Cryptography, the art and science of encoding and decoding information, has evolved significantly since its nascent stages rooted in ancient civilizations. Historically, cryptography encompassed classical ciphers, primarily characterized by simplicity and reliance on mathematical intuition. However, as the digital age dawned upon us, the increasing demand for secure communication propelled the field into more advanced realms. Today, we stand on the precipice of a transformative epoch—one that amalgamates classical foundations with the revolutionary paradigm of quantum cryptography. This discourse elucidates the trajectory of cryptography from its rudimentary beginnings to the complexities of quantum realms.
To comprehend the future, one must first revisit the fundamentals of classical cryptography. The early methods, including Caesar ciphers and Vigenère ciphers, were groundbreaking at their time but fundamentally limited in security. The well-defined key systems permitted only a finite number of possibilities, making them susceptible to frequency analysis and brute-force attacks. As technology evolved, so too did the methods of cryptography, leading to the development of symmetric and asymmetric encryption systems. The Data Encryption Standard (DES) and later, Advanced Encryption Standard (AES), represented substantial advancements that utilized intricate algorithms to secure data.
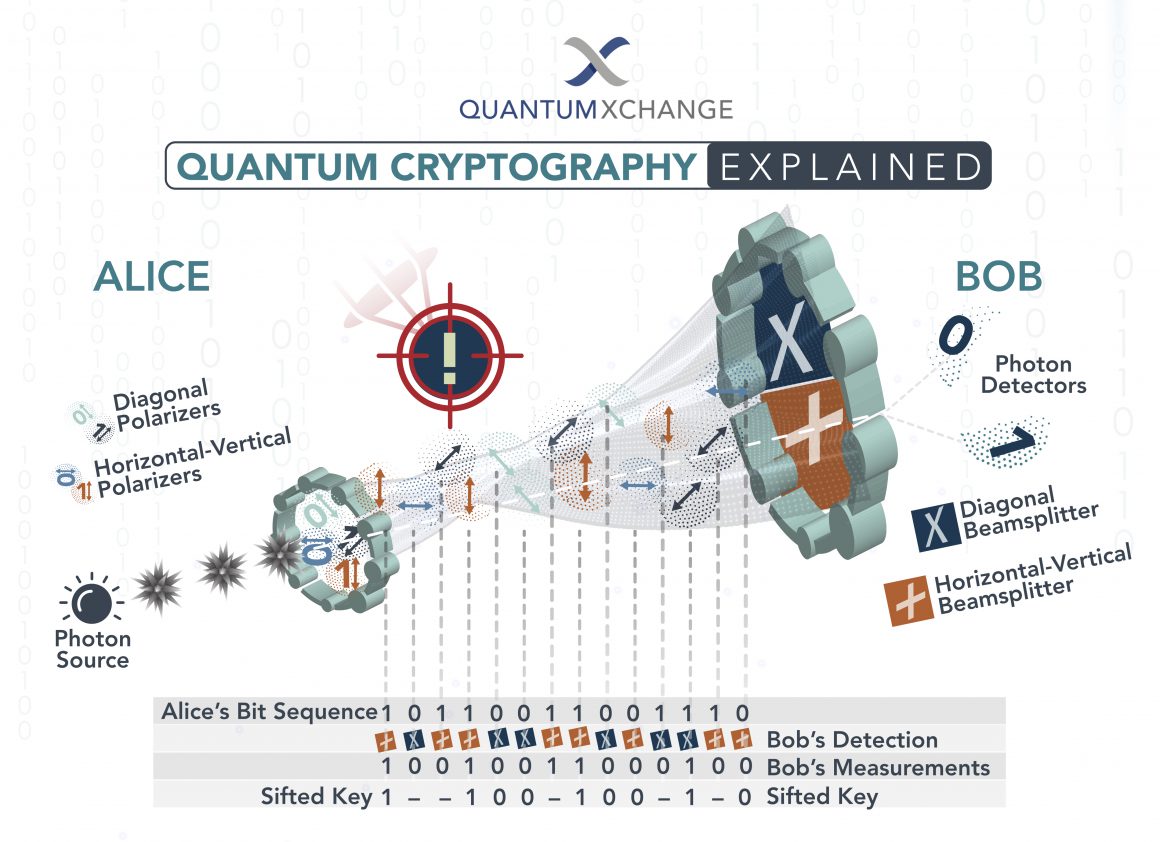
Despite these advancements, the advent of quantum computing incited a seismic shift in the cryptographic landscape. Quantum computers, leveraging the principles of quantum mechanics, possess the potential to execute calculations at speeds unfathomable by classical computers. This capability renders many classical encryption techniques obsolete, laying bare an urgent need for alternative security paradigms. The crux of the impending cryptographic revolution is quantum cryptography, encompassing methodologies like Quantum Key Distribution (QKD), which promises theoretically unbreakable encryption.
Quantum Key Distribution operates on the principles of quantum mechanics, utilizing the peculiar behavior of quantum bits, or qubits. Through the phenomenon of superposition and entanglement, QKD allows two parties to share a secret key with a level of security that is unattainable by classical means. Even if an adversary attempts to eavesdrop, any interception of the quantum state alters the information being transmitted, alerting the parties to the compromise. Thus, the integrity of the communication is preserved, fostering a paradigm of trust that has not been witnessed in the annals of cryptography.
A pivotal aspect of quantum cryptography is its ability to address challenges posed by the burgeoning threat of quantum hacking. Classical systems are fundamentally vulnerable to quantum algorithms, particularly Shor’s algorithm, which efficiently decomposes large integers. This vulnerability could undermine current encryption standards like RSA and ECC, which form the backbone of secure communications on the internet. Quantum cryptography offers a robust countermeasure against such threats, yet the transition from traditional to quantum systems presents multifaceted challenges.
As we gaze into the future of cryptography, it becomes imperative to consider the implications of integrating quantum methodologies into existing infrastructures. The transition requires not only technological adaptations but also a cultural shift in how security is perceived and implemented globally. Institutions and organizations must prioritize research into quantum-resistant algorithms, ensuring that they remain a step ahead in the arms race against cyber threats. The journey toward complete integration of quantum cryptography will undoubtedly be gradual, necessitating collaboration between academic institutions, private sector innovators, and governmental entities.
Furthermore, the ethical implications of quantum cryptography and its potential to reshape privacy standards warrant meticulous examination. In an era where personal data breaches and surveillance are rampant, the advent of quantum encryption heralds an opportunity to redefine personal privacy. However, the power of quantum cryptography also raises concerns about its application in nefarious conducts, such as authoritarian surveillance. Hence, establishing regulatory frameworks that govern the responsible use of quantum technologies is a pressing necessity.
Concurrent with the rise of quantum cryptography, there exists an emerging discourse surrounding neuromorphic computing and its possible intersection with cryptographic endeavors. Neuromorphic systems, modeled after the human brain, offer the potential to enhance machine-learning capabilities, fostering more adaptive and intelligent encryption methods. This intersection of artificial intelligence and cryptography could yield more resilient systems capable of self-evolving and counteracting sophisticated cyber adversaries.
As we extrapolate further into the future, the landscape of cryptography will likely be influenced not only by advancements in quantum computing but also by societal demands for security and transparency. The future will necessitate a symbiotic relationship between cryptography and policy-making, as both fields must converge to illuminate ethical considerations while redefining the principles of confidentiality and authenticity within digital communications.
The prospects of cryptography, driven by quantum advancements, are vast and intricate. As we stand at this juncture, a paradigm shift is not just anticipated; it is imminent. The dynamics of security, privacy, and communication are on the verge of transformation, beckoning researchers and practitioners alike to delve into the enigmatic yet captivating realms of quantum cryptography. Such exploration promises not only to redefine our understanding of security but also to awaken curiosity and ignite innovative solutions to the challenges faced in the ever-evolving digital landscape.







Leave a Comment