In the intricate tapestry of our daily existence, cryptography serves as a silent sentinel, ensuring the confidentiality and integrity of our information. While many regard cryptography as an esoteric art, it permeates numerous facets of our lives, often without us even realizing it. This exploration unveils the unseen but omnipresent role of cryptography, shedding light on its mechanics and implications.
The genesis of cryptography can be traced back to ancient civilizations, where ciphers were employed to relay secret messages. Today, however, cryptography has evolved into a sophisticated discipline that underpins countless digital interactions. From securing personal communications to safeguarding financial transactions, its relevance in the modern world is undeniable.
At its core, cryptography is the practice of transforming readable data into an obscured format, known as ciphertext, which can only be reverted to its original form through the application of a specific key. This fundamental principle can be witnessed in various encryption techniques, each with distinct algorithms and methodologies. Among the most widely utilized forms of encryption in contemporary contexts are symmetric and asymmetric encryption.
Symmetric encryption employs the same key for both encryption and decryption. This method, while efficient, presents challenges in key distribution. The necessity of sharing the same key between the parties involved can lead to vulnerabilities if the key is intercepted. However, notable symmetric encryption algorithms, such as the Advanced Encryption Standard (AES), are extensively employed to secure sensitive data in various applications, ranging from corporate data to personal messages.
Conversely, asymmetric encryption introduces a bifurcated key structure: one public key for encryption and a private key for decryption. This complexity facilitates secure communications between individuals who have never met, mitigating the need for shared secret keys. The RSA algorithm, named after its inventors Rivest, Shamir, and Adleman, is a prominent example that highlights the power of asymmetric encryption. With the ability to generate keys that can withstand brute-force attacks, RSA is frequently employed in securing online transactions and digital signatures.
As we navigate the intricacies of the digital landscape, we continuously engage with cryptography in ways that are often overlooked. Consider your morning routine. Upon waking, you may reach for your smartphone to check email or social media. Each time you engage with these platforms, data is transmitted across networks, necessitating a reliable method to keep your personal information secure. Transport Layer Security (TLS), for instance, encrypts the data exchanged between your device and the servers hosting these services.
When making a purchase online, cryptography’s presence becomes even more pronounced. E-commerce platforms employ HTTPS, which is secured through TLS, to protect sensitive information, such as credit card numbers and personal data, during transactions. This layer of security prevents potential data breaches and fosters user trust, essential for the success of online businesses.
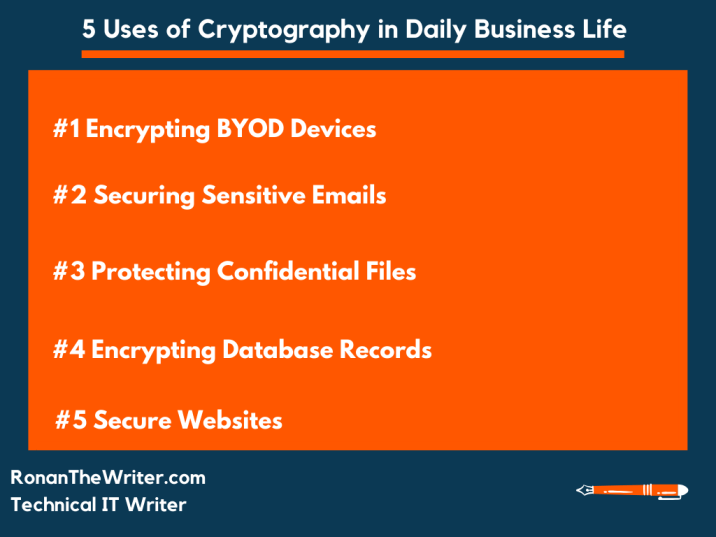
The ramifications of cryptography extend beyond personal interactions and transactions. In the realm of enterprise, organizations leverage encryption to secure vast troves of data. For instance, data-at-rest encryption protects stored information, while data-in-transit encryption safeguards data moving across networks. By implementing stringent cryptographic practices, businesses comply with regulations such as the General Data Protection Regulation (GDPR), ensuring the protection of their customers’ information.
Moreover, in an increasingly interconnected world, encrypted communication channels have become vital for political discourse and social activism. Whistleblowers, journalists, and activists use encrypted messaging applications, such as Signal and WhatsApp, to relay sensitive information without fear of interception. Whispering through the digital void, these messages traverse countless servers, yet remain intelligible only to the intended recipients.
As one contemplates the role of cryptography within this context, an intriguing perspective emerges: we are not merely passive recipients of information but active participants in the protection of our own data. Understanding fundamental cryptographic principles cultivates a sense of empowerment. With knowledge of how encryption safeguards our privacy, we can better navigate the complexities of our digital lives.
However, the advancement of cryptographic technologies is accompanied by challenges. The emergence of quantum computing has instigated a race among cryptographers to develop encryption methods that can withstand the computational prowess of these burgeoning technologies. Quantum key distribution, a pioneering field, holds promise for creating theoretically unbreakable encryption. As this field evolves, it poses critical questions about the future of secure communication.
While cryptography safeguards our interactions and transactions, it also raises ethical concerns. The balance between privacy and security has become a focal point of debate as governments implement surveillance measures intertwined with cryptographic technology. The challenge lies in maintaining the delicate equilibrium between ensuring public safety and preserving individual rights to privacy.
To encapsulate, cryptography is not merely an abstract concept confined to the annals of computer science; it is a vital component of our daily lives, woven into the fabric of our digital experiences. Its applications are diverse and multifaceted, ranging from securing personal communications to bolstering corporate data integrity. As we continue to engage with technology, an understanding of cryptographic principles not only enhances our awareness but also equips us to advocate for our privacy in a rapidly evolving landscape. Cryptography invites us to reconsider our relationship with the digital realm, transforming our perception from passive consumers to informed and empowered users.







Leave a Comment