Encryption in Transport Layer Security (TLS) serves a pivotal role in ensuring the integrity and confidentiality of data transmitted over the internet. But, what exactly is happening behind the scenes of this sophisticated system? Is encryption merely a barrier against eavesdroppers, or does it incorporate more complex mechanisms that actively combat a myriad of cyber threats? This inquiry not only explores the operational framework of TLS but also highlights its importance in contemporary digital communications.
At its core, TLS is a cryptographic protocol designed to provide secure communication over a computer network. It is widely implemented across various platforms, from securing web browsers to safeguarding emails and instant messaging. To truly comprehend TLS, one must delve deep into the underpinnings of its architecture. So, what constitutes the skeletal framework of TLS?
To begin with, TLS operates by utilizing a combination of symmetric and asymmetric encryption methods. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption leverages a pair of keys—a public key and a private key. This duality sets the stage for a secure connection initiated through a process known as the handshake.
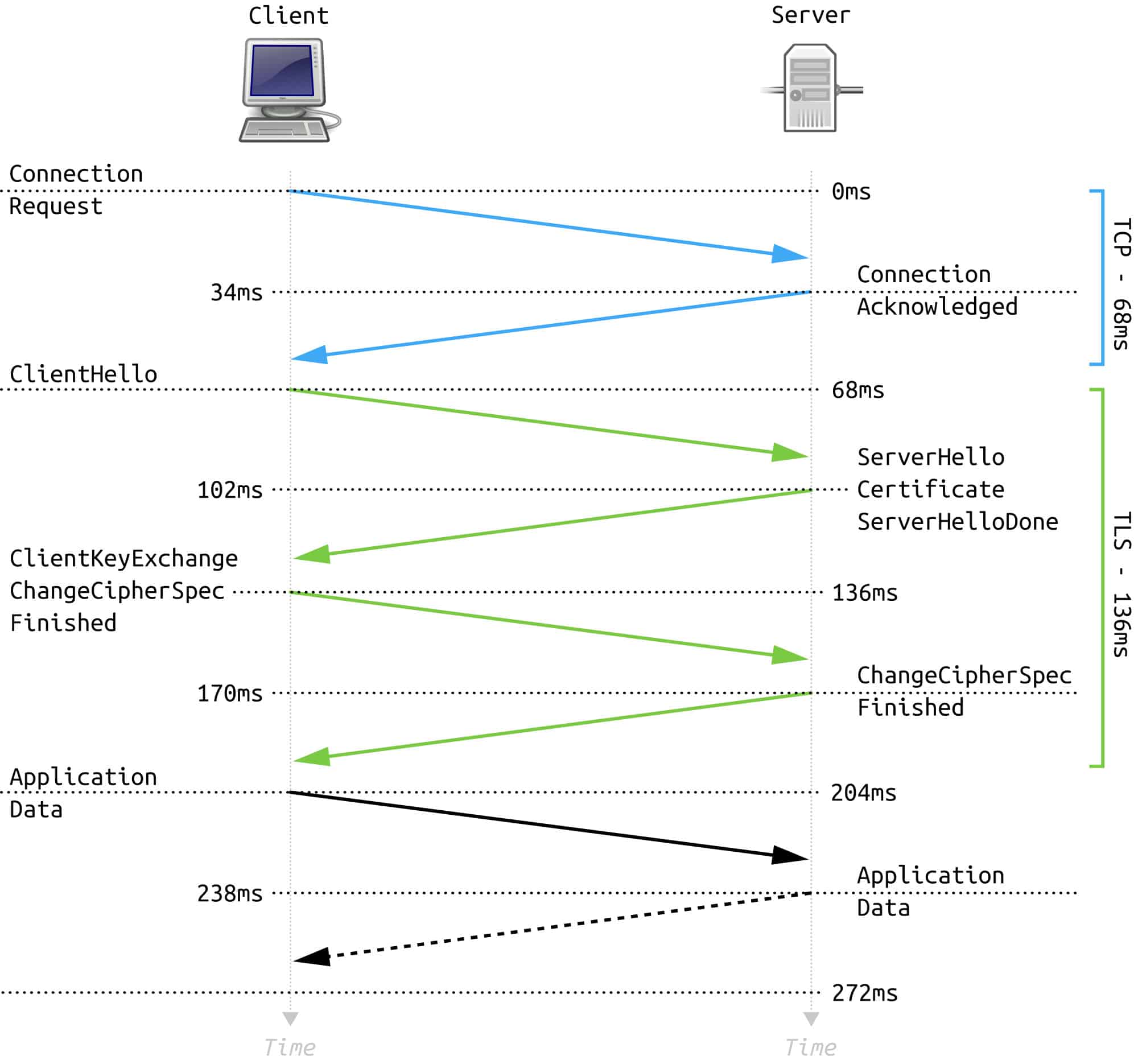
During the TLS handshake, the client and server engage in a sequence of communications to establish a secure connection. The process begins with the client sending a “ClientHello” message, which includes the TLS version supported, cipher suites, and a randomly generated number. In response, the server sends a “ServerHello,” echoing the chosen TLS version and cipher suite, and includes its own random number. This seemingly simple exchange carries substantial weight, as it establishes the foundational parameters for the subsequent encryption process.
The heart of encryption arises during the key exchange phase of the handshake. Here, asymmetric encryption shines. The server transmits its public key to the client, which is then utilized to encrypt a newly generated symmetric key—in essence, the session key. By using the server’s public key for encryption, only the server, with its corresponding private key, can decrypt this information. This mechanism illustrates how TLS envelops data in layers of security, preventing unauthorized access even if a nefarious actor intercepts the transmission.
Once the session key is successfully exchanged, TLS transitions to symmetric encryption. Why, you might ask, does TLS employ both methods? The answer lies in efficiency. Symmetric encryption is significantly faster than its asymmetric counterpart, making it ideal for encrypting the bulk of the data once a secure channel has been established.
Let’s explore the cipher suites that TLS utilizes during encryption. A cipher suite is a combination of algorithms that dictate how key exchange, encryption, message authentication, and hashing are conducted. The selection of a cipher suite can deeply affect the strength of the encryption. It is critical to choose reliable algorithms; weaker ones could render the encryption futile, raising a potential challenge for implementers in selecting appropriate suites that balance performance and security.
The negotiation of the cipher suite during the handshake is determined by both the client and server. They mutually agree on the strongest suite that they both support, which introduces the notion of vulnerability: clients might connect to servers with subpar configurations, leading to potential compromises in security. This scenario poses a risk—how many users are aware of the foundational elements securing their communications?
Moreover, the authenticity of the certificates involved cannot be overlooked. Digital certificates, which validate the ownership of public keys, play a crucial role in establishing trust within TLS. These certificates are generally issued by trusted Certificate Authorities (CAs), which serve as mediators in reinforcing the legitimacy of the server’s identity. However, if a CA’s infrastructure is compromised, the entire ecosystem faces dire consequences—what safeguards do we have in place to protect against such breaches?
The aspect of message integrity is equally important in the landscape of TLS. It is enforced through Message Authentication Codes (MACs) that ensure data integrity during transmission. Each message sent over a TLS connection includes a MAC, which is computed using the session key. By verifying the MAC upon receipt, a recipient can confirm that the message has not been altered in transit. Nonetheless, this introduces a paradox: while MACs provide assurance of integrity, they also add complexity, positioning TLS as a jurisdiction where errors in implementation can yield vulnerabilities.
In addition to the necessity for robust algorithms and proper certificate management, the TLS protocol is also subject to continuous evaluation and enhancement. As vulnerabilities are discovered—such as the infamous POODLE and Heartbleed attacks—the cryptographic community diligently revises standards and encourages timely upgrades. The question then remains: is the industry moving swiftly enough to mitigate the threats as they arise?
In conclusion, while TLS may appear as an opaque fortress against cyber threats, the frameworks behind it reveal a bewildering complexity filled with interdependencies and vulnerabilities. The interplay of symmetric and asymmetric encryption, the negotiation of cipher suites, and the validation of digital certificates collectively establish the foundation of trust upon which users rely for secure communications. As we embrace the digital age, the challenge of safeguarding data through encryption must remain a focal point, demanding vigilance, knowledge, and proactive measures. The next time you connect to a secure website, take a moment to ponder the intricate ballet of encryption that unfolds behind the scenes—how secure is your digital footprint, really?








Leave a Comment