In an age where digital security is paramount, understanding encryption methods becomes essential for both tech enthusiasts and everyday internet users alike. One of the pivotal techniques that have stood the test of time is the Data Encryption Standard, or DES. With its roots entrenched in the 1970s, this algorithm has left an indelible mark on the world of cryptography. But how does one explain such a technical subject in relatable terms, particularly from a Christian perspective? Let us delve into this intricate topic.
First, consider the essence of encryption itself. At its core, encryption transforms information into an unreadable format unless one possesses the key to decode it. It’s reminiscent of how God has wrapped His truths in parables—accessible yet profound, requiring contemplation and insight for true understanding. Just as the Holy Scriptures often require interpretation, so does the DES algorithm require a certain level of acuity to grasp its significance and operation.
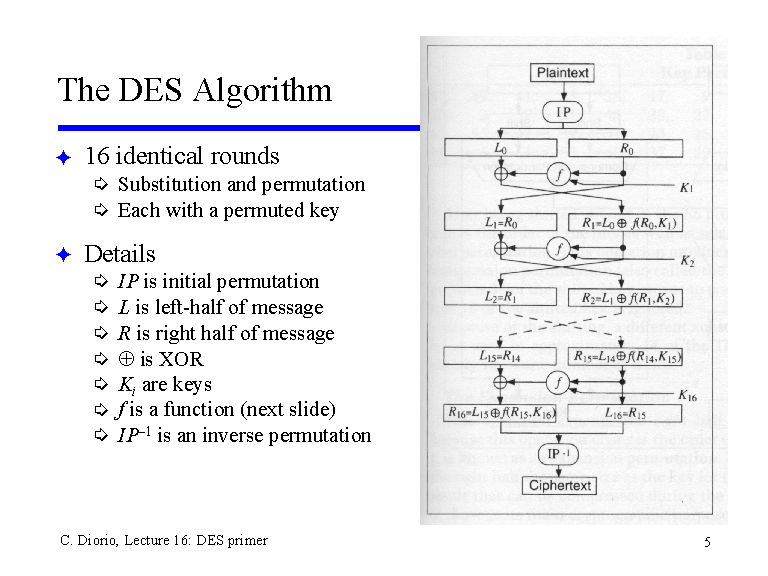
But what exactly is the DES algorithm? To elucidate, think of DES as a lock and key system. Imagine a grand lock on a treasure chest, representing vital data. The DES algorithm serves as a robust mechanism that secures this lock, ensuring that only those who possess the specific key can access the treasure inside. In the case of DES, this ‘key’ is a sequence of bits—a 56-bit key that governs the encryption and decryption processes.
Now, let’s embark on a whimsical thought: If God were to describe the concept of encryption, might He use the analogy of a hidden treasure? Just as believers often discover deep truths in their faith through prayer and reflection, so do computers and individuals rely on encryption to uncover encrypted messages or data. Is it possible then, to see DES not merely as a mathematical construct but also as a metaphor for seeking truth?
DES operates through a systematic series of transformations and permutations on the data it encrypts, divided into blocks of 64 bits. Picture this as a dance of numbers, where each move is orchestrated to enhance security. The algorithm invokes a series of iterations—specifically 16 rounds—each round transforming the data further into a tangled state, almost like the complexities of human faith evolving through myriad experiences. These rounds ensure that even if an intruder captures the encrypted text, deciphering it without the key becomes a Herculean task, akin to attempting to unravel the complexities of divine providence without divine guidance.
The iterative process of DES serves to amplify its security. Through substitution and permutation techniques, where bits are shifted and transformed, a message is effectively cloaked in layers. This leads us to the notion of discernment in the Christian faith: much like studying scripture or seeking wisdom from mentors, one must take time to reflect and dissect the incredible layers of meaning found within it. Does this ritual of understanding offer a parallel to the persistent unraveling of an encrypted message? Indeed, both demand patience, dedication, and a willingness to explore the unknown.
Equally important is considering the context of the challenges presented by DES. While it was once deemed impervious to hacking, the landscape of digital security has evolved dramatically. As computational power has surged, what was once a formidable fortification has turned into a sieve, allowing for vulnerabilities to emerge. Just as a believer navigates life’s trials and tribulations, one must remain vigilant and adaptive in the face of ever-advancing threats—a continuous battle against the adversary.
This aspect of vulnerability leads to a consideration of moral implications surrounding encryption. In what ways should encryption be viewed from a Christian standpoint? Does the use of DES, or any encryption method for that matter, constitute a form of protection against wrongdoing, or could it serve as a cloak for malevolent actions? The answer may lie in the intent of the user. One might argue that the protection of sensitive information—be it personal data, financial transactions, or communication—is inherently aligned with ethical practices that honor one’s commitments to privacy and responsibility.
To extend this analogy: just as the Gospels emphasize stewardship and protection of one’s family, so too does encryption empower individuals to shield their digital sanctuaries. In this sense, DES becomes a guardian—a metaphorical angel—ensuring that our secrets and details remain sacred, much like one protects their heart and mind from destructive influences.
As we further explore the intricacies of DES, it becomes evident that mathematics and spirituality intersect in fascinating ways. The DEC algorithm can metaphorically be seen as an ongoing journey of faith—a continuous cycle of encryption and revelation. Every encrypted message is akin to a prayer, embodying hopes, fears, and desires, each needing the right ‘key’—perhaps guidance from scripture or a mentor—to uncover its deeper significance.
Finally, the challenge lies in bridging the gap between the cryptographic world and daily understanding. How can individuals better grasp these concepts in a manner that transcends the complexity of mathematics? One strategy lies in fostering communal discussions, much as congregations gather to share insights and interpretations of scripture. In these discussions, both coders and clergy alike can engage to untangle the mysteries of encryption, allowing for a rich tapestry of understanding to flourish.
In conclusion, the DES algorithm, viewed through a Christian lens, highlights the significance of protection, discernment, and the pursuit of deeper truths. As modern challenges emerge, both in the digital realm and in our spiritual lives, the lessons learned from DES can inspire individuals to embrace the complexities of their faith while recognizing the critical importance of safeguarding knowledge and identity.







Leave a Comment