Encryption, at its core, is a fundamental aspect of modern cryptography—an essential tool for protecting information in an age where data breaches and cyber threats loom large. A critical element of encryption is the key, which serves as the mechanism that transforms plaintext (readable data) into ciphertext (encoded data) and vice versa. However, the assertion that “all encryption types use keys” is not quite as straightforward as it seems. The landscape of encryption is intricate, and its variations can make even seasoned cryptographers scratch their heads. In delving into this complex realm, one discovers the tantalizing nuances of encryption methodologies.
To begin with, it’s important to define what is meant by “keys” in this context. In cryptographic terminology, keys are strings of data used by algorithms to encrypt and decrypt information. They are typically nuanced in length and composition, leading to varying levels of security. The key’s strength is often proportional to its length; the longer the key, the harder it is to crack. Common symmetric key lengths include 128, 192, and 256 bits, while asymmetric keys tend to be longer, starting at 2048 bits and extending to 4096 bits or more. However, as the importance of keys is perhaps too readily assumed, a closer examination of different encryption types is warranted.
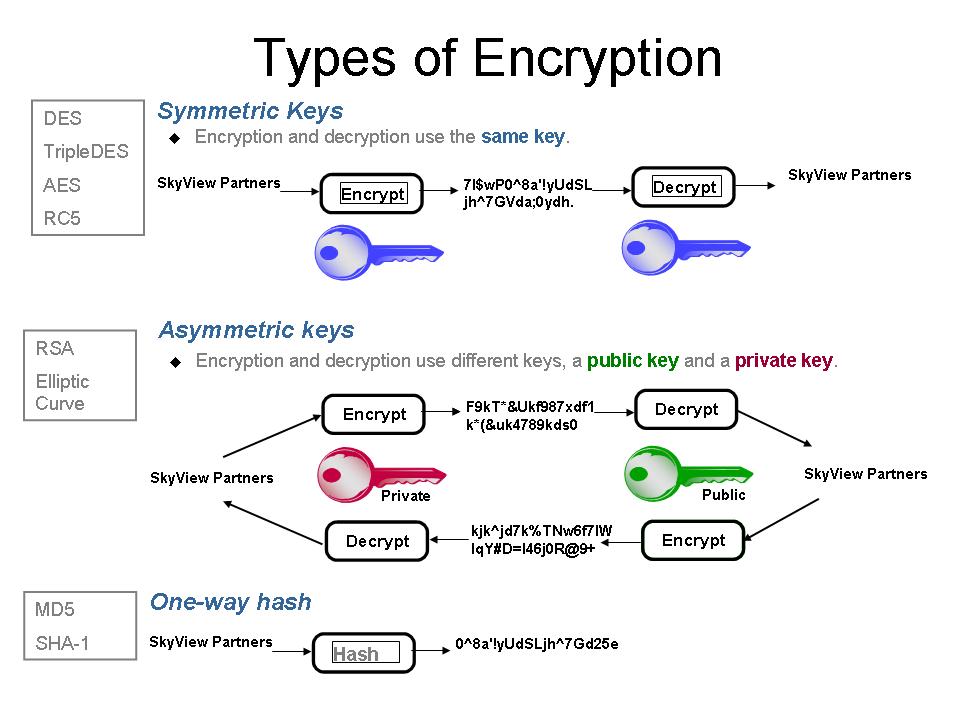
Encryption can be broadly categorized into two types: symmetric and asymmetric. Symmetric encryption, as the name implies, utilizes the same key for both encryption and decryption. This means that both parties involved in communication must possess the same key, creating an inherent dilemma: if transmission of this key is compromised, so too is the security of the entire communication. Popular algorithms for symmetric encryption include the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES), both of which epitomize the conventional reliance on keys.
On the contrary, asymmetrical encryption contrives a clever solution to the sharing key problem. Utilizing a pair of keys—one public and one private—this method allows secure communication without the necessity of exchanging a shared secret. The public key, which can be widely disseminated, is used to encrypt the data, while the private key, kept secure by the owner, is required to decrypt it. This ingenious system underlies protocols like RSA (Rivest-Shamir-Adleman) and has birthed the dazzling landscape of public key infrastructure (PKI). Here, the relationship between the keys is what ultimately enables secure exchanges.
But the conversations surrounding encryption aren’t limited to these two major categories. There exist other convoluted forms—often classified under the umbrella of keyless encryption or non-key-based encryption. At this juncture, the notion of “keys” becomes substantially murkier. A prime example is homomorphic encryption, which allows computations to be performed on ciphertexts without needing access to the keys. This method is groundbreaking because it preserves confidentiality even during processing, yet it operates under principles that defy traditional understanding of keys in cryptography.
Furthermore, concepts like hash functions further complicate the notion of key usage. A hash function converts data into a fixed-size string of characters, which is unique to each input. While hash functions do not encrypt data in a reversible manner like traditional systems, they inherently do not require keys. Instead, they ensure data integrity by producing a hash value that can confirm whether the original data has been altered. When stored passwords are handled, for example, hashes facilitate a comparison without ever revealing the original data. This creates an interesting dichotomy between encryption and hashing.
In exploring these distinctions, a salient observation emerges: not all encryption relies on conventional key usage. Keyless approaches illustrate that while keys are indispensable for many traditional encryption techniques, there are equally valid methodologies that eschew them altogether. Furthermore, one must also consider the growing disinclination to use traditional keys in some sectors, as data security protocols evolve in response to increasing threats. Innovators in the cryptography world are continually seeking creativity in data protection methods, leading to the development of more nuanced strategies.
The implication of such advancements raises another pivotal question: Do we still need keys in a rapidly evolving digital age? As quantum computing approaches, traditional cryptographic algorithms become vulnerable to novel attacks. This progression foretells the emergence of quantum-resistant algorithms, potentially revolutionizing how keys are utilized—or even rendered obsolete entirely. Cryptography must therefore remain agile, dynamically adapting to the shifting bedrock of technological capability.
In conclusion, while it is easy to think of encryption primarily in terms of keys, the reality is far more intricate and multifaceted. Symmetric and asymmetric encryptions solidify the importance of keys, while burgeoning techniques like homomorphic encryption and hash functions showcase alternatives that challenge conventional paradigms. The landscape of cryptography is replete with opportunities for innovation, urging those involved to reassess what “use of keys” fundamentally entails. Consequently, this invites not only analytical inquiry but a reorientation of perspective on how secure communication will evolve in a complex digital ecosystem.







Leave a Comment