In an age dominated by technology, the concept of security in mobile applications has metamorphosed into a fundamental pillar upon which trust is established. Behind every secure app lies a labyrinth of intricate algorithms designed not just for efficiency, but primarily for safeguarding sensitive information. This article delves into the various aspects of secure application algorithms, providing insight into their underlying mechanisms and the myriad of techniques employed to ensure user safety.
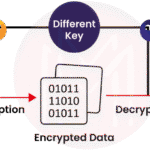
The first line of defense in any secure app is encryption. Encryption algorithms translate data into a coded format, requiring a specific key for decryption. One prevalent encryption standard is the Advanced Encryption Standard (AES), which has become the gold standard for data protection. AES utilizes block ciphers that systematically transform plaintext into ciphertext, making it virtually impenetrable without the decryption key. Both symmetric and asymmetric encryption methods play critical roles in various scenarios, offering flexibility based on the requirements of the application.
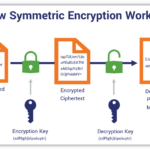
Symmetric encryption utilizes the same key for both encryption and decryption, thus demanding a secure method of key exchange. Conversely, asymmetric encryption employs a pair of keys—one public and one private. This forms the crux of modern secure communications, enabling functionalities such as secure email and online transactions. Notably, the RSA algorithm stands out for its robustness, using complex mathematical computations to protect information, instilling confidence in users.
Another pivotal aspect is authentication. Ensuring that users are who they claim to be is paramount in curbing unauthorized access. Multi-factor authentication (MFA) has emerged as an indispensable security layer. By requiring users to provide two or more verification factors—such as a password combined with a fingerprint or a one-time code sent via SMS—MFA adds an extra barrier against potential intruders. The cryptographic protocols underlying these systems, such as Time-based One-Time Password (TOTP), are specifically designed to generate securely timed entries that enhance overall security.
Furthermore, secure apps are fortified through hashing techniques. Hashing is a one-way function that transforms sensitive information, like passwords, into a fixed-length string of characters. Consequently, even if the data is intercepted, reconstituting the original information becomes an insurmountable challenge. Algorithms such as SHA-256 are frequently employed, offering a secure means of data integrity verification. In addition, salted hashes add an additional layer of protection, as they incorporate random data into the hash function, thwarting pre-computed attacks.
The role of secure coding practices cannot be overstated. Developers must adhere to rigorous guidelines when crafting algorithms for mobile applications. Implementing principles such as input validation, output encoding, and error handling serves to mitigate vulnerabilities that could be exploited by nefarious actors. For instance, employing parameterized queries can significantly reduce the risk of SQL injection attacks, while comprehensive error logging assists in identifying potential breaches in real-time.
Equally significant is the importance of regular security audits and testing. Continuous evaluation of algorithms and their implementation in an application helps identify weaknesses before they can be exploited. Static and dynamic analysis tools can be utilized to examine code, uncovering vulnerabilities that may otherwise remain hidden. Additionally, penetration testing simulates potential cyberattacks, allowing organizations to fortify their defenses preemptively.
As we plunge further into the realm of machine learning (ML) and artificial intelligence (AI), their application in secure app development is becoming increasingly pronounced. Machine learning algorithms can analyze user behavior patterns, enabling the identification of anomalies that may indicate security breaches. For instance, if an application detects that a user is attempting to log in from an unfamiliar location or device, it can trigger additional verification processes, safeguarding sensitive information.
Data integrity is yet another critical tenet of secure applications. Employing algorithms that ensure consistent data accuracy and validity is vital. Techniques such as checksums and digital signatures are routinely used to verify that data has not been altered during transmission. Digital signatures, in particular, provide irrefutable proof of authenticity, allowing users to confirm the legitimacy of the source.
The embrace of blockchain technology has also illuminated new pathways for securing applications. By decentralizing data storage across numerous nodes, blockchain enhances security by eliminating single points of failure. Additionally, each transaction is time-stamped and linked to previous transactions, creating an immutable record that significantly increases transparency and trust. This technology has found applications beyond cryptocurrencies, extending into logistics and smart contracts due to its secure nature.
Coloring the landscape of secure applications is the often-overlooked aspect of user education. Users play a pivotal role in the overarching security framework. Educating them about the importance of robust passwords, the significance of regularly updating software, and the dangers associated with public Wi-Fi networks empowers individuals to take an active role in their digital security. Notably, security awareness training initiatives serve to bridge the knowledge gap, fostering a culture of vigilance.
In conclusion, the algorithms that underpin secure applications are as multifaceted as the threats they seek to counter. From encryption and authentication to hashing and secure coding practices, each element collaborates harmoniously within a broader framework designed to protect user data. As technology continues to evolve, so too must the strategies employed to secure mobile apps. Embracing advanced algorithms, leveraging innovative techniques such as machine learning, and fostering a culture of security awareness will collectively fortify the integrity of mobile applications and ensure a safer digital landscape. In a world that increasingly relies on technology, building trust through unwavering security measures is not just an option—it is a necessity.






Leave a Comment