In the complex landscape of modern cryptography, the Diffie-Hellman key exchange stands out as a pivotal mechanism, akin to a secret handshake shared among trusted allies. This algorithm enables two parties to securely exchange cryptographic keys over a public channel, laying the groundwork for encrypted communication. Understanding its applications in the real world reveals not only its technical brilliance but also its significance in our digitally connected lives.
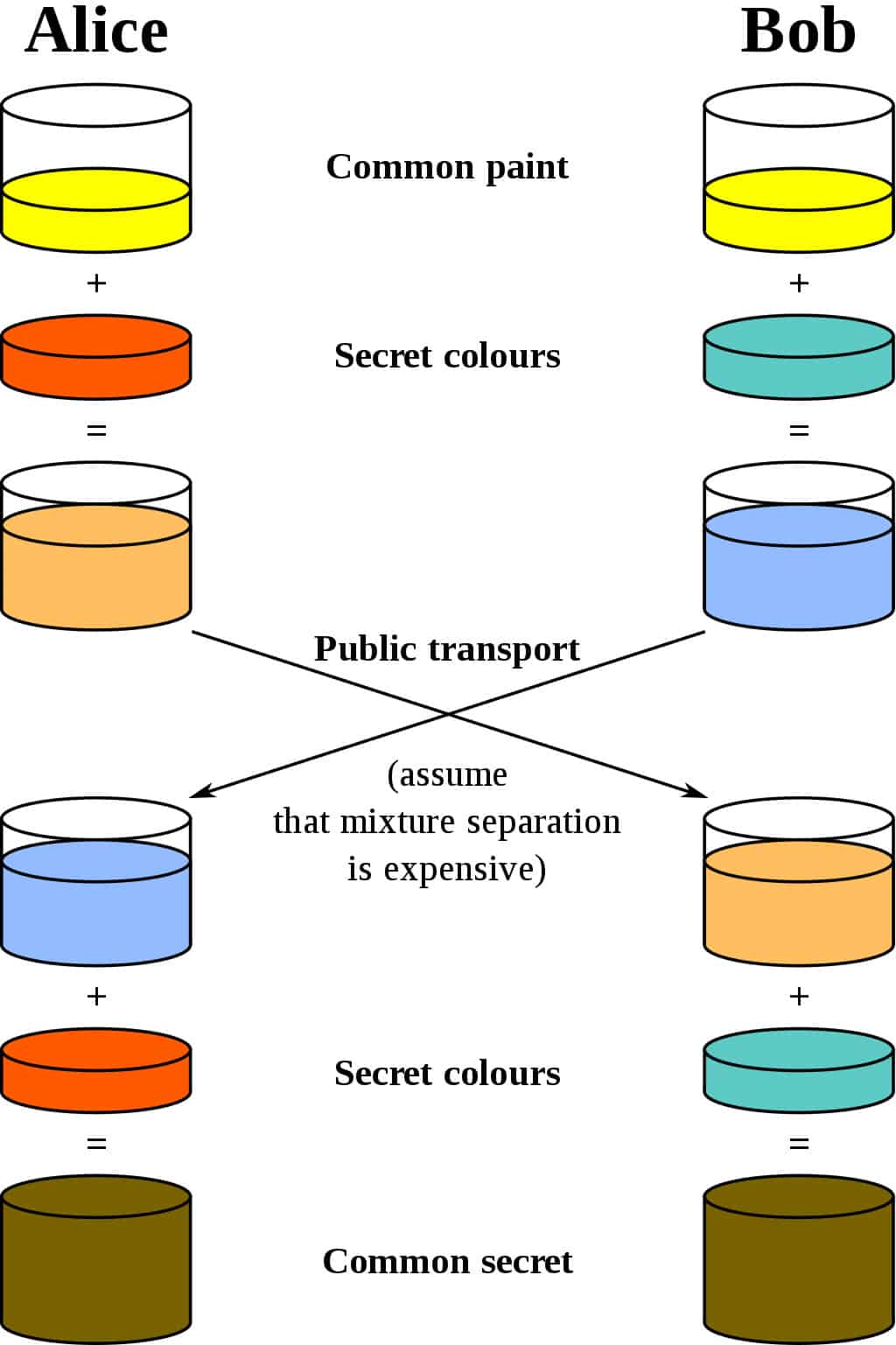
To comprehend the practicality of the Diffie-Hellman algorithm, one might envision an exquisite vault, guarded by two sentinels who, unbeknownst to each other, are tasked with securing a treasure. Without meeting face to face, they rely on their individual abilities to construct a shared key that will unlock the vault. This analogy illustrates the elegance of Diffie-Hellman: it allows secure keys to be generated and exchanged without necessitating a secure line of communication.
Diffie-Hellman’s initial foray into the real world was primarily within academic circles, yet it swiftly garnered traction across various sectors. Today, its applications permeate through numerous technologies, shaping the underpinnings of secure communications in an increasingly vulnerable cyber landscape.
The Web and E-Commerce
Online shopping has transformed the retail experience, but it comes with inherent risks. Enter the Diffie-Hellman key exchange, which facilitates secure transactions and data integrity during an online purchase. By using this algorithm, ecommerce platforms can establish a secure channel for users to input sensitive information, such as credit card details and personal addresses, ensuring that these data remain shielded from prying eyes.
When you click ‘Checkout’ on an online retailer, the page doesn’t merely transport you to a payment gateway. It utilizes Diffie-Hellman to negotiate session keys that encrypt the entire transaction process. This means your financial information is transformed into an impenetrable code, a fortress against potential data breaches.
Secure Messaging Applications
In an age where information travels at the speed of light, confidentiality is paramount. Messaging apps like WhatsApp and Signal have harnessed the power of the Diffie-Hellman algorithm to ensure that conversations remain private. By employing end-to-end encryption through this key exchange, these applications create a secure space where only the intended recipients can decipher the message.
Every time a message is sent, the devices involved generate unique session keys using Diffie-Hellman. Imagine sending a letter sealed with a cryptographic wax seal; only the intended receiver possesses the wax stamp to unseal it. This process equips users with the confidence that their exchanges—whether of mundane updates or sensitive details—are shielded from interception.
Virtual Private Networks (VPNs)
With the increasing prevalence of remote work, VPNs have become essential by safeguarding users’ online activities from eavesdropping. At the heart of many VPN implementations is the Diffie-Hellman key exchange, which serves as a mechanism to create secure tunnels over the internet.
Connecting to a VPN can be likened to locking an intricate door when entering private territory. Through Diffie-Hellman, the VPN server and the user’s device collaborate to generate a transient shared key. This key is subsequently utilized to encrypt the data traversing the network, thus ensuring that even if a malicious actor were to intercept the traffic, deciphering the data would be an insurmountable challenge.
Blockchain Technology
In the realm of blockchain, secure transactions and trustworthiness are fundamental. While many discussions about security focus on hashing and digital signatures, the Diffie-Hellman algorithm plays a crucial role in establishing secure peer-to-peer interactions. It is utilized in various cryptocurrencies and decentralized applications to facilitate the secure exchange of keys between users.
Financial transactions within a blockchain can be an intricate dance, where each participant must have faith not only in the technology but also in the protocols that govern it. When users set up wallets or participate in decentralized finance (DeFi), Diffie-Hellman serves as the hidden force that underpins their confidence in the security and integrity of their exchanges.
Internet of Things (IoT)
The proliferation of IoT devices introduces another layer of complexity to security concerns. From smart home appliances to wearable technology, these devices often communicate over public networks, which makes secure communication paramount. Implementing Diffie-Hellman within IoT devices allows for establishing secure channels without the need for pre-shared secrets or complicated key management rituals.
Picture a smart thermostat that not only detects the ambient temperature but also clandestinely communicates with your smartphone. The secure channel negotiated through Diffie-Hellman ensures that your preferences and usage data remain private, protecting them from unauthorized access. As the IoT ecosystem expands, the role of Diffie-Hellman in maintaining data integrity and privacy cannot be overstated.
The Future of Diffie-Hellman
As technology evolves, the implications and potential applications of Diffie-Hellman will likely expand in tandem. Innovations in quantum computing pose new challenges, yet efforts such as post-quantum cryptography aim to protect key exchanges against future threats. The adaptability of Diffie-Hellman not only speaks to its robustness but also underscores its importance within the ever-changing landscape of digital security.
In conclusion, the Diffie-Hellman key exchange is not merely a theoretical construct but a practical solution that underlies the security architecture of numerous modern technologies. From ensuring the confidentiality of online transactions to safeguarding our communication in an increasingly interconnected world, Diffie-Hellman has woven itself into the very fabric of our digital existence. As we continue to navigate through the complexities of technology, the quiet elegance of this algorithm will likely remain a steadfast ally in the quest for secure communications.







Leave a Comment