In the realm of modern cryptography, the Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) key exchange protocol, particularly in conjunction with RSA (Rivest-Shamir-Adleman) digital signatures, presents a sophisticated framework for secure communication. This process commences with the establishment of a shared secret between two parties, utilizing the mathematical properties of elliptic curves. However, when we delve into the intricacies of ECDHE_RSA, it becomes evident that the collision of curves and keys introduces several nuanced challenges and opportunities that are pivotal to understanding contemporary cybersecurity architecture.
To adequately comprehend ECDHE_RSA, one must first dissect its two primary components. ECDHE leverages the advantages of elliptic curve cryptography (ECC), which provides high levels of security with relatively small key sizes, thereby optimizing performance. Comparatively, RSA relies on the computational complexity of factoring large integers, necessitating significantly larger keys to maintain security. The merger of these methodologies appears seamless initially, yet the interaction of their underlying mathematical principles reveals potential friction points.
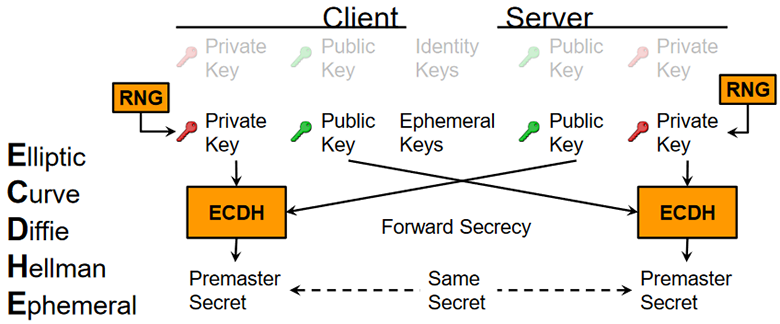
The ephemeral nature of ECDHE is a critical attribute. Each session generates a novel ephemeral key, which drastically reduces the risk of long-term key compromise should a single session’s key be exposed. This transient key fortifies security since it minimizes the impact of potential attacks targeting any given transaction. However, the RSA signature component, often utilized for authentication, introduces a static key paradigm that does not share the same transient characteristics as ECDHE. The juxtaposition of ephemeral keys with static RSA keys necessitates a rigorous discussion about the implications for key management and long-term security.
As one explores the operational mechanisms between ECDHE and RSA, it is worthwhile to examine the birth of the ECDHE_RSA handshake. It commences with one party generating an ephemeral public/private key pair from their chosen elliptic curve. The ephemeral public key is transmitted to the other party, along with a digitally signed message using the RSA key. The receiving party, in turn, verifies the signature, ensuring the integrity and authenticity of the exchanged data before proceeding to compute the shared secret using the ephemeral key.
However, the collision of these cryptographic paradigms is not without its pitfalls. One significant concern arises from the choice of elliptic curve used during the key exchange process. Different curves possess unique properties regarding their security levels and performance metrics. For instance, the adoption of a weak or poorly defined curve can expose the communication to vulnerabilities such as the “invalid curve attack,” wherein adversaries exploit the choice of curve to facilitate the extraction of private keys or unscramble encrypted data.
Moreover, the stability and maturity of the cryptographic libraries that implement ECDHE_RSA cannot be understated. Flawed implementations or outdated libraries can create critical vulnerabilities in the security framework. Hence, developers must prioritize regular updates and adhere to best practices when integrating these cryptographic protocols into applications. Security is ultimately a chain, and each link must be robust to withstand contemporary threats.
In addition to these vulnerabilities, the performance trade-offs associated with the integration of ECDHE and RSA merit scrutiny. While ECDHE offers efficient key exchange mechanisms, the reliance on RSA signatures can hinder the overall speed of the handshake process. This phenomenon is particularly evident in environments with limited processing capabilities or bandwidth, where the overhead introduced by RSA can become a bottleneck. As such, practitioners ought to consider alternative approaches, such as the use of ECDSA (Elliptic Curve Digital Signature Algorithm), which aligns more closely with the ephemeral characteristics of ECDHE.
The resilience of ECDHE_RSA to various cryptographic attacks further compounds the complexity of its deployment. While the ephemeral key aspect significantly fortifies against eavesdropping and replay attacks, it does not render the protocol invulnerable to more sophisticated threats, such as man-in-the-middle attacks. These attacks can exploit weaknesses in the authentication process, especially if the integrity of the RSA signature is compromised. Therefore, ensuring that the authenticity of the public keys and the integrity of the signature must remain paramount, necessitating a robust public key infrastructure (PKI) to facilitate secure exchanges.
In examining the future of ECDHE_RSA, advancements in quantum computing loom as a potential upheaval to the current security models. Quantum algorithms, particularly Shor’s algorithm, have the potential to dismantle the foundational security of RSA, thereby necessitating a reevaluation of key exchange protocols reliant on RSA signatures. In light of these impending developments, the integration of quantum-resistant algorithms may soon become indispensable, prompting a shift towards hybrid models that combine classical algorithms with post-quantum alternatives.
In conclusion, ECDHE_RSA exemplifies the intricate interplay between advanced cryptographic methodologies in contemporary communication security. The synthesis of ephemeral key exchanges and long-term RSA signatures provides heightened security, but not without introducing unique challenges. Developers and cybersecurity professionals must be keenly aware of the structural intricacies and ongoing developments in the field. As threats evolve and technology advances, a proactive approach to cryptography will remain essential for safeguarding sensitive data against a myriad of potential vulnerabilities.








Leave a Comment