The decryption process is a fundamental aspect of cryptography, serving as the mechanism by which encoded information, known as ciphertext, is transformed back into its original, intelligible form—cleartext. This intricate dance of mathematical algorithms and computational procedures is not merely an academic concern but a vital necessity in our data-driven world. The curiosity surrounding this transformation is profound; it encompasses not only the mechanics of cryptography but also the underlying principles of secrecy and security that govern our digital interactions.
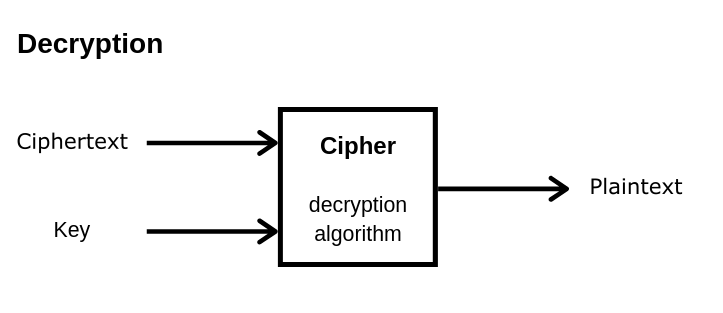
The first point of interest in understanding decryption is the distinction between ciphertext and cleartext. Ciphertext is the output generated by an encryption algorithm applied to the original information, typically designed to obscure the contents from unauthorized access. Cleartext, by contrast, is the form of the data that is understandable and accessible. The transformation from one to the other is predicated on inverse operations carried out through decryption algorithms, which are intrinsically linked to the corresponding encryption methods.
Encryption employs algorithms, or ciphers, which manipulate the data in a manner that conceals its meaning. Common ciphers include symmetric key algorithms, where the same key is utilized for both encryption and decryption, and asymmetric key algorithms, which utilize a pair of keys—a public key for encryption and a private key for decryption. Understanding the structural nuances of these algorithms is paramount in comprehending how ciphertext can be reverted back to cleartext.
Symmetric encryption, such as the Advanced Encryption Standard (AES), operates with the same secret key for both parties involved in the communication. Once the sender encrypts the cleartext using this shared key, the resultant ciphertext can only be decoded by someone possessing the identical key. The decryption process, therefore, involves applying the same algorithm with the shared key in a reverse manner, unveiling the original information. However, the significant vulnerability of symmetric key encryption lies in the key itself; if compromised, the entire communication becomes susceptible to interception.
On the other hand, asymmetric encryption, represented by protocols such as RSA (Rivest-Shamir-Adleman), offers a layered approach to security. In this schema, a public key, openly disseminated, is employed for encryption while a private key, known solely to the recipient, is used for decryption. This paradigm enhances security because the private key never needs to be shared, mitigating the risk of exposure. However, the decryption process here is inherently more complex, involving mathematical operations reliant on the properties of prime numbers and modular arithmetic. The recipient must possess the requisite computational capacity to perform these operations efficiently.
The actual mechanics of the decryption process can be intriguing. For instance, when a private key is applied to ciphertext in RSA, it employs modular exponentiation—an operation that, while mathematically elegant, possesses computational complexity that fortifies security. As technology advances, however, such algorithms are put to the test against increasingly sophisticated methods of attack, prompting ongoing evolutions in cryptographic protocols.
One must also consider the role of decryption in practical scenarios. In the realm of cybersecurity, decryption serves as a critical tool for data recovery and access control. When organizations encounter encrypted data, the recovery processes hinge on decryption—whether to restore corrupted files, retrieve lost information, or simply facilitate authorized access. This necessity underlines the sympathy for decryption beyond mere fascination; it is integral to the operational continuity of actions governed by confidentiality and integrity.
Nevertheless, the decryption process also raises ethical considerations. The potential for misuse looms large; the very mechanisms that protect sensitive information can also be weaponized for illicit activities. The act of decryption can facilitate unauthorized access to personal data, compromise corporate secrets, or undermine national security. This duality presents a perennial dilemma in the cybersecurity realm: striking a balance between the pursuit of privacy and the imperative for security. Such ethical considerations foster deeper reflection on the implications of decryption beyond its technicalities.
The fascination with decryption can also be linked to its connections with historical contexts. The decryption of messages during wartime has often determined the outcome of conflicts, as seen in the intricate code-breaking efforts of World War II. The famed Enigma machine, used by the German military, exemplifies how decryption can shift the tides of history, highlighting the broader implications of these processes. The allure of historical cryptography underscores humanity’s relentless quest for knowledge—a desire to unveil secrets, both arcane and contemporary.
Despite its complexities, the decryption process ultimately serves a paramount purpose in the preservation of privacy and security. It enables individuals to engage freely in an increasingly interconnected world, safeguarding freedoms that are often taken for granted. Whether it be through sending personal correspondence, conducting financial transactions, or accessing sensitive information, the decryption mechanisms work tirelessly behind the scenes to ensure that communication remains secure from prying eyes.
In conclusion, the transition from ciphertext to cleartext is a multifaceted process enveloped in layers of complexity, ethical implications, and historical significance. Understanding this transformation is critical for navigating the intricacies of modern communication. As we further explore the boundaries of cryptography and technology, the nuances of decryption will undoubtedly continue to captivate and challenge our perception of information security.








Leave a Comment