AES, or Advanced Encryption Standard, stands as a formidable bastion in the realm of cryptography, safeguarding sensitive information across the globe. Its widespread adoption in securing data transmission underscores its efficacy, yet the mechanics of encryption and decryption often incite questions, particularly regarding the relationship between AES and public key cryptography. This inquiry leads us directly to the crux of the matter: Can AES be decrypted using a public key? The definitive answer is no, and understanding the rationale behind this conclusion warrants a deeper exploration into the principles of encryption methodologies and the distinct natures of symmetric and asymmetric cryptography.
To unravel this enigma, one must first appreciate the foundational tenets of symmetric encryption algorithms like AES. In symmetric encryption, a single key serves dual purposes: it encrypts and subsequently decrypts the data. This singularity necessitates stringent security measures in key distribution, as the loss or compromise of the key undermines the entire cryptographic framework. AES is predicated on complex mathematical operations and transformations, ensuring that even a modicum of variation in the input or key produces drastically different outputs, enhancing its resilience against brute-force attacks.
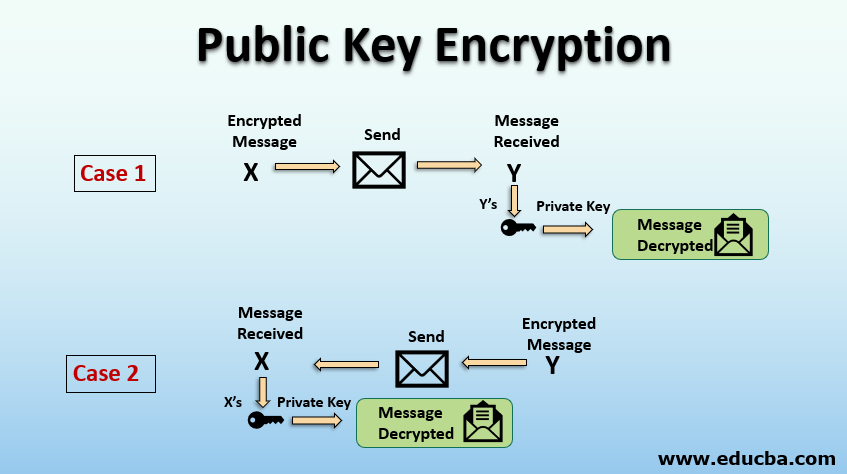
In stark contrast, public key cryptography, or asymmetric cryptography, employs a pair of keys: one public and one private. The public key is disseminated widely to encrypt messages, while the private key remains confidential, used solely for decryption. The beauty of this system lies in its inherent efficiency for secure communications, facilitating the safe exchange of keys or messages without needing a pre-established confidential channel between parties.
In essence, AES, being a symmetric encryption algorithm, diverges fundamentally from the operations of public key cryptography. Therefore, the mechanics of a public key system cannot be applied to decrypt AES-encrypted data. Let’s delve deeper into this assertion, highlighting key elements that substantiate this distinction.
First and foremost, the algorithmic structures of AES and public key systems differ significantly. AES is a block cipher that processes fixed-size blocks of data—128 bits in the case of AES—with key lengths of 128, 192, or 256 bits. The security of AES lies in its robust substitution-permutation network: an intricate dance of substitution boxes (S-boxes) and permutation operations that obfuscate the relationship between plaintext and ciphertext. This complexity ensures that ciphertext produced by AES cannot be deciphered without the corresponding secret key.
On the other hand, public key cryptographic systems such as RSA or ECC (Elliptic Curve Cryptography) are based on mathematical constructs involving prime factorization or elliptic curves. This fundamentally different architecture results in varied decryption protocols, none of which are applicable to AES. The public key serves solely for encrypting information that only the corresponding private key can decrypt, a process antithetical to AES’s symmetric plaintext-ciphertext relationship.
Moreover, the security implications of key management further elucidate why AES cannot be decrypted using a public key. In a public key system, the security of the relationship between the public and private keys is predicated upon computational difficulties—such as the challenge of factoring large numbers or solving discrete logarithm problems. These are computationally intensive tasks that bolster the security of the asymmetric system. However, AES relies on the secrecy and protection of a singular symmetric key. Flaws in handling, sharing, or storing symmetric keys could entail devastating consequences for data integrity.
Addressing the practical applications, it is worth noting that while AES itself cannot be directly decrypted with a public key, public key systems can complement AES. Strikingly, hybrid cryptographic schemes leverage the strengths of both symmetric and asymmetric methods. In a common scenario, data is encrypted using AES, while the AES key is encrypted using a public key algorithm. This dual-layer approach provides the expediency of symmetric encryption while also benefitting from the secure key exchange mechanisms of public key systems.
Finally, the implications of understanding why AES cannot be decrypted with a public key extend beyond theoretical musings. It fosters an appreciation for cryptographic integrity in data security practices across various industries, from banking to healthcare. Acknowledging the limitations and strengths inherent to these systems cultivates a more nuanced perception of the cryptographic landscape, shedding light on its complexity.
Ultimately, grappling with the question of whether AES can be decrypted using a public key not only leads to the pronounced conclusion that it cannot but also encourages a broader contemplation of encryption principles. It challenges conventional understandings, beckoning stakeholders to recognize the sophisticated interplay between security and functionality. As technology evolves and new cryptographic standards emerge, the importance of safeguarding information persists, making the comprehension of these concepts not just beneficial but essential in our increasingly digital world.







Leave a Comment