In the realm of cryptography, security is paramount. Among the myriad of techniques employed to protect data, hashing and HMAC (Hash-based Message Authentication Code) stand out as fundamental concepts. Their respective functions within cryptographic applications evoke intriguing discussions regarding not only their security features but also the subtle nuances that differentiate them. This article contemplates the inherent dichotomy between hashing and HMAC, exploring which of the two mechanisms offers superior security for digital communications.
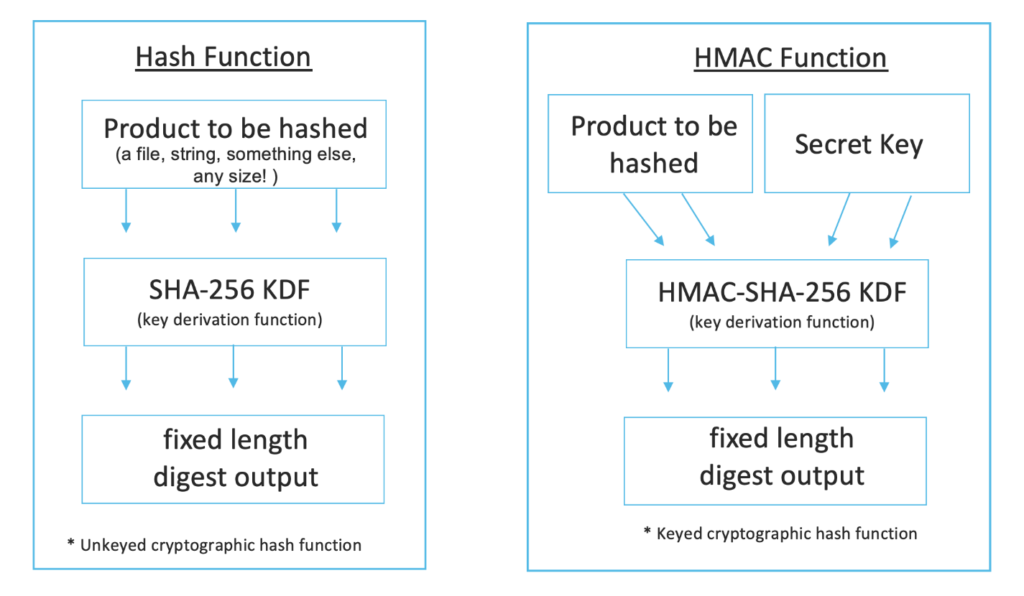
At the core of any discussion on cryptographic security, it is essential to define the concepts of hashing and HMAC. Hashing refers to the process of transforming input data (or a message) into a fixed-size string of characters, which is typically a sequence of numbers and letters. This transformation is achieved through a hash function, such as SHA-256. The primary characteristic of a dependable hash function is that it should produce a unique output for a unique input; thus, even a slight alteration in the input data should yield a considerably different hash result.
Conversely, HMAC builds upon the foundation of hashing by introducing an additional layer of security. It employs a hash function in conjunction with a secret key, effectively generating a code that not only validates data integrity but also authenticates the origin of the data. This mechanism ensures that the recipient can verify that the message has not been altered in transit and that it originates from an authenticated source. The integration of the secret key is crucial; it significantly amplifies the security aspects that a standard hash function cannot guarantee by itself.
One might posit that since HMAC incorporates a secret key, it must inherently be more secure than traditional hashing. A critical distinction arises when assessing the potential vulnerabilities that each method may be subject to. Hashing functions, while effective at data integrity checks, are vulnerable to collision attacks. A collision occurs when two distinct inputs produce the same hash output. This vulnerability can be exploited by adversaries, enabling them to substitute a malicious message in place of a legitimate one without detection. Noteworthy instances, such as the collision flaw discovered in MD5 and SHA-1, underscore the necessity for cryptographic practitioners to migrate towards more robust hash functions.
HMAC, however, circumvents the susceptibility to collision attacks by adding the secret key into the computational mix. The integration of the key ensures that even if two different sources produce identical messages, the resulting HMAC will differ based on the respective keys employed. Additionally, the cryptographic community regards the construction of HMAC safeguards against common cryptographic attacks, such as length extension attacks, where an attacker can manipulate a hash by appending additional data. By requiring a secret key, HMAC blunts such attack methods, establishing deeper trust in its efficacy.
Moreover, the adaptability of HMAC allows for flexibility in the choice of underlying hash functions. This functionality empowers users to pair HMAC with any secure hash function, creating a spectrum of security levels. For instance, one can employ HMAC with SHA-256, thereby benefitting from the robustness of this hash function while instilling the additional security offered by HMAC. Such versatility is not intrinsic to basic hashing techniques, which are constrained by the properties of the singular hash function utilized.
However, the superiority of HMAC over traditional hashing does not imply the complete obsolescence of hashing functions. Hashing remains a valuable tool for many applications where authentication is not a primary concern—such as file integrity verification, checksums, and digital signatures. In these instances, the speed and efficiency of hashing may serve as sufficient criteria, recognizing that its vulnerabilities do not pose significant risks in the outlined contexts. Understanding these distinct applications illuminates the broader spectrum of cryptographic methodologies.
Yet, the discussion inevitably circles back to the intricacies of security principles. It is pivotal to acknowledge that the strength of HMAC is contingent upon the confidentiality and complexity of the secret key implemented. If a weak or easily guessable key is used, the purported advantages of HMAC diminish significantly. Consequently, adhering to best practices in key management creates a critical layer of defense, ensuring that security measures align with desired outcomes. This highlights an overarching theme in cryptographic systems; they are only as resilient as their weakest element.
Ultimately, the question of whether HMAC is more secure than conventional hashing involves multifaceted considerations. While HMAC undeniably offers enhanced security due to its incorporation of a secret key and resistance to various cryptographic attacks, one must also weigh the context of deployment against the specific requirements of the system in question. Thus, the credibility of HMAC comes not solely from its mechanisms but from its implementation within a rigorous security framework. Cryptographic safety encapsulates not only the tools employed but also the protocols strung around them, emphasizing that security should be seen as a holistic construct.
In summary, HMAC excels over standard hashing in terms of security due to its key-dependent nature, providing comprehensive data integrity and authenticity assurances. However, the context matters. The implementer must remain vigilant, as the overall security posture depends on numerous interrelated elements across the cryptographic landscape. In a world increasingly dominated by digital transactions, understanding the dichotomy between HMAC and hashing becomes vital in safeguarding sensitive information against evolving threats.






Leave a Comment