In the realm of modern cryptography, the debate surrounding the security of encryption methods often gravitates toward two prominent players: Elliptic Curve Cryptography (ECC) and Rivest-Shamir-Adleman (RSA). Both of these encryption algorithms have their own respective advantages and drawbacks, sparking a plethora of discussions regarding which method stands as the paragon of security. As we delve into this analytical exploration, one may ponder: Is it really a matter of picking a side, or is there a more nuanced understanding awaiting beneath the surface?
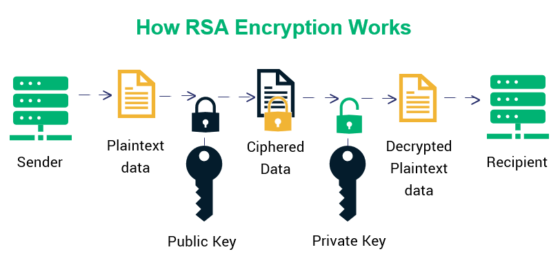
To commence this discourse, it is essential to establish a baseline understanding of both ECC and RSA. RSA, a stalwart in cryptographic protocols since the late 1970s, employs the mathematics of large prime numbers. Through the process of key generation, it creates a pair of keys that are functionally asymmetrical; one key for encryption and the other for decryption. The security of RSA predominantly relies on the computational difficulty of factoring the product of two large prime numbers. This characteristic renders RSA a formidable encryption method, particularly when dealing with extensive datasets.
Conversely, ECC is a more recent innovation within the cryptographic fabric. It utilizes the algebraic structure of elliptic curves over finite fields. The potency of ECC lies in the fact that it can achieve equivalent levels of security with significantly smaller key sizes compared to RSA. For instance, a 256-bit key in ECC is roughly tantamount in security to a 3072-bit key in RSA. This disparity presents compelling economic and efficiency advantages, particularly in environments where processing power and bandwidth are at a premium.
However, functionality encompasses more than mere efficiency. While ECC is predicated on challenging mathematical problems, it is paramount to interrogate whether these problems are sufficiently resilient to emerging computational threats, especially with the looming specter of quantum computing. Quantum machines are anticipated to undermine traditional cryptographic protocols, especially that of RSA, through algorithms such as Shor’s algorithm, which capitalizes on the efficiency of quantum computations to factor large integers far more expeditiously than classical computers.
This raises an intriguing question: Can ECC stand the test of quantum advancements? Currently, ECC relies on the elliptic curve discrete logarithm problem (ECDLP) for its security, a problem that, although not easily solved by classical computers, remains vulnerable to quantum algorithms too. This leads to a potential challenge: the apparent security of ECC could warrant skepticism when pitted against future technological trajectories. In essence, while ECC is lauded for its efficiency and security, both ECC and RSA may need re-evaluation in the impending post-quantum era.
Another vital aspect to consider is implementation. Security, after all, is not merely a matter of theoretical strength; it is profoundly affected by real-world application. RSA’s lengthy keys and established presence result in a wealth of libraries and tools optimized for its use, enhancing its reliability. However, ECC’s subtleties necessitate meticulous implementation, given that any flaw in its application may lead to vulnerabilities. This bifurcation necessitates that cryptographers and security engineers approach each method with discernment, cognizant of the subtleties interlaced within their respective implementations.
Moreover, the environmental context in which these encryption methods are utilized reveals additional complexities. For instance, in constrained environments such as mobile devices or Internet of Things (IoT) applications, the resource-intensive nature of RSA may hinder performance. Herein lies ECC’s advantage: its smaller key sizes provide a compelling solution to performance concerns, thus facilitating faster computations and reduced energy consumption. Such distinctions underscore that the choice of an encryption method is not merely academic; it is fundamentally tied to the specific use case and threat landscape.
Nonetheless, it is judicious to recognize that the debate is not a zero-sum game. Dominating discussions often circle around which method is ‘more secure,’ but this binary framing belies the rich tapestry of considerations influencing encryption choice. Encryption should be perceived as a multi-faceted tool, where the context, threat model, available resources, and long-term vision for security must harmoniously coalesce to inform the best course of action.
Ultimately, ECC and RSA can be viewed as joint protagonists in the narrative of cryptography, each with its unique strengths and weaknesses. As such, engaging with the question of which is “more secure” benefits from a more sophisticated lens — one that considers not only their mathematical underpinnings but also practical implications within diverse environments. As advances in computing technology continue to emerge, revisiting these encryption methods will be paramount in ensuring that they align with the evolving landscape of cybersecurity. While both RSA and ECC offer substantial security guarantees, adaptability, foresight, and an understanding of their respective roles will be the keystones of a resilient cryptographic strategy.







Leave a Comment