In an increasingly digitized world, safeguarding sensitive information has transcended mere convenience; it is now a necessity. Cryptography, the art and science of encoding and decoding information, plays an instrumental role in providing this security. From the texts we exchange to the servers that store our data, the invisible tapestry of cryptographic methods intertwines with our daily lives, shaping how we communicate and transact online.
At its core, cryptography serves two primary purposes: confidentiality and integrity. Confidentiality ensures that the information is accessible only to the intended recipients, while integrity ensures that the data remains unaltered during transmission. These principles underpin various cryptographic algorithms, enabling a secure framework for digital interaction. With a myriad of encryption techniques available, understanding how they function is crucial to appreciating their impact.
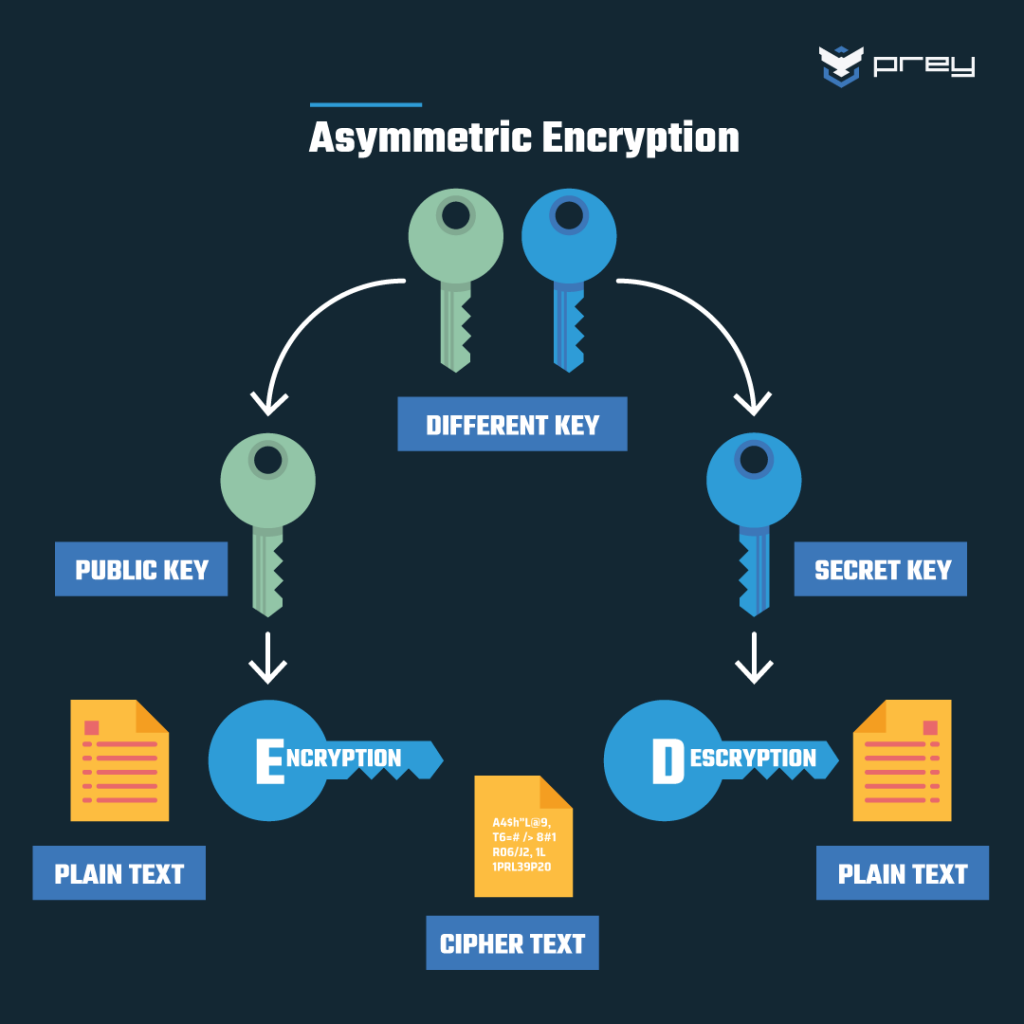
Consider the ubiquity of smartphones. Each time a text message is sent, it traverses a labyrinth of networks before reaching its destination. This journey would be fraught with the potential for interception without cryptographic safeguards. Here, asymmetric encryption, prominently featuring public and private key pairs, becomes our sentinel. The sender encrypts the message with the recipient’s public key; only the recipient, equipped with the corresponding private key, can decrypt it. This process not only secures personal correspondence but also creates a foundational trust among users—a pivotal aspect for maintaining privacy in digital communications.
In instances where speed supersedes the need for intricate security, symmetric encryption algorithms come into play. This method employs a single key for both encryption and decryption. Due to its efficiency, symmetric algorithms like AES (Advanced Encryption Standard) are utilized in various applications, from securing Wi-Fi networks to protecting files on personal computers. However, the reliance on a shared key introduces vulnerabilities in case the key is compromised. Hence, modern systems often employ a hybrid approach, marrying the strengths of both symmetric and asymmetric encryption to enhance security.
Transitioning from personal communications to corporate environments reveals another layer of cryptographic implementation. Server security is paramount, especially for businesses that store vast amounts of sensitive user data. Through Transport Layer Security (TLS), which relies on a combination of both symmetric and asymmetric encryption, data moving between a user’s web browser and a server is meticulously protected from prying eyes. TLS certificates ensure authenticity and encrypt the data in transit, thereby fomenting confidence in e-commerce transactions.
The significance of cryptographic protocols extends beyond mere data protection. It empowers increasingly sophisticated applications like blockchain technology. Embedded within the architecture of cryptocurrencies, blockchain employs cryptographic hashing functions to guarantee the integrity of transactions. Each block in the chain contains a cryptographic hash of the previous block, effectively securing the chain against tampering. This mechanism not only protects financial transactions but also introduces trust in decentralized applications, marking a paradigm shift in how data integrity can be preserved.
In a more intricate application of cryptography, digital signatures emerge as a powerful tool for authentication. They utilize asymmetric encryption to validate the origin and content of digital communications. By affixing a digital signature to a document, a sender can provide unequivocal proof of authorship. This technology underpins critical practices in fields like law and finance, where the authenticity of documents is paramount. Digital signatures not only assert trustworthiness but also enhance accountability in digital environments.
As the Internet of Things (IoT) proliferates, so too does the need for robust cryptographic solutions. Each device that connects to the internet introduces potential vulnerabilities, necessitating secure communication channels. Implementing lightweight encryption algorithms suitable for resource-constrained devices is vital. This scenario illustrates the adaptive nature of cryptography; it not only evolves to meet the demands of emerging technologies but also ensures the secure interconnectivity of a multitude of devices, from smart thermostats to health monitoring wearables.
Nevertheless, the discourse surrounding cryptography is not without challenges. As cyber threats continue to evolve, the arms race between cryptographic techniques and malicious actors intensifies. Advanced persistent threats (APTs) and sophisticated phishing attacks exemplify the need for perpetual vigilance. However, by fostering a culture of awareness about cryptographic principles, individuals and organizations can stay one step ahead. Regular updates of cryptographic protocols and robust password policies are essential for mitigating risks and safeguarding information.
In conclusion, cryptography is an indispensable pillar within the framework of modern security practices. Its omnipresence shapes our everyday experiences, influencing how we maintain privacy, authenticate identities, and secure sensitive transactions. As society becomes increasingly reliant on digital infrastructures, investing in understanding and implementing cryptographic solutions becomes not merely advisable but imperative. The narrative is evolving, and with each advancement in cryptography, we take another step toward a more secure digital future.







Leave a Comment