When considering the realm of digital security, understanding the intricacies of SSL (Secure Sockets Layer) encryption is paramount. One of the most frequently asked questions involves the role of asymmetric encryption within this framework. In this exploration, we’ll methodically dissect whether SSL employs asymmetric encryption, what that entails, and how it integrates with other encryption techniques to secure communications over the internet.
SSL, now largely superseded by Transport Layer Security (TLS), is a protocol used to establish a secure, encrypted link between a web server and a client, typically a web browser. The importance of this secure link cannot be overstated; with the proliferation of cyber threats, robust encryption standards are essential to safeguard sensitive data during transmission. But how do asymmetric and symmetric encryption interrelate within this protocol?
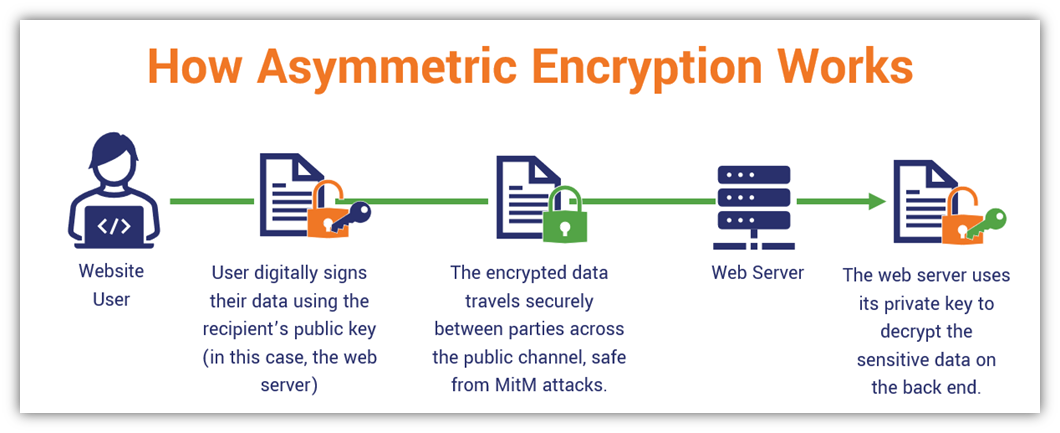
Asymmetric encryption is distinct in its operational methodology. It employs a pair of keys: a public key, which can be disseminated widely, and a private key, which must remain confidential to the owner. This dual-key system enhances security in ways that traditional symmetric encryption can’t achieve. In symmetric encryption, the same key is used for both encryption and decryption, which raises concern about key distribution — risk increases if the key falls into the wrong hands.
The SSL handshake process is the key moment where asymmetric encryption plays its crucial role. When a client attempts to connect to a secure server, the initial communication begins unencrypted. The server responds with its public key, which the client uses to generate a random session key. This session key, unique to that connection, is then encrypted using the server’s public key and sent back to the server. Only the server, holding the matching private key, can decrypt this information. Thus, asymmetric encryption ensures that even if the session key is intercepted, it remains protected due to the security of the private key.
After the handshake, the session key is employed for symmetric encryption for the duration of the session. Symmetric encryption is considerably faster than asymmetric encryption, making it more efficient for encrypting large volumes of data. This hybrid approach — leveraging the best of both encryption methodologies — underscores SSL’s efficacy in securing communications.
Another essential aspect of SSL’s operation is the implementation of digital certificates, which further utilize asymmetric encryption. A digital certificate, often issued by a trusted Certificate Authority (CA), serves multiple purposes: it verifies the server’s identity, ensures that the public key is authentic, and establishes a chain of trust that enhances the overall security framework. The certificate contains the public key and is signed by the CA’s private key, ensuring its integrity. This veracity is crucial for preventing man-in-the-middle attacks, where an adversary might attempt to intercept or alter communications between the client and server.
Moreover, SSL’s reliance on asymmetric encryption facilitates the establishment of new cryptographic standards. With the advent of quantum computing, traditional asymmetric algorithms, such as RSA, may become vulnerable due to their mathematical underpinnings. Newer algorithms are being designed to withstand such threats, ensuring that as technology evolves, so too does our capacity for secure communications. This dynamic nature of cryptography emphasizes the perpetual need for advancement in encrypted protocols.
In addition to the technical intricacies, the implementation of SSL tangentially intersects with broader implications for privacy and security on the internet. As users become increasingly aware of data breaches and the commodification of personal information, the demand for encryption methods that protect user data during transit heightens. SSL serves as a bedrock for e-commerce, online banking, and various digital communications, validating its essential role in fostering trust between users and service providers.
Overall, the interplay of asymmetric and symmetric encryption within SSL is a sophisticated convergence of technology aimed at securing digital communication. By utilizing asymmetric encryption during the initial SSL handshake, the protocol ensures secure key exchange before seamlessly transitioning into a more efficient symmetric encryption mode for the session’s duration. The inherent trust established through digital certificates further fortifies the security framework, illustrating the complexity and necessity of encryption in the digital age.
As consumers and professionals alike navigate the labyrinth of digital security, understanding the underpinnings of protocols such as SSL becomes increasingly important. Knowledge of encryption types and their applications can empower individuals to make more informed choices about the platforms and services they engage with, ultimately enhancing their digital safety. While the technical verbiage may appear daunting, grasping the basics provides foundational insight into the mechanisms that protect our most sensitive data from prying eyes.
In conclusion, while SSL prominently employs asymmetric encryption during its establishment phase, it is the hybridization with symmetric encryption that undergirds its widespread application and effectiveness. The combination of these two types of encryption not only optimizes performance but also extends robust security, making SSL a cornerstone of digital trust and safety across the web.







Leave a Comment