an unscrupulous adversary, they remain powerless without the private key. The delicate interplay of these keys embodies the principle of trust, an essential tenet in any secure communication.
Once data is encrypted, the process of decryption becomes paramount to returning the scrambled message to its original, legible form. This phase is akin to a skilled linguist deciphering an ancient script, painstakingly unraveling the knots of meaning embedded in the encrypted text. Here, the key—whether it be singular or a duo from asymmetric encryption—is wielded as a tool of clarity. With the right key, the cryptic symbols yield their secrets, establishing a pathway back to intelligibility.
Modern encryption relies on algorithms, complex mathematical functions designed to obscure data. Widely adopted algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) employ intricate mathematical principles to complicate the decryption process for anyone lacking the appropriate key. These algorithms function as the architects of security, designing formidable barriers that deter the most determined of intruders.
The implications of encryption and decryption extend far beyond mere data protection; they embody the quintessence of privacy in the digital age. In an era where personal information can be commodified and exploited, encryption stands as a bulwark against breaches and identity theft. Its significance resonates even more profoundly within sensitive domains, such as financial transactions and healthcare information, where confidentiality is not merely a luxury but a necessity.
However, the story of encryption is not devoid of complexity and controversy. While it fortifies our data, it also invites a litany of ethical dilemmas. On one hand, encryption protects innocents from malevolent forces; on the other, it can serve as a shield for nefarious actors, allowing them to operate in the shadows. The tussle between security and transparency embodied in encryption practices evokes a fundamental question: how do we strike a balance between safeguarding legitimate privacy and ensuring accountability?
Pragmatic policymakers must navigate these murky waters, as the discourse surrounding encryption continues to evolve. Legal frameworks must adapt to embrace the dual nature of encryption, championing its protective capabilities while crafting pathways that allow for lawful oversight without infringing upon the rights of citizens. This multifaceted dialogue highlights the importance of collaboration between technologists, ethicists, and legislators as they forge a future that honors both security and freedom.
In conclusion, the intricate dance of encryption and decryption is a sophisticated ballet of mathematics and cryptography, refined through years of advancement and innovation. In this digital age, as we traverse the infinite corridors of cyberspace, these processes remain our vigilant protectors. By converting readable information into cryptic codes, they ensure that our data remains our own, safe from the grasp of those who would exploit it. Thus, the world of encryption and decryption, much like the vigilant night watchmen, continues its unwavering quest to secure the secrets of the digital realm and safeguard the treasures inherent in our information.







Leave a Comment