The secure sharing of encryption keys over a network is a paramount challenge in the domain of cryptography. It is a sophisticated process that fundamentally relies on the principles of mathematics, computer science, and increasingly, quantum mechanics. The core dilemma arises from the inherent vulnerability of information transmitted over potentially insecure channels. As such, one must explore the intricacies of key exchange protocols that facilitate the safe dissemination of these critical cryptographic components.
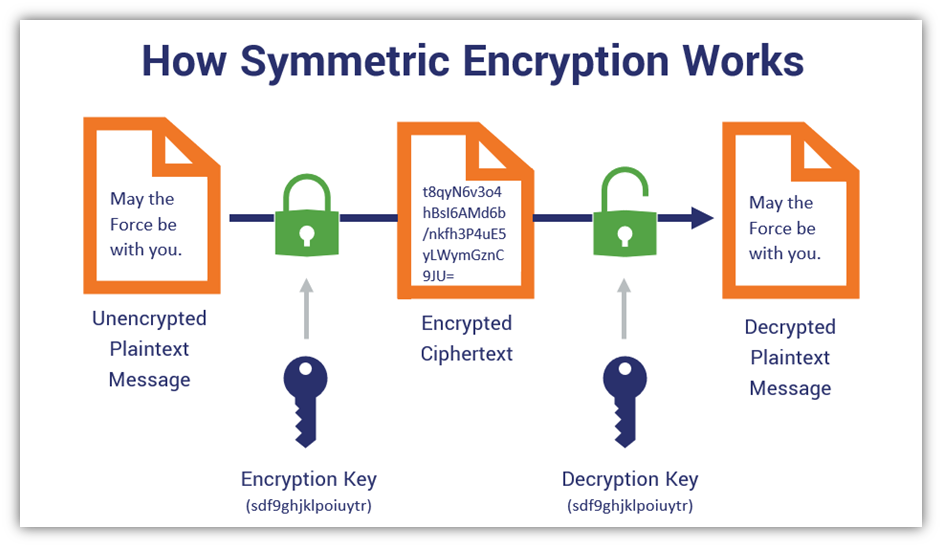
To grasp the nuances of this subject, it is essential first to understand the types of encryption keys in play. Generally, encryption keys fall under two broad categories: symmetric and asymmetric keys. Symmetric keys utilize a single key for both encryption and decryption, necessitating a secure method to share this key between parties. Conversely, asymmetric keys operate on a pair system where a public key encrypts the data, while a private key decrypts it. This architectural dichotomy forms the foundation of various protocols that mitigate risk when sharing encryption keys.
One of the preeminent methods for securely exchanging symmetric keys is the Diffie-Hellman key exchange. Developed by Whitfield Diffie and Martin Hellman in 1976, this groundbreaking protocol allows two parties to establish a shared secret over an insecure channel without prior sharing of a key. The mechanism relies on the mathematical principles of modular arithmetic and discrete logarithms, ensuring that even though the exchange occurs over an unsecured medium, an eavesdropper cannot feasibly derive the shared key.
The genius of the Diffie-Hellman exchange lies in its reliance on the difficulty of the discrete logarithm problem. Each party selects a secret integer, computes a corresponding public value, and shares this public value with the other party. After exchanging these values, both parties can independently compute the shared secret without ever transmitting it directly. This process highlights a pivotal realization in cryptography: the key can be generated without transmission, thereby thwarting potential interception.
Despite its merits, Diffie-Hellman is not impervious to all threats. It is susceptible to man-in-the-middle attacks, wherein a malicious actor positions themselves between the communicating parties to intercept and alter the exchanged values. To counter this vulnerability, protocols such as Transport Layer Security (TLS) incorporate additional mechanisms like digital signatures. Such signatures authenticate the parties involved and verify the integrity of the messages exchanged. Thus, even if an interceptor attempts to manipulate the parameters, the deception would be readily apparent.
Moreover, the application of public key infrastructures (PKI) serves as a bulwark against impersonation. PKI involves a network of entities that issue digital certificates, thereby linking public keys to the identities of the key holders. This layering ensures that the legitimacy of the public keys can be verified, drastically reducing the chances that an adversary could successfully hijack the key exchange process. PKI is integral to establishing trust in online communications, particularly in scenarios requiring sensitive data transmission.
As technology evolves, so do the challenges associated with key sharing. The advent of quantum computing looms large over traditional cryptographic protocols. Quantum computers wield the potential to solve mathematical problems that are currently intractable for classical computers, posing a significant risk to protocols reliant on discrete logarithm problems. In response, researchers are actively exploring quantum-resistant algorithms to enhance the resilience of key exchange methods against such formidable adversaries.
The advent of quantum key distribution (QKD) exemplifies the novel approaches emerging to address these challenges. QKD utilizes the principles of quantum mechanics to facilitate secure communication. By leveraging the properties of quantum bits (qubits), any attempt to measure or intercept the key results in observable disturbances. This inherent trait of quantum mechanics means that the presence of an eavesdropper can be detected, offering a level of security unparalleled by classical methods.
Nevertheless, the practical implementation of QKD remains fraught with logistical hurdles. Issues such as limited operational range, the complexity of quantum technology, and the need for specialized infrastructure make widespread adoption a current limitation. Addressing these issues could unlock the broader applicability of quantum cryptography in securing key exchanges in the future.
In addition to technological advancements, the human element remains a critical factor. End-user education on the importance of secure practices, such as utilizing strong and unique passwords, can enhance overall security. Furthermore, the implementation of two-factor authentication as an adjunct to encryption enhances defenses as it adds an additional verification layer. This multifaceted approach illustrates how security is not a linear problem; it is equally a cultural and behavioral challenge as it is a technical one.
In conclusion, the sharing of encryption keys over a network without interception is a complex task that intertwines mathematics, technological innovation, and human behavior. While protocols like Diffie-Hellman and innovations such as QKD present promising avenues for secure key exchange, the evolving landscape of cryptographic challenges necessitates continual vigilance and adaptation. The fascination with secure communications stems not merely from the mechanics of encryption but also from a broader understanding of trust, identity, and the relentless pursuit of security in an uncertain world.








Leave a Comment