Encryption has undergone a prodigious transformation throughout history, evolving from simple mechanical devices to sophisticated quantum systems. This article delineates the remarkable progression of encryption technologies and techniques, illustrating their significance in safeguarding information within a multifarious digital landscape.
The Birth of Cipher Wheels
The journey of encryption began in antiquity, with the inception of rudimentary ciphers. Cipher wheels, as rudimentary as they were ingenious, were among the early tools employed by diplomats and military strategists. These mechanical devices featured rotating discs with letters printed on them, enabling users to encode and decode messages by aligning the discs in specific configurations. Such simple devices allowed for the creation of substitution ciphers, where each letter in plaintext was replaced by another letter. Although they offered a basic level of security, their vulnerability lay in the predictable patterns of letter frequency, which could be exploited by astute cryptanalysts.
The Renaissance of Classical Encryption
As civilization advanced, so too did the complexity of encryption methods. The Renaissance period saw the introduction of the Vigenère cipher, a significant advancement in cryptography. Unlike its predecessors, the Vigenère cipher employed a keyword to alter the encryption method, thus enhancing security. This polyalphabetic cipher proved to be a formidable challenge for cryptanalysts, as it obscured the frequency of letters significantly better than simple substitution methods. However, its eventual deciphering in the 19th century by Charles Babbage exposed the limitations of classical encryption methods.
The Age of Mechanical and Electromechanical Devices
The 20th century heralded a new era of encryption, characterized by the development of mechanical and electromechanical devices. The Enigma machine, utilized by the Germans during World War II, epitomized this innovation. This complex system of rotors and wiring allowed for an astounding number of possible key combinations, making the decryption process tremendously laborious. Nonetheless, the efforts of cryptanalysts, including Alan Turing and his colleagues at Bletchley Park, ultimately cracked Enigma’s code, showcasing the ongoing arms race between encryption and decryption technologies.
Mathematics and the Rise of Modern Cryptography
The latter half of the 20th century witnessed a seismic shift in encryption with the advent of modern cryptographic techniques grounded in mathematical principles. The Data Encryption Standard (DES), introduced in the 1970s, utilized a complex algorithm based on permutations and substitutions. DES marked the beginning of symmetric key cryptography, where both the sender and receiver employed the same key for encryption and decryption. While DES provided a substantial level of security, the exponential growth in computational power rendered it vulnerable to brute-force attacks as the 1990s approached.
Asymmetric Cryptography: A Paradigm Shift
In response to the burgeoning threats posed to symmetric encryption, researchers devised asymmetric cryptography in the late 20th century. Pioneered by figures such as Whitfield Diffie and Martin Hellman, this revolutionary approach relied on the use of public and private key pairs. The RSA algorithm, developed by Rivest, Shamir, and Adleman, became the standard bearer for public-key cryptography. In this framework, the public key serves for encryption, while a distinct private key decrypts the information, thereby enhancing security by eliminating the need to share sensitive keys over insecure channels.
The Emergence of Hash Functions
Alongside advancements in encryption methods, hash functions emerged as another key facet of modern cryptography. Functions like SHA-256 (Secure Hash Algorithm) transformed the ability to ensure data integrity and authenticity. Unlike encryption, hash functions generate a fixed-length string of characters from input data, rendering the original data irretrievable. These functions play a critical role in digital signatures and certificates, ensuring that information remains uncompromised in transit.
The Digital Age and Symmetric Key Advancements
As the internet proliferated, the necessity for robust encryption became paramount. The Advanced Encryption Standard (AES), established in the early 2000s, addressed the security shortcomings of DES. AES employs block ciphers to encrypt data in fixed-size blocks, providing enhanced security against ever-evolving threats. With various key lengths—128, 192, and 256 bits—AES offers users a flexible approach to securing sensitive information.
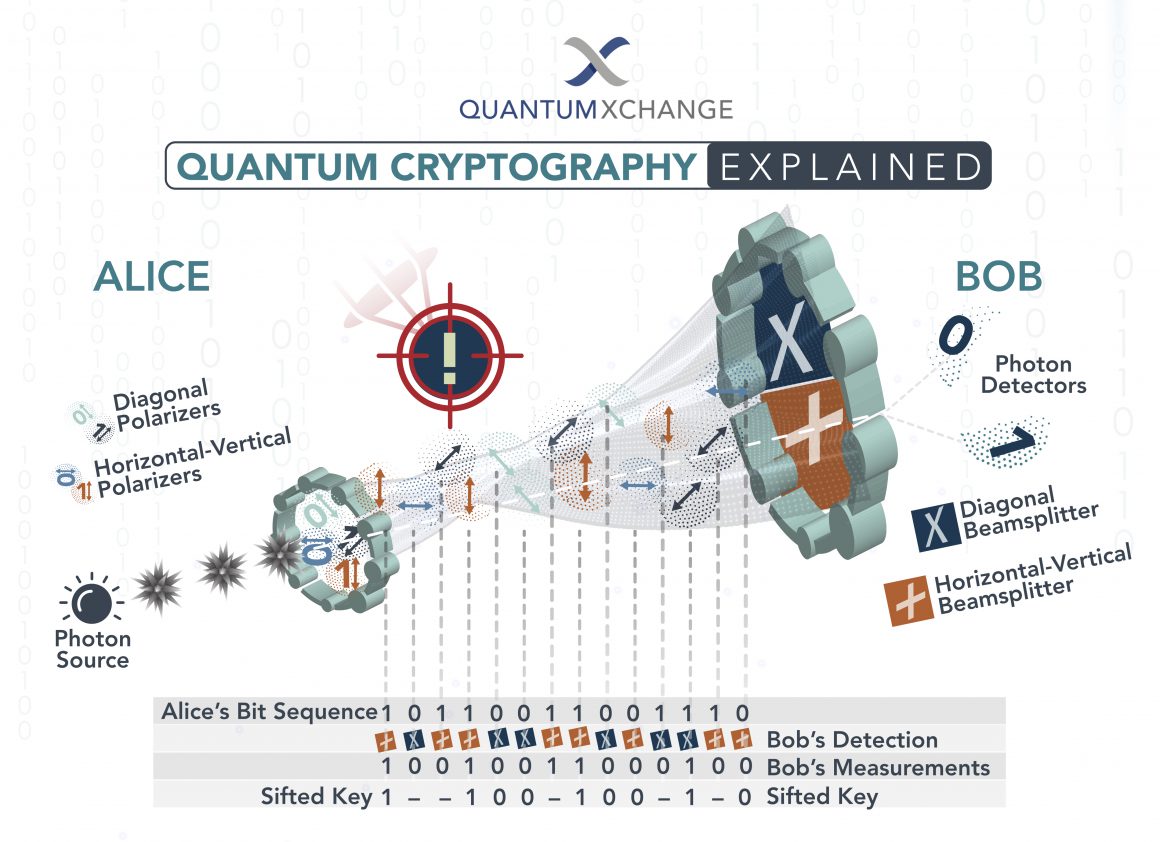
The Quantum Leap: Quantum Cryptography and Key Distribution
As we approach the contemporary era, the advent of quantum computing introduces both unprecedented capabilities and formidable challenges for encryption methods. Quantum cryptography, notably the groundbreaking Quantum Key Distribution (QKD), leverages the principles of quantum mechanics to create secure communication channels. Unlike traditional methods susceptible to interception, QKD employs the behavior of subatomic particles to detect eavesdroppers covertly. This innovative approach promises to lay the foundations of virtually unbreakable encryption, heralding a new epoch in the battle for data security.
Conclusion
The evolution of encryption reflects humanity’s enduring quest for privacy and security in communication. From the simplicity of cipher wheels to the complexities of quantum key distribution, each milestone in this chronological saga underscores how the interplay of advancing technology and intellectual ingenuity continues to shape the encryption landscape. The future promises even more innovations as cryptographers and technologists strive to stay ahead of emerging threats, ensuring that the sanctity of information remains intact in an increasingly interconnected world.







Leave a Comment