Cryptographic algorithms form the bedrock of modern digital security, serving as pivotal tools in protecting sensitive information from unauthorized access. As digital communication burgeons, the question arises: do cryptographic algorithms always need keys? At first glance, the answer seems to be a resounding yes, particularly in the context of conventional cryptographic methods. However, the landscape of cryptography is intricate and multifaceted, demanding a deeper exploration to uncover the nuances surrounding this assertion.
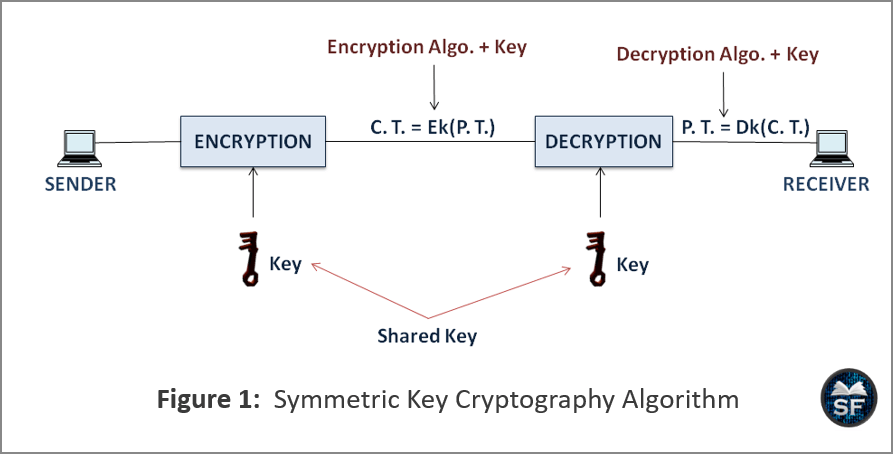
To embark on this journey, we must first delineate what cryptographic keys are and their quintessential role in various algorithms. In symmetric cryptography, both the encryption and decryption processes are governed by a single shared key. Conversely, asymmetric cryptography employs a pair of keys—public and private—where the public key is used for encryption, while the private key is reserved for decryption. This bipartite architecture serves to enhance security and facilitate secure communications without the necessity of exchanging secret keys beforehand.
However, while keys are integral to most cryptographic processes, there exist notable exceptions that warrant examination. One such exception lies within the realm of hash functions. Hashing algorithms, such as SHA-256 or MD5, transform an input (or ‘message’) into a fixed-length string of characters that appears random. Importantly, these algorithms do not require keys for their operations. Instead, they focus on producing a unique output for a given input. This property makes hash functions invaluable for data integrity verification, password storage, and digital signatures.
The absence of keys in hashing may provoke intrigue: how does this contribute to security? The answer lies in the concept of pre-image resistance—the difficulty of reconstructing the original message solely from its hash output. While this does not provide confidentiality in the traditional sense, it ensures that tampering or altering the data can be readily detected. Thus, in specific scenarios, hashing algorithms operate effectively without keys, challenging preconceived notions of cryptographic necessities.
Exploring further, we encounter another classification of systems termed ‘keyless encryption.’ Keyless encryption, while not a mainstream approach, raises curiosity about non-conventional methods of safeguarding information. These techniques often utilize mathematical constructs or algorithms that render information unintelligible without needing a key in the conventional sense. For instance, some systems capitalize on secret sharing, where a piece of information is divided into parts and distributed among different parties. Only a subset of those parts is required to reconstruct the original data, embodying a principle of distributed security rather than relying on a singular key.
Moreover, the necessity of keys is also contingent on the context and objectives of the cryptographic process. In scenarios ranging from secure communications to digital signatures, keys undeniably play a critical role. Nonetheless, when assessing the broader domain of cryptographic algorithms, we encounter instances of enciphering methods that yield utility irrespective of keys. Consider obfuscation techniques, where code or data is rendered unintelligible through transformations rather than traditional encryption. While strictly speaking, obfuscation is not cryptography per se, it serves a parallel purpose: protecting intellectual property and deterring unauthorized access.
Now, juxtaposing these methodologies invites contemplation on the implications of not utilizing keys. On one hand, the absence of a key can simplify processes and reduce complexity. For instance, hashing functions simplify data verification, enhancing efficiency. Conversely, forgoing keys may invite potential vulnerabilities. The reliance on other mechanisms such as computational complexity or mathematical randomness raises questions about their robustness under adversarial conditions. Are these systems resilient enough against sophisticated attacks? This ambiguity generates further curiosity about the trade-offs inherent in different cryptographic approaches.
As we navigate the ongoing evolution of technology, novel paradigms emerge. Quantum cryptography, once relegated to the realm of theoretical exploration, is now making tangible waves. Quantum key distribution (QKD) exemplifies this, employing quantum mechanics principles to facilitate secure key-sharing. Intriguingly, in QKD, the concept of keys prevails; however, the approach encapsulates a transformative shift in perception, positing that security itself can be fundamentally linked to the laws of physics rather than mere algorithmic complexity.
On another front, the rise of post-quantum cryptography fosters a reinvigoration of conventional cryptographic methodologies to withstand the advancements in quantum computing. Such developments beckon inquiries about the long-standing dependence on keys in an era defined by transformational challenges and opportunities. Consequently, does our reliance on keys in cryptography illustrate resilience or limitation? This reflection invites consideration of potential future paradigms where the relationship between keys and algorithms may not be as dichotomous as it appears today.
In summation, while traditional cryptographic algorithms predominantly rely on keys, exceptions abound, revealing an intricate tapestry of methods. Hash functions, keyless encryption systems, and obfuscation techniques exemplify the diversity of approaches transcending the key-centric paradigm. The discourse around keys and their necessity is not merely a question of functionality; instead, it propels a broader narrative into the essence of security itself. It compels the community to re-evaluate the core principles underpinning cryptographic practices as they adapt to the relentless advancement of technology. The journey into the enigma of cryptography teems with curiosity, inviting further exploration and fostering a profound appreciation of the art and science that protect our digital world.






Leave a Comment