In the realm of cryptography, hash functions serve as pivotal components for ensuring data integrity and authentication. These cryptographic constructs convert input data, regardless of its size, into a fixed-size string of characters, often represented numerically. The critical caveat is that hash functions are designed to ideally yield a unique output for every unique input. However, the paradox arises when considering hash collisions—instances where two disparate inputs produce the same hash output.
Understanding hash collisions is fundamental for various applications such as digital signatures, data integrity checks, and password storage. This article assesses the implications and mechanics of hash collisions, examining their significance, ramifications, and countermeasures against potential vulnerabilities.
The Nature of Hash Functions
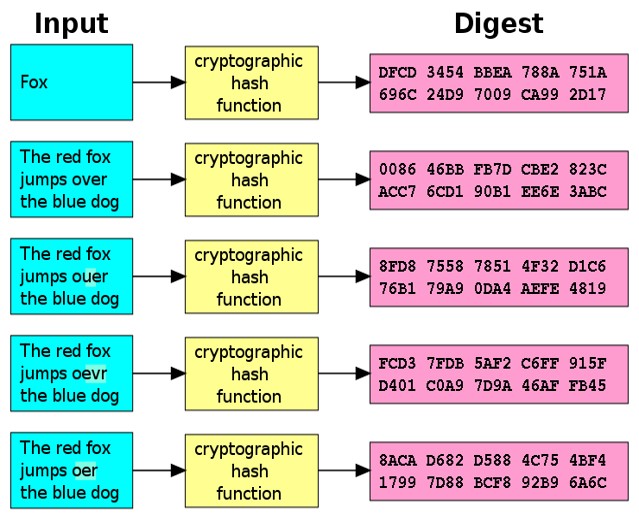
Hash functions operate on the principle of determinism, wherein the same input consistently produces the same output. Most hash functions are designed to be fast and efficient, encouraging their utilization in diverse applications, from cryptography to data retrieval. Notable examples include MD5, SHA-1, and the more robust SHA-256, each varying in complexity and security levels.
Central to their utility is the notion of collision resistance, a property that ensures it is computationally infeasible to find two different inputs that hash to the same output. However, the pigeonhole principle—a simple yet profound concept in mathematics—implies that if a hash function produces a fixed-length output (the digital fingerprint), the finite number of possible hashes will inevitably lead to collisions given an infinite set of inputs. This phenomenon exposes a chilling aspect of hash functions.
The Mechanisms Behind Hash Collisions
Collisions can be attributed to various factors, including the inherent limitations of the hashing algorithm employed and the sheer volume of possible inputs. Attacks aimed at realizing collisions often fall under two camps: birthday attacks and second preimage attacks. A birthday attack exploits the probability of two different inputs sharing a hash value, relying on the notion that the likelihood of collisions increases rapidly with the number of unique inputs examined.
In contrast, a second preimage attack occurs when an adversary, given a specific input and its corresponding hash, seeks another input that produces an identical hash output. Both forms of attack exploit vulnerabilities in hash functions, leading to significant repercussions for systems that rely on their integrity.
Consequences of Hash Collisions
The ramifications of hash collisions are profound, especially in digital security. In the context of digital signatures, a successful collision attack could enable malicious actors to forge signatures, effectively impersonating legitimate entities. This undermines trust in systems that rely on cryptographic assurances, thereby exposing sensitive information and assets to exploitations.
Moreover, the integrity of data generated through hash functions may be compromised, leading organizations to make erroneous decisions based on tampered data. The implications stretch beyond mere data corruption; they extend to legal, financial, and reputational consequences, demonstrating the critical importance of employing robust hashing algorithms that resist collisions.
Real-World Examples of Hash Collisions
Historical incidents provide tangible illustrations of the perils posed by hash collisions. One of the most notorious instances involved MD5 and SHA-1, both of which have been rendered obsolete in high-security contexts due to their vulnerabilities. Notably, in 2004, researchers demonstrated a practical collision for MD5, rendering it unsuitable for cryptographic applications. Similarly, a significant milestone in 2017 saw Google’s researchers successfully exploit a collision in SHA-1, further underscoring the urgency for transitioning to more secure alternatives.
Such revelations prompted a paradigm shift in cryptographic practices, compelling the cryptography community to advocate for the adoption of stronger hash functions, such as SHA-256 or the SHA-3 family. These newer algorithms are designed with advanced techniques to mitigate the risks associated with collisions, enhancing overall security.
Preventative Measures Against Hash Collisions
To fortify systems against the threat of hash collisions, a multi-faceted approach is paramount. Firstly, adopting modern hash functions characterized by superior collision resistance is essential. Instead of relying on deprecated algorithms like MD5 or SHA-1, organizations should embrace algorithms rooted in contemporary cryptographic advancements, such as SHA-256.
Additionally, implementing salting techniques—where unique random values are added to inputs before hashing—can significantly bolster security. This practice complicates the prospect of successful collision attacks, fortifying data integrity. Regular updates and audits of cryptographic practices further serve to ensure that existing systems remain resilient against evolving threats.
Furthermore, adopting best practices for cryptography and investing in continuous education for stakeholders involved in data protection enhances an organization’s preparedness against potential vulnerabilities. By fostering a culture of awareness and vigilance, the risks associated with hash collisions can be significantly mitigated.
Conclusion
In conclusion, the phenomenon of hash collisions poses substantial challenges within the realm of data security. While the mathematical inevitability of collisions cannot be eliminated, the strategies to avert and mitigate their impacts are robustly available. By recognizing the complexities and risks associated with hash collisions, organizations can better safeguard their digital assets and maintain trust in an increasingly interconnected landscape.







Leave a Comment