As we delve into the landscape of cybersecurity in 2025, one cannot help but closely scrutinize the relevance of encryption standards that have served as cornerstones of digital security. Among these, RSA (Rivest-Shamir-Adleman) algorithms have held sway since their inception in the late 1970s. However, recent discussions suggest that RSA-based systems may be approaching obsolescence. Are we witnessing the twilight of this venerable cryptographic standard, or is its ongoing evolution sufficient to meet emerging security challenges?
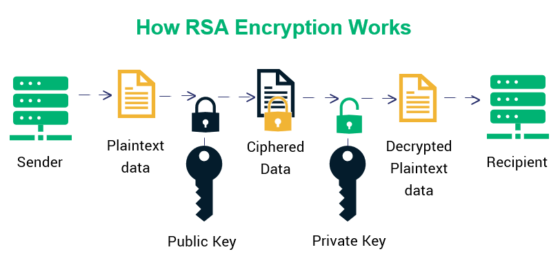
The backbone of RSA encryption lies in its asymmetric nature. This mechanism involves a pair of keys: a public key used for encryption and a private key used for decryption. This paradigm allows for secure communication over insecure channels, a necessity in our increasingly interconnected world. However, despite its foundational role, the cryptographic community has noted potential vulnerabilities lurking within RSA’s architecture. The advent of quantum computing looms ominously on the horizon, threatening to dismantle the very principles upon which RSA is constructed.
Experts anticipate that by the mid-2020s, quantum computers could achieve capacity levels allowing them to execute Shor’s algorithm efficiently. This algorithm dramatically reduces the time required to factor large integers, which is the linchpin of RSA’s security. If such machines become a reality, the core assumptions of RSA encryption could be compromised, rendering it susceptible to breaches and manipulation. The urgency of this dilemma has prompted an increasing number of organizations to explore post-quantum cryptography as a contingency.
Moreover, the emergence of alternative encryption methodologies has magnified discussions surrounding RSA’s future viability. For example, Elliptic Curve Cryptography (ECC) presents itself as a formidable contender. With substantially shorter key lengths than RSA while delivering equivalent security levels, ECC offers efficiency advantages that cannot be overlooked, especially for mobile devices and constrained environments. In parallel, lattice-based and multivariate cryptography solutions are garnering attention for their potential in resisting the cryptographic perils associated with quantum computing.
Despite the rising tide of alternatives, the ingrained legacy of RSA serves as a double-edged sword. Its wide-reaching adoption has created a vast ecosystem of applications, protocols, and infrastructures built around its principles. Transitioning to new encryption standards involves significant operational and logistical considerations, presenting formidable challenges to organizations that must grapple with compatibility issues and potential disruptions in service. Certainty is elusive in a landscape shaped by rapid technological advancements and escalating cyber threats, necessitating a careful analysis of risk versus reward.
Nevertheless, a seemingly paradoxical question arises: Can RSA maintain its relevance in the interim? Optimists within the cryptographic community advocate for hybrid models that combine RSA with emerging algorithms to bolster defenses against both classical and quantum threats. The logical synthesis of these technologies may provide an elegant solution that preserves existing RSA infrastructure while gradually phasing in quantum-resilient practices.
Moreover, regulatory implications further complicate the landscape. Governments across the globe are contemplating stricter compliance requirements and enhanced cybersecurity frameworks to safeguard national digital infrastructures. These efforts could inadvertently energize the market for RSA by mandating its continued use in specific contexts, thereby prolonging its lifespan while creating a more dynamic interplay between legacy systems and emergent technologies.
However, this prolongation might be akin to a band-aid solution, obscuring the inevitable transition to next-generation encryption mechanisms. Security professionals must engage in proactive dialogues about the long-term implications of sustained reliance on RSA. Fostering a culture of adaptability within organizations is vital. Embracing a forward-thinking ethos could empower them to preemptively pivot to more secure alternatives before any significant quantum advancement occurs.
Moreover, as educational institutions and private sector players pour resources into advancing cryptographic research, stakeholders should remain cognizant of the potential hurdles associated with such transitions. Cryptography is not merely a function of mathematics; it is a complex amalgamation of human behavior, policy, and economics. Fear of change, financial barriers, and the inertia of existing systems can stymie even the most well-intentioned efforts toward modernization.
In conclusion, the question of whether RSA-based systems are outdated by 2025 is as nuanced as the very algorithms that define them. While these systems are facing significant challenges—ranging from quantum threats to the rise of alternative encryption techniques—one must recognize the intricate web of operational realities that govern the adoption of new technologies in the digital realm. Although RSA may very well be on the brink of obsolescence, its legacy continues to inform the ongoing evolution of cybersecurity practices. The path ahead is one that requires both vigilance and adaptability, as the world hurtles into an era defined by unprecedented technological change.







Leave a Comment