In the realm of data security, symmetric encryption stands as a cornerstone technique, widely utilized for safeguarding sensitive information. This method employs a single secret key for both encryption and decryption, presenting a paradox of simplicity and complexity. Does symmetric encryption unequivocally guarantee data integrity? This question permeates discussions among cryptographers, security engineers, and information technologists alike.
Understanding the concept of data integrity is pivotal for grasping the implications of symmetric encryption. Data integrity refers to the maintenance of data accuracy and consistency over its lifecycle. It is a fundamental principle that ensures information remains unaltered during storage, transmission, and retrieval. Failing to uphold data integrity can lead to catastrophic consequences, including unauthorized access, data breaches, and corruption. Given the significance of integrity, symmetric encryption’s role must be scrutinized more closely.
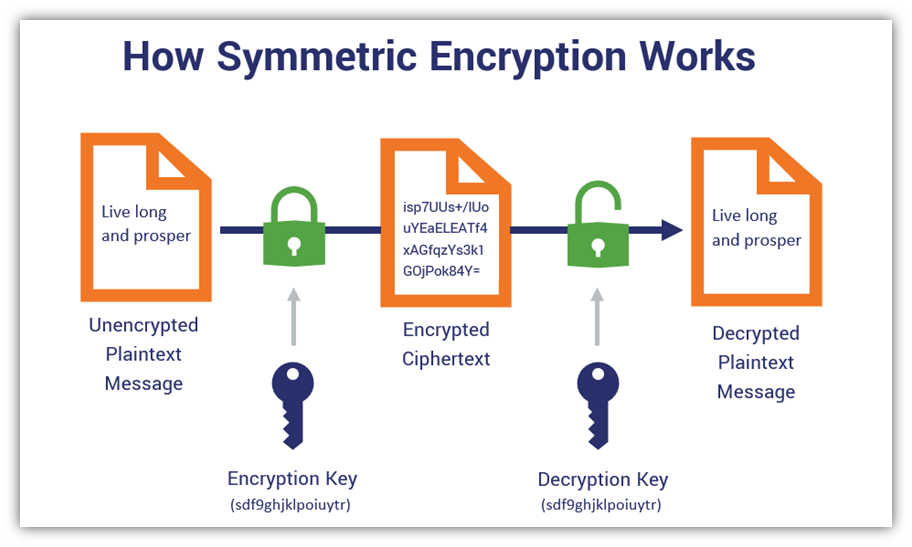
At its core, symmetric encryption accomplishes the task of confidentiality by transforming plaintext into ciphertext, thus obscuring the original data from potential eavesdroppers. While this transformation ensures that only individuals possessing the secret key can decrypt the information, it does not inherently affirm that the data has not been tampered with. The transformative process can encrypt malicious data just as easily as it can secure legitimate data. Thus, while the encrypted message remains confidential, its integrity cannot be guaranteed through encryption alone.
This leads to the paramount concern: the absence of mechanisms to verify that the data received is identical to the data sent. Without additional protocols, users cannot ascertain whether the data has been altered in transit. For example, an attacker could intercept and modify the encrypted data before it reaches the intended recipient, replacing benign ciphertext with a harmful payload. Such scenarios illustrate the limitations inherent in relying solely on symmetric encryption for data integrity.
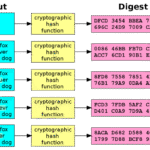
The conundrum invites one to explore the broader cryptographic landscape to fulfill the imperative of integrity. Incorporating cryptographic hash functions is a prevalent approach. A hash function takes an input—a file, message, or data packet—and generates a unique fixed-size string of characters, or hash value, that represents the data. When a sender transmits data, they can also send the corresponding hash value. Upon receipt, the receiver can compute the hash value of the received data and compare it to the transmitted hash. If the two hash values match, integrity is confirmed; if not, the receiver knows the data has been compromised.
Moreover, the significance of using secure hash functions, such as SHA-256, cannot be overstated. Using outdated or vulnerable hashing algorithms could potentially expose data to collision attacks, wherein two different inputs yield the same output hash. It is crucial that hashing mechanisms employed alongside symmetric encryption are robust and resilient against such vulnerabilities.
Ultimately, the integration of hashing into the encryption process illustrates a broader, more holistic approach to securing data. This interplay emphasizes the necessity of dual mechanisms: one for confidentiality and another for integrity. Such practices align with comprehensive security frameworks, which underscore that no single method should be solely relied upon. Instead, a multi-faceted approach amalgamating different cryptographic techniques fortifies the resilience of security measures.
Additionally, digital signatures represent another critical facet of ensuring data integrity. Unlike traditional signatures, which authenticate documents, digital signatures utilize asymmetric cryptography for validation. By pairing a hash of the data with a private key, the sender can create a digital signature that can be verified by anyone possessing the corresponding public key. This method not only affirms the integrity of the data but also enables authentication of its origin. Significantly, when combined with symmetric encryption, this mechanism further reinforces confidentiality and integrity, creating a more robust data protection environment.
Created in a landscape filled with risk and threats, the intricacies of cryptographic principles underscore a continuous and evolving battle in the digital age. The fascination around symmetric encryption and its role in ensuring data integrity stems not from the technique itself but from the broader implications it invokes about trust, security, and the human need for privacy. As the digital landscape continues to evolve, so too must our approaches to safeguarding information. Strengthening the integrity of data through a multifaceted application of cryptographic principles exemplifies the inherent complexities and challenges faced within this domain.
In conclusion, symmetric encryption is a powerful tool for ensuring confidentiality, yet it possesses intrinsic limitations regarding data integrity. To authenticate integrity effectively, reliance on additional methodologies—such as hash functions and digital signatures—is indispensable. As the evolution of technology continues to mold the security landscape, the interconnectedness of these various techniques will prove crucial in addressing the ever-present threats to data integrity.





Leave a Comment