The Advanced Encryption Standard (AES) has garnered significant attention in the realms of cybersecurity and data management. Its ubiquity signifies trust; it is the backbone of secure communications, protecting sensitive information against unauthorized access. However, inherent in the discussion about AES is a question that has ignited fervent debate: Can AES be reversed? This inquiry delves deeply into the heart of cryptographic principles, addressing not only the mechanics of encryption and decryption but also the philosophical implications of information security in our increasingly digital world.
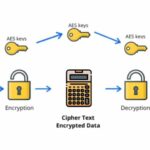
AES operates as a symmetric-key algorithm, meaning the same key is utilized for both encryption and decryption. This methodology offers a duality that simplifies key management but also invites scrutiny regarding key recovery and vulnerabilities. At its core, AES is predicated on transforming plaintext into ciphertext using a series of well-defined mathematical operations, encompassing substitution, permutation, and mixing. Each of these operations is meticulously designed to obfuscate the original data, complicating any attempts at reversal without the key. However, the mere existence of such an encryption standard does not preempt the inherent fascination and speculation surrounding its potential reversibility.
One area of heightened concern is the possibility of cryptographic weaknesses emerging over time due to advances in computational power or theoretical breakthroughs. Some may recall historical events where previously deemed secure encryption standards, like DES (Data Encryption Standard), became effectively obsolete due to the relentless march of technological progress. The fascination surrounding AES’s longevity stems from its adoption as a standard endorsed by organizations such as NIST (National Institute of Standards and Technology), with the expectation that it will endure against future cryptanalytic efforts.
Within this discourse lies a fundamental tension between security and accessibility. On the one hand, AES is designed to be robust against brute-force attacks, wherein an adversary systematically attempts every possible key combination until the correct one is uncovered. With a key size of up to 256 bits, the number of potential keys is astronomical. Still, the evolution of quantum computing introduces a new variable that could destabilize the traditional understanding of encryption. Quantum algorithms, such as Grover’s algorithm, threaten to reduce the effective key space for symmetric-key cryptography, which indirectly influences the perception of AES’s reversibility. It prompts the inquiry: Could there come a time when AES is no longer impervious?
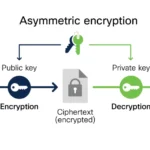
Further complicating this debate are the ethical dimensions surrounding access to encrypted data. In certain scenarios, law enforcement or national security agencies advocate for a backdoor access mechanism, which would ostensibly provide them with the capability to decrypt AES-encrypted data when necessary. This proposition generates a multifaceted dialogue about the balance between public safety and individual privacy rights. While some may perceive the potential for backdoors as a necessary compromise, others argue it fundamentally undermines the core tenets of encryption; creating vulnerabilities invites abuse and erodes trust in digital infrastructures.
The discussion of reversibility also encompasses the concept of cryptographic failures. In any encryption method, both systemic and operational flaws can manifest. A theoretical reverse engineering of AES could hinge not only on the mathematical robustness of the algorithm itself but also on human error—the exposure of encryption keys through poor management practices, for instance. The dichotomy between flawless encryption and practical implementation renders the question of AES’s reversibility all the more urgent and layered. Every encryption standard rests on the assumption of fail-proof execution, yet the reality remains precarious.
Moreover, adversarial testing of AES—a practice where security experts attempt to exploit weaknesses in the algorithm—reflects a growing trend within the cybersecurity domain. As researchers endeavor to unearth potential vulnerabilities, the question of reversibility becomes less an argument against AES, and more a testament to the dynamic nature of cryptography. Success in these tests does not merely affirm that AES can be reversed; rather, they reveal the relentless pursuit of knowledge within the field. Each flaw detected contributes to an evolving discourse on the efficacy of AES in practical, real-world applications.
As we navigate the contemporary landscape of cybersecurity, the role of user behavior cannot be understated. Encryption may provide a formidable barrier, yet it cannot shield users from all external threats. Phishing attacks, social engineering, and various forms of malware can circumvent even the most sophisticated encryption. Hence, while AES is seemingly impervious under certain conditions, the broader question of overreliance on encryption surfaces. This brings forth another layer of complexity: Is the fascination with reversing AES symptomatic of a deeper discomfort with the vulnerabilities that exist outside the realm of encryption?
In conclusion, while the technical architecture of AES yields a rarefied barrier to reversal, the socio-political, ethical, and operational contexts to which it pertains heightens the intrigue of the debate. The question of AES’s reversibility compels us to consider not only the limits of technology but also the responsibilities we shoulder as a society in protecting our data. Ultimately, as we stand at the intersection of innovation and security, our curiosity regarding AES reflects a broader quest for understanding in an age that is increasingly reliant on encrypted information. This fascination underscores humanity’s enduring interest in safeguarding knowledge in a world where the boundaries between security and accessibility are ever murky.





Leave a Comment