In the intricate world of cryptography, the ability to both encrypt and decrypt data is quintessential; however, the question arises: can we effectively utilize different key lengths for these operations? This exploration introduces metaphorical perspectives to grasp the broader implications of key lengths in encryption, similar to a masterful painter who selectively employs various brush sizes to create a harmonious work of art.
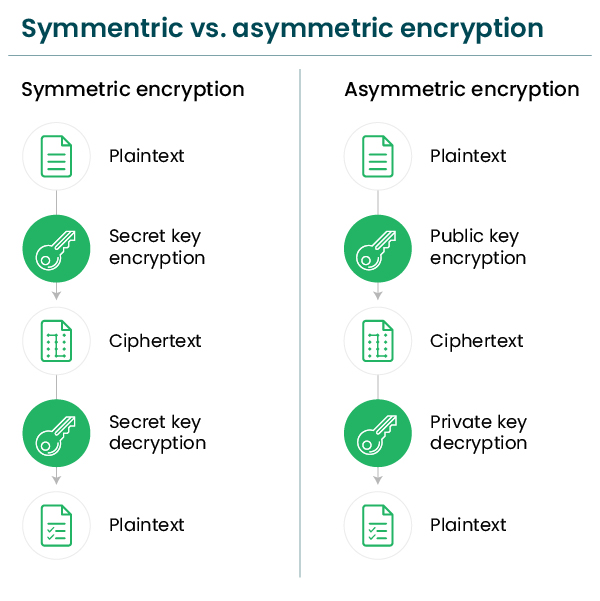
At the core of cryptography lies the concept of keys, which serve as the locks and keys of the digital realm. Key length, measured in bits, can be regarded as the robustness of these locks. A short key might open a flimsy door, while a long key secures a heavily fortified vault. The simplest encryption techniques often employ symmetric key algorithms where the same key is used for both encrypting and decrypting a message. This method can be likened to having a single, unchangeable key to access both your front and back doors.
However, the inquiry here delves deeper into asymmetric encryption, where differing key lengths might play a crucial role. In this scenario, the process involves a pair of keys: a public key for encryption and a private key for decryption. Think of this as employing two distinctly sized keys for two different doors; thus, every adjustment in size brings forth distinct ramifications.
To illustrate, let’s consider the role of key length through the lens of security and efficiency. A longer key length exponentially increases the complexity inherent in data encryption, analogous to hiring a team of experienced locksmiths to devise an intricate locking mechanism. This escalation in security, however, does not come without trade-offs. Longer keys necessitate more computational resources, potentially causing delays akin to hiring an entire crew to unlock a simple door when a single, smaller key would suffice. As the balance between speed and security becomes precarious, an ideal key length must be determined based on the sensitivity of the data.
So, can encryption and decryption operate with different key lengths? The pendulum of possibility swings between the realms of symmetric and asymmetric encryption, whereby the definitions of key lengths take on new significance. In symmetric encryption, one must adhere to the rigidity of uniformity—both operations require identical keys. Conversely, asymmetric encryption offers a duality where different key lengths might engage in a sophisticated tango; however, they must be appropriately designed and executed to intertwine without discord.
In asymmetric encryption, each key serves a distinct purpose. The public key dynamically ties together broad swathes of users, allowing anyone to encrypt data while maintaining the confidentiality inherent in its creator’s private key. This method can be visualized as an expansive garden: the broad, vibrant public spaces invite shared exploration, yet only the gardener possesses the key to unlock the inner sanctum. Herein lies the genius of asymmetric encryption—one can, in theory, choose to implement varying lengths of keys for encryption and decryption, yet with each choice comes a matrix of mathematical challenges and security implications.
Pragmatically speaking, utilizing different lengths can introduce complexities that may render the relationship between encrypted data and its decryption less than straightforward. Picture a meticulously crafted secret letter, imprinted with an intricate symphony of characters; should the keys differ dramatically in size, the decrypted message may become garbled, akin to attempting to decipher a musical score where different instruments are tuned to disparate frequencies. For this reason, amalgamating key lengths demands significant expertise to ensure compatibility without compromising security.
Furthermore, the essence of key management emerges as a fundamental consideration. With longer keys, the pitfalls of key distribution become exacerbated, akin to trying to reassure a community about a single, illusive locksmith. This scenario raises pressing concerns; will every recipient have access to the correct public key, and will they understand how to utilize it properly? The confusion surrounding key lengths and compatibility often leads to the unfortunate result of data breaches, where malicious third parties exploit inadequacies in the cryptographic infrastructure.
In conclusion, while it is theoretically plausible to encrypt and decrypt data using different key lengths, the practical execution remains fraught with peril. The interconnectedness of key management, security needs, and computational efficiency creates a labyrinthine decision-making process that every cryptographer must navigate. Should one venture into the terrain of asymmetric encryption, the varying key lengths symbolize the duality of opportunity and risk—where creativity runs rampant but complexity reigns supreme. Thus, participants in the cryptographic conversation must remain vigilant, as the robust guardians of digital communications. Recognizing the integral relationship between key lengths and their implications may prove paramount in forging a secure digital future.







Leave a Comment