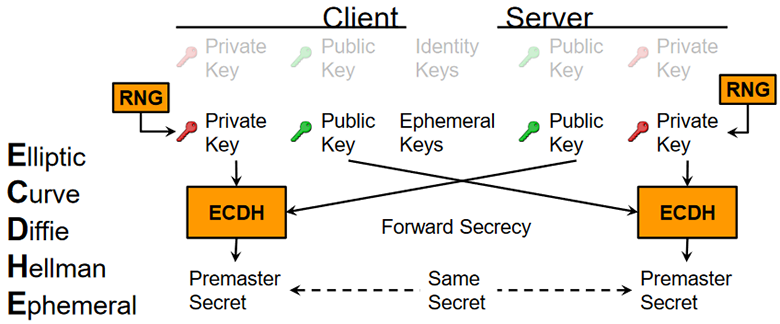
The realm of cryptography is a robust field, marrying complex mathematical concepts with the practical necessities of securing digital communications. Within this domain, the Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) cipher emerges as a particularly sophisticated player. This protocol engenders secure key exchanges by employing the principles of ephemeral keys, leveraging elliptic curve cryptography to ensure not just speed but also a crucial property known as forward secrecy.
To navigate through the intricacies of ECDHE, it is useful to unpack its multifaceted components, beginning with the foundational principles of key exchange mechanisms. Key exchange protocols allow two parties to establish a shared secret over an insecure channel. Traditional methods, such as the Diffie-Hellman key exchange, laid the groundwork, but they were often vulnerable to various cyber threats, particularly through the capture of the symmetric keys themselves over time.
Enter ECDHE, which enhances the Diffie-Hellman model by employing elliptic curve mathematics. This substitution significantly reduces the key size required to achieve comparable levels of security when juxtaposed with non-elliptic curve algorithms. For instance, while a 2048-bit RSA key may provide substantial security, an ECDHE key of only 256 bits can offer equivalent protection. This efficacy stems from the inherent properties of elliptic curves that make certain difficult mathematical problems, such as the discrete logarithm problem, exponentially more challenging to solve, thus fortifying the cryptographic framework.
At the core of ECDHE is the concept of ephemeral keys. Unlike static keys that might be used indefinitely, ephemeral keys are generated anew for each session. This attribute guarantees that even if a key were to be compromised, it would only endanger that singular session’s communications rather than all past or future exchanges. This enhances security, particularly in an age relentlessly defined by data breaches and cyber espionage.
Forward secrecy is a distinguishing feature of ECDHE, providing an essential safeguard for user privacy and data confidentiality. With traditional key exchanges, if a static key is compromised, every communication encrypted with it could potentially be exposed. In contrast, ECDHE ensures that session keys are ephemeral and thus not translatable back to any long-term keys. Therefore, even in the unfortunate event of a future key compromise, past communications remain protected, an invaluable reassurance in today’s digital environment.
When deploying ECDHE, one might encounter various implementations and configurations. Typically, the cipher suite in use will designate the key exchange method. Often, ECDHE is paired with symmetric ciphers for the actual data encryption, such as AES (Advanced Encryption Standard). In a common scenario, a client and server may initiate a secure connection through the Transport Layer Security (TLS) protocol, where both parties agree on using ECDHE for key exchange and AES for the encryption of data—a harmonious combination that imbues the communication channel with both agility and fortitude.
Additionally, the intricacies of elliptic curve operations can lead to some implementation challenges. Developers must ensure that the curves used are appropriately chosen to resist known vulnerabilities. The National Institute of Standards and Technology (NIST) recommends certain curves, including the NIST P-256 curve, to guarantee optimal security and performance. It is not only crucial to select robust curves, but also to remain vigilant about potential side-channel attacks that aim to exploit timing or power consumption variations during cryptographic operations.
The deployment of ECDHE is not without its advantages and drawbacks. A primary advantage lies in its efficiency. Given the smaller key sizes required, resource-constrained devices benefiting from ECDHE can maintain secure communications without incurring excessive overhead. This is particularly pertinent in the Internet of Things (IoT) landscape, where devices often have limited processing capabilities.
However, ECDHE’s reliance on proper implementation raises the stakes. Any lapse in the cryptographic configurations, such as utilizing weak or outdated curves, can lead to vulnerabilities within the security model. Consequently, organizations must invest in rigorous testing and continual updates of their cryptographic libraries to safeguard against emerging threats.
Moreover, regulatory compliance regarding cryptographic protocols is another dimension to consider. As privacy and data protection laws evolve, organizations using ECDHE must remain informed about applicable standards and best practices to comply with governmental regulations, especially in industries like finance or healthcare where the stakes are significantly heightened regarding data security.
In the evolving landscape of cybersecurity, the importance of ECDHE cannot be overstated. Its architecture, which synergizes sophisticated mathematics with practical applications, underscores the direction in which secure communications are heading. ECDHE provides an armor of resilience against a backdrop of ever-increasing threats, encapsulating vital characteristics that support our digital engagements. The interplay of speed, security, and forward secrecy positions ECDHE as an invaluable asset in protecting our sensitive information in an increasingly interconnected world.
Ultimately, as technology advances, keeping abreast of cryptographic developments will prove essential. By understanding the mechanisms and implications of protocols like ECDHE, stakeholders across various sectors can foster more secure communication channels, ensuring that privacy remains paramount in a digitally-driven society.







Leave a Comment