In an era marked by unprecedented digital transformation, the specter of cyber threats looms large, casting shadows over both individual privacy and organizational integrity. As the frequency and sophistication of cyber-attacks burgeon, the question arises: can encryption truly outsmart hackers? This inquiry necessitates a comprehensive examination of cyber defenses, the role of encryption, and the methodologies employed by malicious actors.
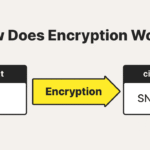
Encryption, at its core, is the art of converting text into a coded format, rendering the information unintelligible to unauthorized entities. It serves as a formidable bulwark against eavesdropping and data breaches. However, is it sufficient to safeguard our digital domains? A deeper analysis reveals that while encryption is a pivotal element in the hierarchy of security measures, it is not a panacea. Understanding its limitations reveals the complexities of the digital landscape.
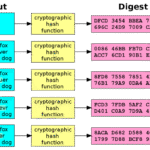
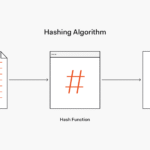
To appreciate the efficacy of encryption, one must delve into its operational mechanics. There are generally two forms: symmetric and asymmetric encryption. Symmetric encryption utilizes a single key for both encryption and decryption, thus requiring secure key distribution channels. Conversely, asymmetric encryption employs a pair of keys—a public key, known to all, and a private key, safeguarded by the owner. The cryptographic algorithms underpinning these processes, such as AES (Advanced Encryption Standard) or RSA (Rivest–Shamir–Adleman), are instrumental in establishing secure communication channels.
Yet, despite the mathematical intricacies, the security offered by encryption is predicated upon several variables. The strength of the encryption algorithm, the length of the key, and the practices surrounding key management all play crucial roles. Hackers perpetually seek vulnerabilities, employing varying strategies like brute-force attacks, where they methodically attempt every possible key until the correct one is discerned. Consequently, the longevity of encryption relies on maintaining key secrecy and deploying robust algorithms resistant to cryptanalytic attacks.
Nevertheless, encryption is not impervious to compromise. Historical instances illustrate that, under certain conditions, encryption can be circumvented. One particularly illustrative example is the use of encryption keys that remain dormant until activated by the rightful user. If a hacker gains access to a system before encryption is applied—during a device’s initial boot process or in transit—the conundrum of data integrity arises. In such scenarios, while encryption fortifies data at rest and in transit, it can be rendered impotent against pre-emptive attacks.
This compels a broader examination of cyber defense strategies. Encryption should be viewed as one cog in a more complex machine—an integrated defense strategy. The concept of defense in depth advocates layering multiple security measures. Firewalls, intrusion detection systems (IDS), and anti-malware solutions form the first line of defense. These systems can detect anomalies and provide alert mechanisms, crucial in thwarting attacks before they reach sensitive areas needing encryption.
Furthermore, the human element must not be overlooked. Social engineering remains a prevalent method hackers employ to breach security layers, often bypassing encryption entirely. Human gullibility renders even the most robust encryption vulnerable. Phishing attacks, where hackers deceive users into divulging sensitive information, illustrate that no amount of encryption can substitute for user vigilance. Comprehensive training and awareness programs are fundamental in augmenting security protocols and fortifying the human firewall.
In addition to enhancing human awareness, organizations must adopt a culture of regular updates and patch management. Software vulnerabilities can create chinks in the armor of encryption, allowing adversaries to exploit weaknesses. Continuous monitoring and an agile approach to updates ensure that organizations remain resilient against evolving threats, adapting their defenses in sync with newly discovered vulnerabilities.
Moreover, consider the burgeoning field of quantum computing. As capabilities expand, the very foundations of traditional cryptographic security may be challenged. Quantum algorithms, once fully realized, could potentially crack encryption methods that currently safeguard sensitive information. The prospect of quantum hacking necessitates a proactive stance in adopting quantum-resistant algorithms before the technology becomes mainstream.
Ultimately, while encryption undoubtedly provides a vital layer of security, it must be buttressed by a comprehensive strategy encompassing technological, procedural, and human-centric defenses. Each layer enhances overall resilience, creating a more formidable barrier against potential breaches.
In conclusion, the intersection of encryption and the evolving cyber threat landscape calls for a nuanced understanding. Encryption alone cannot outsmart hackers; it is the amalgamation of strategies, awareness, and continual evolution that affords robust defenses against cyber threats. As the digital realm continues to expand, fostering a mindset committed to vigilant and proactive cybersecurity practices will be crucial. Future-focused organizations that recognize the multifaceted nature of cyber defense will be best positioned to navigate the complexities of the digital age, ensuring both security and trust. In this ever-present battle of wits, curiosity and adaptability may indeed prove to be the most potent tools in outsmarting hackers.






Leave a Comment