In the realm of cryptography, the phrase “Decrypting with a Public Key” often evokes a chiaroscuro of intrigue and skepticism. For many, the concept seems counterintuitive, layering impenetrable complexity over what appears to be a straightforward process. At its essence, it invites a slew of questions: Can public keys truly decrypt data? What mechanisms underlie such a phenomenon? And importantly, how can one delineate between fact and fiction when navigating the intricacies of public key cryptography?
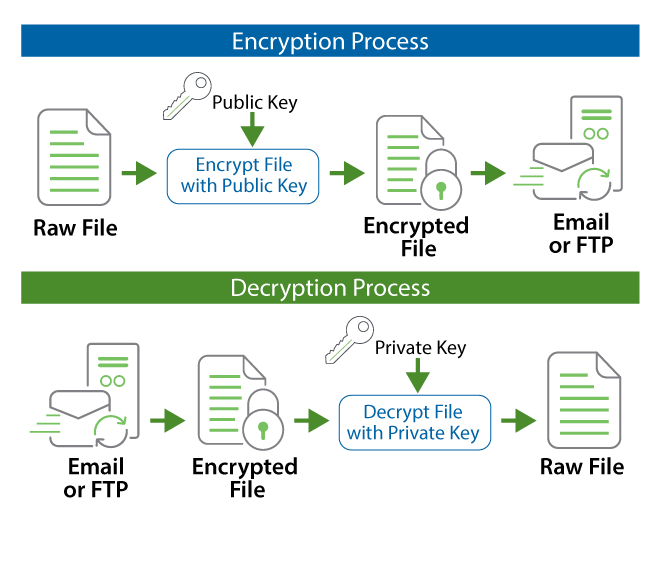
The fascination with public key cryptography lies not simply in its operational mechanics but also in its broader implications for data security and privacy. Public key infrastructure (PKI) operates on the principle of dual keys—one public and one private—each serving distinct yet complementary functions. The public key, as its nomenclature suggests, is available to anyone wishing to send confidential information. The enigmatic attributes of the private key, however, provide the requisite access to decrypt that information, thus establishing a one-way encryption loop that fosters trust in a digital age.
To comprehend the dissonance surrounding public key decryption, one must first delineate its architectural framework. In traditional symmetric cryptography, a single key suffices for both encryption and decryption. This dual-functionality simplifies the exchange but simultaneously poses a significant risk. If the key is intercepted, adversaries can access secure information with ease. Public key cryptography mitigates this risk by separating these two functionalities, enhancing the overall security landscape.
Nonetheless, the adoption of public key cryptography has fostered misconceptions about its capacities. A common misconception posits that public keys can decrypt data independently. This belief stemmed from an oversimplification of the cryptographic process. In actuality, a public key serves to encrypt data, while only its associated private key possesses the requisite capability to reverse this encryption. Thus, while public keys facilitate an initial layer of security, they do not wield the power to decrypt information autonomously.
Addressing this common observation leads us to consider the implications of understanding key functions within cryptographic systems. The allure of public key cryptography stems not just from its technological prowess, but rather from the philosophical questions surrounding trust and accessibility. By making one-half of the equation publicly accessible, cryptography promotes transparency, heightening the perceived safety of confidential transactions. However, it simultaneously raises nagging concerns about ownership and assurance.
The dichotomy between fact and fiction in this context extends beyond mere technicalities. Consider the latent social constructs that emerge from the implementation of public keys. When individuals place their trust in a public key, they do so based on an implicit understanding of the underlying assumptions regarding security, authenticity, and the very architecture of the Internet. The public key signifies a handshake of sorts, a digital acknowledgment that while the data remains accessible, the requisite tools for decryption are securely safeguarded away from prying eyes.
This interplay between trust and accessibility becomes particularly evident in real-world applications. For instance, consider the realm of secure communications. Individuals utilize encryption tools to safeguard their conversations against unauthorized interception. Here, the public key can encrypt the message, while the private key remains securely ensconced within the user’s device. Yet, should an individual inadvertently expose their private key—be it through malware, phishing attacks, or negligence—the purported security evaporates, exposing them to myriad vulnerabilities.
Moreover, the evolution of cryptographic standards has introduced another layer to this nuanced dialogue. As technology progresses, cryptographic techniques evolve concurrently, leading to new standards and practices. The continuous push for stronger, more resilient encryption methods compounds the complexity of public key usage. As quantum computing looms on the horizon, concerns about the longevity of traditional public key systems have made the discourse richer and more relevant, substantiating the argument for continued education and adaptation within the field.
This multifaceted relationship between public key cryptography and societal trust encapsulates the deeper reasons for fascination in the narrative surrounding decryption. Many find allure in the dualities— of public and private, trust and vulnerability, fact and fiction. These divisions prompt critical questions that extend far beyond technical correctness. They incite contemplations about the very nature of information security and the ethical implications of technology in our daily lives.
In conclusion, while the assertion that “Decrypting with a Public Key” hinges on a misinterpretation of cryptographic principles is factual, it also serves as a keystone for broader contemplation. The journey through the landscape of public key cryptography reveals an intricate web of trust, transparency, and security. To navigate this terrain effectively, one must embrace the complexities therein, ultimately recognizing that while public keys are essential for enhancing encrypted communications, they cannot function as standalone tools for decryption. Instead, they thrive within a larger ecosystem, one that underscores the importance of safeguarding private keys and fostering an informed dialogue about the implications of encryption in our increasingly interconnected world.







Leave a Comment