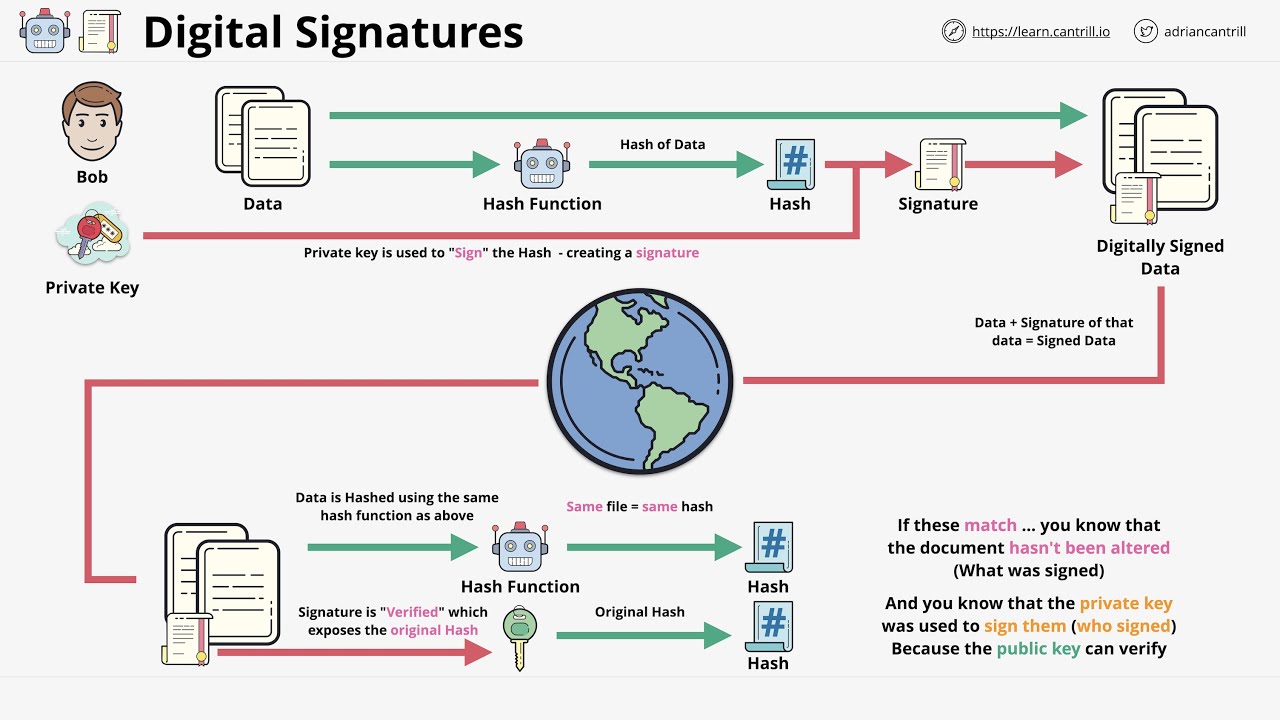
Digital signatures represent a pivotal advancement in the realm of cryptography, significantly enhancing the integrity and authenticity of digital communications. As the digital landscape becomes increasingly populated with sensitive information, the mechanism of digital signatures emerges as an indispensable tool for securing the integrity of these communications. In essence, a digital signature is akin to a handwritten signature or a stamped seal, but it employs cryptographic techniques to provide a far greater level of security.
At its core, a digital signature involves the use of a cryptographic key pair: a private key and a public key. The private key, which is kept secret by the signer, is used to generate the digital signature, while the public key is shared with recipients to verify that the signature is valid. This two-key system ensures that, should the private key remain confidential, the integrity of the data can be assured.
One of the critical functions of a digital signature is to maintain the integrity of the message being transmitted. Integrity, in this context, refers to the assurance that the message has not been altered in transit. When a sender signs a message with their private key, a unique hash is created; even the slightest modification to the message will result in a completely different hash value. This property of digital signatures is what guards against tampering. If the recipient can successfully verify the signature using the sender’s public key, they can be confident that the message remains unchanged from the point of its origin.
Moreover, digital signatures provide non-repudiation. This implies that a signer cannot later deny having signed the message. To elaborate, once a signature is affixed to a piece of data, the signer is bound to that action, which is an essential aspect in legal and fiscal environments. The implications of non-repudiation extend beyond merely establishing accountability; they are crucial in compliance with various regulatory frameworks that necessitate validated documentation of transactions.
When delving into implementations, various algorithms can be employed to produce digital signatures. Some of the most common algorithms include RSA (Rivest-Shamir-Adleman), DSA (Digital Signature Algorithm), and ECDSA (Elliptic Curve Digital Signature Algorithm). Each of these has its own theoretical underpinnings and applications based on the desired balance between security and computational efficiency.
RSA, for instance, is one of the oldest public key cryptosystems and is widely used today. It operates on the mathematical difficulty of factoring the product of two large prime numbers. The security afforded by RSA increases with key size; however, larger keys demand more processing power for both signature generation and verification.
On the other hand, DSA was specifically designed for digital signatures and does not provide encryption capabilities. Instead, it focuses on producing signatures rapidly, making it ideal for contexts where speed is paramount. This algorithm is predicated on the difficulty of computing discrete logarithms, with its strengths lying in the efficiency of signature generation.
In contrast, ECDSA efficiently utilizes the properties of elliptic curves to derive a robust signature scheme. It offers equivalent security to RSA with significantly shorter key lengths, leading to less memory overhead and quicker computations. This efficiency makes ECDSA increasingly prevalent in mobile applications and constrained environments.
There are also digital signature standards that help to manage how digital signatures should be formatted and used. Notable among these is the Public Key Infrastructure (PKI), which establishes a framework for managing digital certificates and signatures. PKI enables the validation of identities and the secure exchange of public keys, thus fortifying the trust model within digital communications.
With the surge in digital transactions, the relevance of safeguarding information through digital signatures cannot be overstated. E-commerce platforms, governmental bodies, and financial institutions increasingly rely on these cryptographic protocols to ensure the security of sensitive transactions. For instance, when a user submits a tax return electronically, the signature verifies their identity and affirms that the data has not been manipulated.
Despite their robust advantages, it is important to remain cognizant of potential vulnerabilities. For instance, if a private key is compromised, any data signed with that key becomes subject to fraudulent activities. Additionally, reliance on outdated or compromised hashing algorithms can present significant risks, as advancements in computing power can render them vulnerable to cryptographic attacks.
In conclusion, digital signatures are a cornerstone of modern digital communications, providing not only integrity and authenticity but also non-repudiation. The diverse array of algorithms allows for tailored implementations across various applications, ensuring that the right balance of security and efficiency is achieved. As digital interactions continue to proliferate, the role of digital signatures in maintaining secure communications will only increase, catalyzing innovations in cybersecurity practices and shaping the future of digital integrity.







Leave a Comment