Encryption is a fundamental aspect of information security. It protects data from unauthorized access, ensuring confidentiality and integrity in communication. This intricate field is often characterized by its reliance on keys, but the assertion that all forms of encryption necessitate keys warrants examination. This article delves into the complexities of encryption, exploring the nuances of key utilization and the intriguing notion that some secrets don’t require locks.
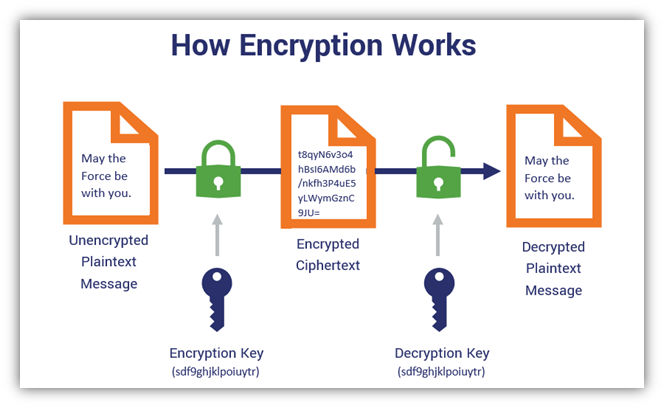
At the heart of traditional encryption lies the concept of keys. In symmetric encryption, a single key is utilized for both the encryption and decryption processes. This shared secret must be securely exchanged between the communicating parties prior to any data transmission. In contrast, asymmetric encryption employs a pair of keys: a public key, which can be freely distributed, and a private key, which remains confidential with the key owner. This dual-key method enhances security by allowing individuals to exchange information openly without the need for prior secret exchanges.
However, while keys are central to many encryption frameworks, not all methods rely on them in the traditional sense. To elucidate this point, let us consider the world of steganography. Steganography obscures the existence of a message rather than encrypting its contents. By concealing data within other non-secret data—such as an image or audio file—it renders the very notion of encryption obsolete for the concealed information. In this framework, no keys are necessary; the secret exists within plain sight, albeit hidden in an intricate veil.
Moreover, there exists the realm of homomorphic encryption, a revolutionary concept allowing processing on encrypted data without requiring access to the keys. Through this methodology, computations can be performed directly on ciphertexts. The results, once decrypted, reflect the outcome of the same operations as if they had been executed on the plaintext data. Such an approach implies that keyless operations can be achieved within the secure confines of encrypted environments, challenging conventional perceptions of the reliance on keys.
It is critical to understand, however, that the absence of traditional keys in certain scenarios does not imply an absence of security. In fact, the robustness of a keyless system hinges upon different principles. For instance, steganography capitalizes on the psychological perception of secrecy. The effectiveness of steganographic techniques depends largely on the assumption that an observer is unaware of the hidden message, unlike encryption, which operates under the presumption that an attacker may have knowledge of the encryption method but lacks the key. Each methodology carries its own strengths, weaknesses, and contexts wherein it shines.
Consider also the phenomenon of hashing—a cryptographic process that converts input data into a fixed-size string of characters through a one-way function. Hashing is not encryption in the traditional sense but serves as a vital mechanism in verifying data integrity. Passwords, for example, are often hashed prior to storage. This system inherently lacks a key because the original input cannot be regenerated from its hash. Instead, it relies on comparative checks against the stored hash, further complicating the conversation on keys and confidentiality.
Inherent in the discussion of keys is a broader philosophical inquiry into the nature of security itself. Should keys be regarded merely as access tools, or do they represent a deeper commitment to data protection? Tightly held keys offer security, yet they can also become points of failure. The loss of a key leads to irrevocable data loss, raising critical questions about access, control, and the implications of cryptographic dependence.
Alternatively, consider the development of zero-knowledge proofs, intricate cryptographic protocols allowing one party (the prover) to validate a statement to another party (the verifier) without revealing the content of the statement itself. This allows for verification without disclosing the secret information, creating a unique paradigm where the secrets do not necessitate traditional locks and keys. Zero-knowledge proofs highlight an evolution in cryptographic technology that challenges long-held beliefs surrounding the necessity of encryption keys.
As we parse through these various forms of encryption and their differing relationships with keys, it becomes apparent that the landscape of information security is dynamic, often defying simplistic categorizations. Technologies evolve, and with this evolution come changing definitions of what constitutes security and confidentiality.
Moving forward, it is essential for stakeholders in the digital realm, from individuals to corporations, to cultivate a nuanced understanding of encryption. The conversation cannot merely dwell upon keys as synonymous with security; rather, it should encompass a broader dialogue about the methodologies employed to secure information. In a world increasingly reliant on digital communications, recognizing the diversity of approaches to information security will pave the way for more resilient and effective defenses.
Ultimately, while the classical paradigms of encryption revolve around keys, the broader landscape reveals a myriad of options worthy of exploration. The idea that “not all secrets need locks” fosters curiosity and a thirst for understanding. This shift in perspective unveils the multifaceted nature of encryption and invites further investigation into the ever-evolving technologies that seek to protect our most sensitive information.







Leave a Comment